New Email Campaign From ‘NOBELIUM’ Indicates the Actor’s Development
- ‘NOBELIUM’ is delivering malicious emails to American companies en masse, pretending to be from USAID.
- Most of these are being blocked and marked as spam, but some find their way in corporate networks.
- This is another indication that state-supported actors aren’t willing to pause their espionage operations.
Microsoft has managed to uncover a wide-scale email campaign launched and operated by ‘NOBELIUM,’ the same group of actors who are considered responsible for the supply-chain attacks against users of the SolarWinds Orion. According to Microsoft’s threat intelligence team, the particular email campaign appears to have started in January 2021 and has signs of rampant experimentation that lasted until May 25, 2021. At that date, NOBELIUM leveraged the mass-mailing service ‘Constant Contact’ to scale up the operation and send out large numbers of emails masquerading as a U.S.-based development organization.
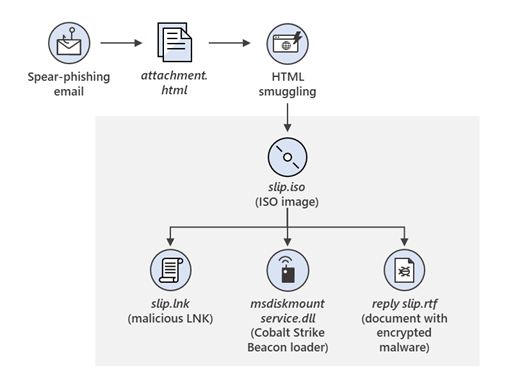
The targeting scope of the attack includes approximately 3,000 accounts across 150 companies and organizations operating in a variety of sectors. The emails carry an HTML file as an attachment, and if the recipient opens that, a JavaScript snippet runs to mount an ISO file as an external or network drive on the machine. In there, an LNK file executes a DLL which launches the Cobalt Strike beacon on the compromised computer.
The mass-scale distribution achieved through ‘Constant Contact’ caused some trouble to NOBELIUM, as the high volumes of incoming mail triggered automated systems that blocked the messages and marked them as spam. However, as Microsoft warns, this doesn’t mean everything was prevented from being delivered.
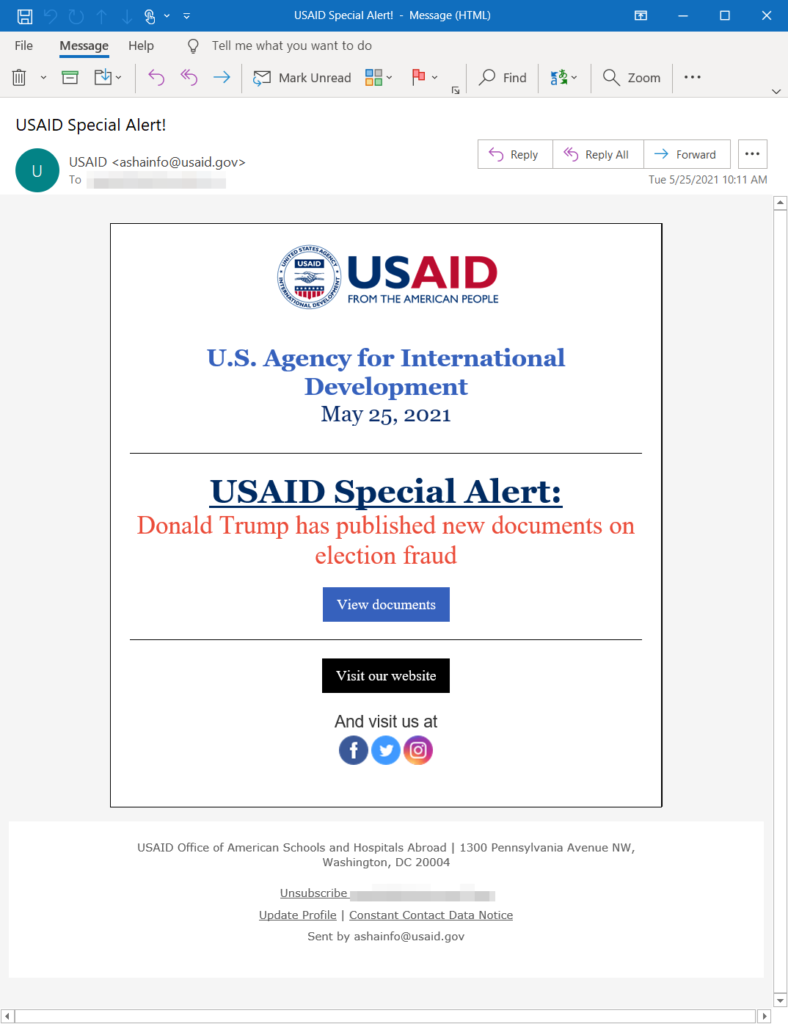
The latest organization mimicked by the actors is USAID (U.S. Agency for International Development). The messages are presented as alerts about former U.S. President Donald Trump publishing new documents that prove the election fraud claims that shook the country at the start of the year. Of course, the actors could change their spear-phishing theme any time, especially now that this particular one has been unmasked.
For Microsoft, there are three reasons why this campaign is notable:
- NOBELIUM continues to seek a way in important organizations that would open the door to massive espionage operations, exactly like they did with SolarWinds.
- This time, the actors appear to be targeting many humanitarian and human rights organizations too, which were previously excluded or ignored.
- Nation-state attacks aren’t showing any signs of slowing no matter the skirmishes between country leaders and the imposition of sanctions for this exact reason.
It is important to note that this campaign is still pretty much active, so checking the indicators of compromise given at the bottom of Microsoft’s analysis could help save you from great troubles. As always, you are advised to enable MFA on all accounts, turn on cloud-delivered protection, and run EDR in block mode.