New Malware LOSTKEYS Targets Western Entities and NGOs in ClickFix Campaign, Google Reports
- A new malware campaign relies on social engineering via fake CAPTCHA and a ClickFix lure.
- The multi-stage delivery system of LOSTKEYS marks a continuation of COLDRIVER’s targeted intelligence collection activities.
- The malware showcases anti-VM measures and downloads a VBS decoder with the payload.
A new strain of malware, dubbed LOSTKEYS, is linked to the Russian government-backed hacking group COLDRIVER (also known as UNC4057, Star Blizzard, or Callisto). It can steal files from predefined directories and extensions, sending system details and active processes back to its operator.
Best known for credential phishing attacks against high-value targets such as NATO governments, NGOs, and former intelligence officers, COLDRIVER (tracked closely by GTIG for years) continues to diversify its attack methods, Google’s Threat Intelligence Group (GTIG) has uncovered.
Traditionally, the group focuses on credential theft to exfiltrate emails, contact lists, or sensitive data, but malware deployment has now become a more pronounced aspect of its operations. LOSTKEYS was observed in attacks throughout January, March, and April 2025.
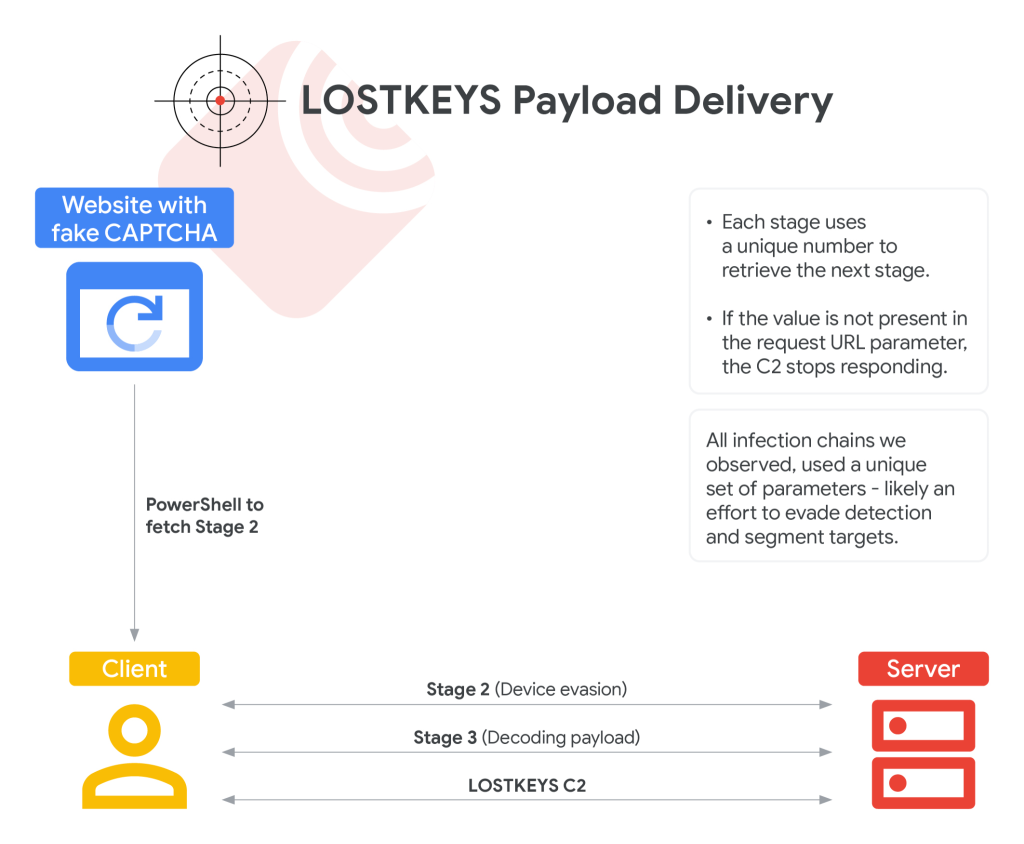
The attack begins by luring victims to a malicious website with a fake CAPTCHA. Once the target “verifies” the CAPTCHA, they are encouraged to copy and execute malicious PowerShell code directly into their system via the Windows “Run” prompt.
This method, notably referred to as ClickFix, has been seen in campaigns from other advanced persistent threat (APT) actors and relies heavily on social engineering for execution.
The second stage retrieves additional code if the affected system does not match specific display resolution hashes, likely a mechanism to evade analysis in virtual machine (VM) environments. This step ensures only valid targets proceed to the next stage.
The final stage involves downloading and decoding Base64-encoded files. These include a Visual Basic Script (VBS) decoder alongside the malware’s payload. LOSTKEYS uses unique encryption keys for each infected device, adding another layer of complexity to the attack chain.
The resulting VBS payload runs on the victim machine, enabling data exfiltration and reconnaissance activities.
GTIG assesses that COLDRIVER’s activities support Russia’s strategic intelligence goals. The group primarily targets individuals with connections to Western governments, military advisors, think tanks, NGOs, and high-profile entities involved with Ukraine.
Notably, COLDRIVER has been linked to hack-and-leak operations, including campaigns aimed at UK officials and NGOs. These operations aim to disrupt or discredit adversarial governments and organizations, aligning with Russian geopolitical interests.