A New Iteration of the GlitchPOS Malware is on Sale on Crimeware Forums
- The popularity of PoS malware tools that steal credit card information from terminals is on the rise again.
- Researchers notice that crimeware forums are selling new iterations of previously popular malware tools.
- The authors tout the user-friendliness and simplicity of their tools, while the cost of acquisition is substantial.
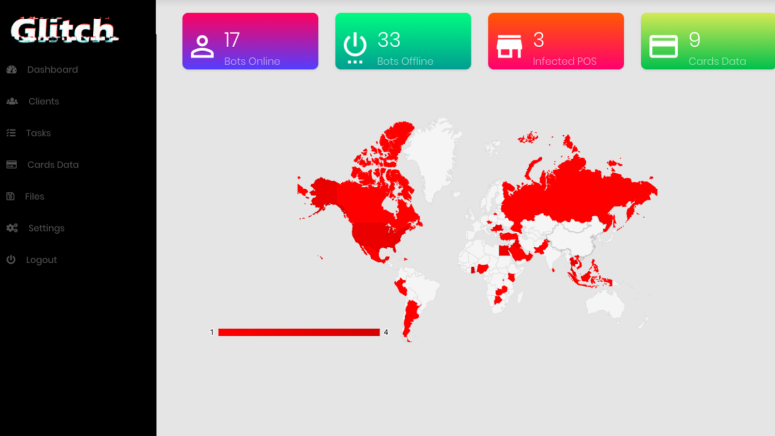
Three Talos Intelligence researchers have noticed a new PoS (point of sale) malware that targets people’s credit card and payment information details. The actor who is behind this malware though is not a newcomer in the field, but rather an adept hacker who has previously offered two similar tools known as “GlitchPOS” and “DiamondFox”. PoS payment terminals are still not treated with the appropriate level of caution, as both the shop owners and the clients maintain a false sense of security that supposedly underpins them.
This is precisely what makes PoS systems such as lucrative targets, with attackers planting them on the websites of retailers, and starting a chain of infection from there. Moreover, and since all other ways of acquiring valuable data from people get increasingly harder, attackers are shifting their attention back to “classic” fields like the PoS. Only a couple of weeks back, we saw how 6500 shops in the US have had their customer payment data stolen by malicious actors, after the infrastructure of the PoS systems provider “North County Business Products” was compromised.
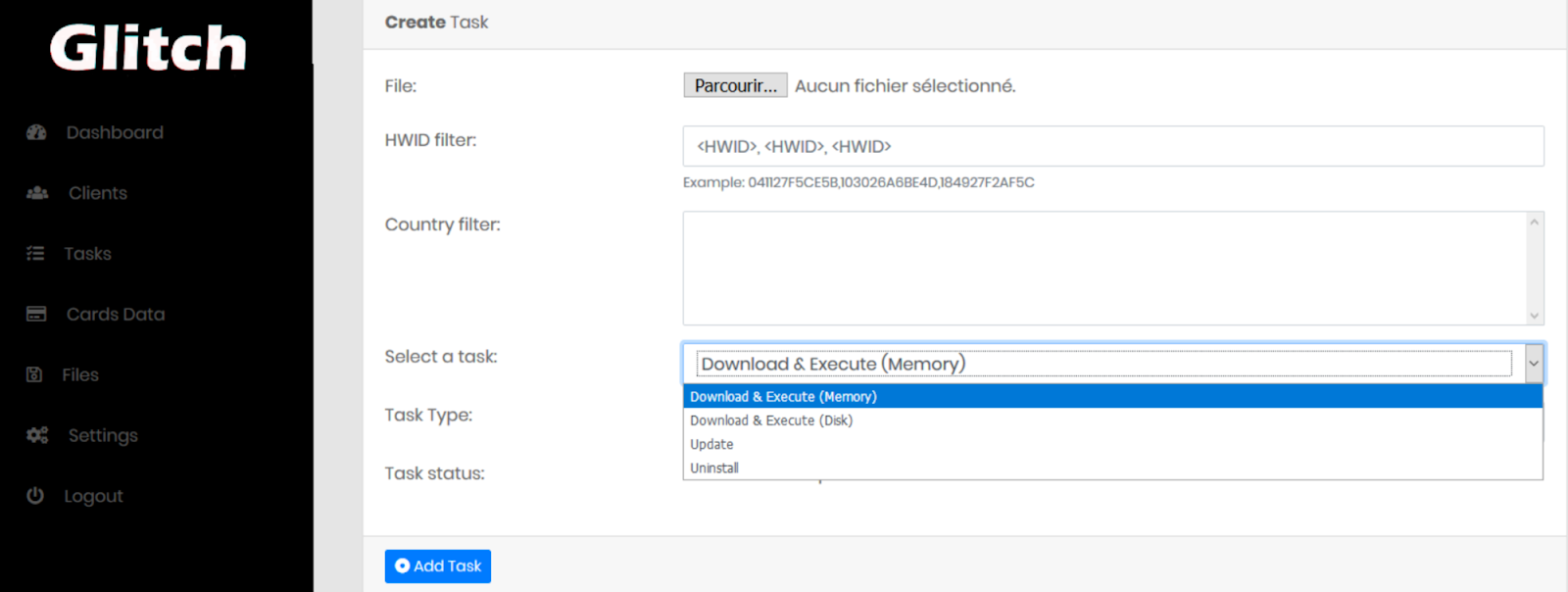
The creator of this new iteration of the GlitchPOS is advertising his/her product as an “easy to use yet powerful” one. The commands to the malware are sent by the C2 server, and can be one of the following:
- Register the infected systems
- Receive tasks (command execution in memory or on disk)
- Exfiltrate credit card numbers from the memory of the infected system
- Update the exclusion list of scanned processes
- Update the "encryption" key
- Update the User Agent
- Clean itself
source: blog.talosintelligence.com
The communication is encrypted with base64, while the malware itself hides behind a fake game with cat pictures, developed in VisualBasic. However, in reality, it is an encoded memory grabbing malware. The main stealing target is the credit card number that is stored in the compromised terminal through a series of regular expressions. Once the card holder, card number, and expiration date data are exfiltrated, they are beamed to the C2 server. The creator has even produced a demonstration video that shows how simple it is to do the job with GlitchPOS. It’s a business after all, as the malware tool costs $250, the builder another $600, while the gate address change sets attackers back $80.
Talos researchers have noticed that the new GlitchPOS differs from earlier tools published by the same creator, as no leaked code has been used for the implementation of the credit card grabbing action. This time, the author developed his/her own code, as leaked code is known, and can be negated. Another thing that they noticed is that a couple of devious members of these shady crimeware forums have bundled the POS malware as their own, and tried to sell it for an even higher price. Deceptors trying to trick fraudsters is nothing short of the crookedness that one would naturally expect in these places.
Do you prefer paying in cash, or do you blindly trust PoS systems all the time? Share your thoughts in the comments section beneath, and don’t forget to like and subscribe to our socials, on Facebook and Twitter.