New Mirai Botnet Variant Exploits RCE Flaw CVE-2024-3721 in TBK DVR Devices
- A recently disclosed vulnerability in TBK DVR devices is currently exploited through malicious POST requests.
- A new Mirai variant uses shell commands embedded in HTTP requests to execute ARM32 binaries on vulnerable devices.
- The attack showcases anti-VM techniques, anti-emulation checks, and RC4 encryption.
A new variant of the infamous Mirai botnet is targeting DVR devices using the recently disclosed vulnerability CVE-2024-3721. The variant exploits a critical flaw in TBK DVR systems, enabling remote code execution (RCE) through embedded Linux commands within GET or POST requests.
The attack leverages a simple shell command embedded in HTTP requests to execute ARM32 binaries on vulnerable devices, according to a report by Kaspersky researchers.
Telemetry indicates that the majority of infections have been detected in countries such as China, India, and Egypt. Over 50,000 exposed DVR devices have been identified, presenting a significant attack surface for cybercriminals.
Unlike typical botnet infections, this Mirai variant bypasses the architecture detection stage, as DVR systems primarily support ARM32. This targeted approach streamlines the infection process, making it faster and more efficient.
The key features of the Mirai variant are RC4 data encryption, anti-VM techniques, and anti-emulation verification.
The malware employs RC4 encryption to obscure command strings, enhancing its ability to evade detection. The encrypted data is then stored in a custom global structure for retrieval during operations.
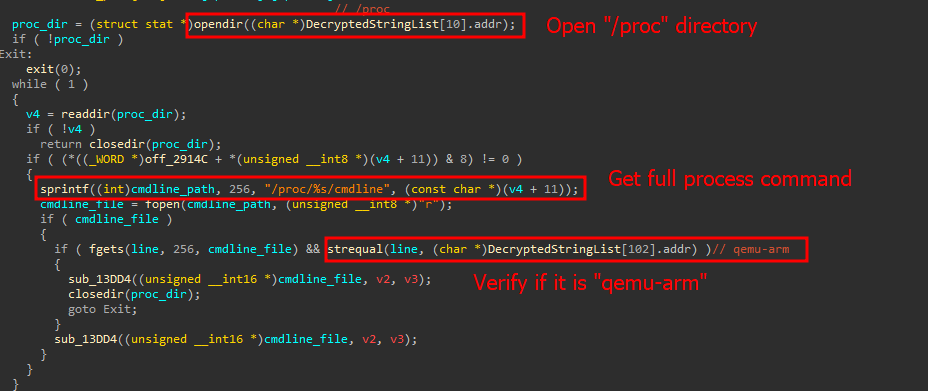
This variant detects if it is running in a virtualized environment by scanning processes for indicators of VMware or QEMU, further complicating analysis by security experts.
The malware verifies if it is operating within expected directories, introducing additional barriers to reverse engineering.
The latest reported attack was a near-record distributed denial-of-service (DDoS) attack that struck KrebsOnSecurity last month.