New CountLoader Malware Linked to Major Ransomware Gangs LockBit, BlackBasta, and Qilin
- Loader associations: A novel malware loader is strongly associated with Russian ransomware gangs LockBit, BlackBasta, and Qilin.
- Its role: The .NET, PowerShell, and JScript loader is used as an Initial Access Broker (IAB) in ransomware attacks.
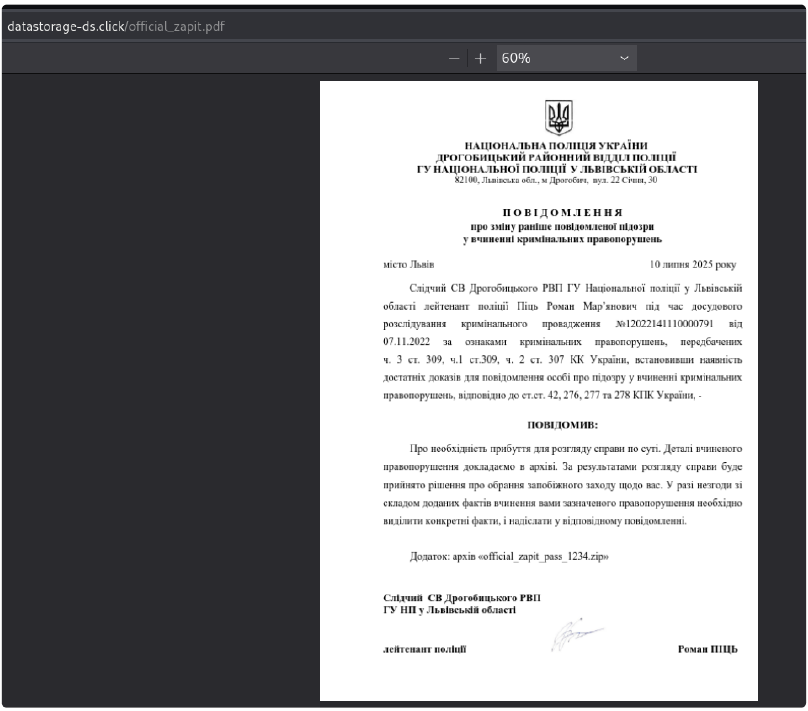
- Recent campaign: It was recently used in a campaign targeting Ukraine with a PDF-based phishing lure impersonating the Ukrainian police.
Security researchers have discovered a new malware loader, dubbed "CountLoader," which is strongly associated with prominent Russian ransomware groups. The loader, which has been observed in three distinct versions—.NET, PowerShell, and JScript—is being leveraged as an Initial Access Broker (IAB) in high-stakes ransomware attacks.
CountLoader Malware Analysis
CountLoader is an evolving threat designed to deploy secondary payloads, making it a crucial component in the attack chain. Silent Push analysis reveals the malware is apparently used by major ransomware groups, including LockBit, Black Basta, and Qilin, to gain initial entry into target networks.
Its different versions exhibit varying levels of sophistication. The JScript variant is the most complex, featuring six different methods for downloading files and functionality to collect detailed system information from victims.
A recent campaign utilizing CountLoader involved a PDF-based phishing lure impersonating the Ukrainian police to target individuals in Ukraine. This strengthens the suspected ties to Russian-speaking threat actors.
The loader's command and control (C2) communication pattern is unique, and its code includes advanced features like multi-layered download attempts using LOLBins such as "certutil" and "bitsadmin."
Role in Ransomware Attacks
The connection to ransomware operations is a critical piece of cybersecurity threat intelligence. By analyzing Cobalt Strike samples delivered by CountLoader, researchers linked the malware's C2 infrastructure to watermarks previously associated with BlackBasta and Qilin ransomware incidents.
The loader frequently stages its payloads in the victim's "Music" folder, a TTP that aligns with past LockBit campaigns.
The discovery of CountLoader provides defenders with new indicators to hunt for, as it signifies the initial stage of potentially devastating ransomware attacks. Organizations are urged to review security logs for signs of this new threat.