New “Bundlore” Adware Brings Back Trouble to macOS Users
- Fresh “Bundlore” versions indicate that the authors worked in making their adware pack compatible with Safari 12.
- The actors have followed the new format guidelines by Apple, exactly like any add-on developer would do.
- Users who fall victim to this malware will deal with classic adware burden and the associated signs.
When it comes to browser add-ons, you should never blindly trust anything. The markets that offer them are simply too crowded to check and confirm everything, and so there’s always some space for malicious developers to move in. Sophos reports on a new version of the “Bundlore” adware that comes with a total of seven unwanted applications, including three Safari extensions that inject ads, hijack download links, and redirect search queries to steal user clicks. Bundlore is a very common threat in the macOS ecosystem, accounting for 7% of all attacks against the platform.
The most recent versions, though, are particularly interesting because the authors of the malware have demonstrated their capacity to adjust to the latest format changes that Apple applied on the Safari and the browser extensions in particular (change to “.appex” format). Bundlore was quick to adapt to these shifts and push new versions of the adware that are compatible with the latest Safari versions. The rest of the functionality remains basically the same, with fake clicks on affiliate advertisements generating money for the Bundlore authors. However, that is not to say that this bundleware does not constitute a risk of personal data exfiltration, or a channel through which users can be siphoned to malvertising domains.
Source: Sophos
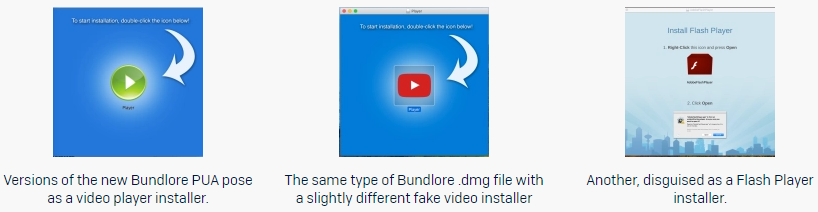
During analysis, the Sophos researchers found that the signature used by the adware had been reported, so it was blocked from running. The developers will not give up because of this, though, as they’ll change to using a different signature, will create new developer accounts, and even try out different installation tactics. Some of the tactics used are to disguise the installers and payloads as video player apps or Flash Player packs. Other methods include chains of bash shell scripts that decrypt obfuscated code, or the creation of temporary directories to drop installers and fetch additional payloads from there.
Source: Sophos
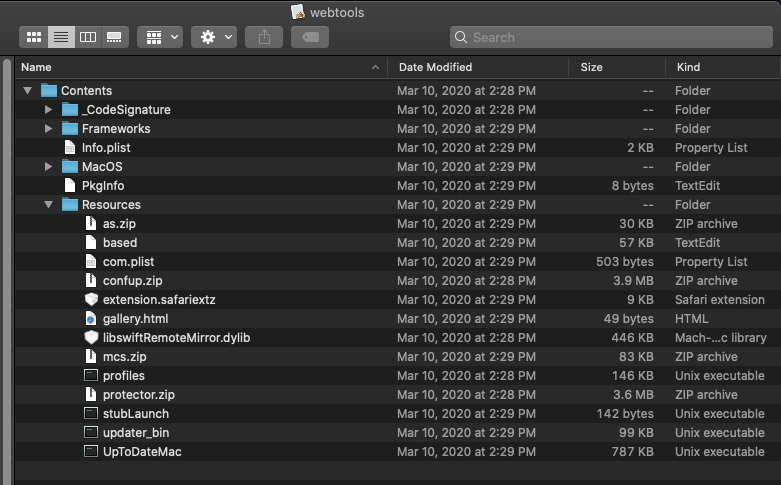
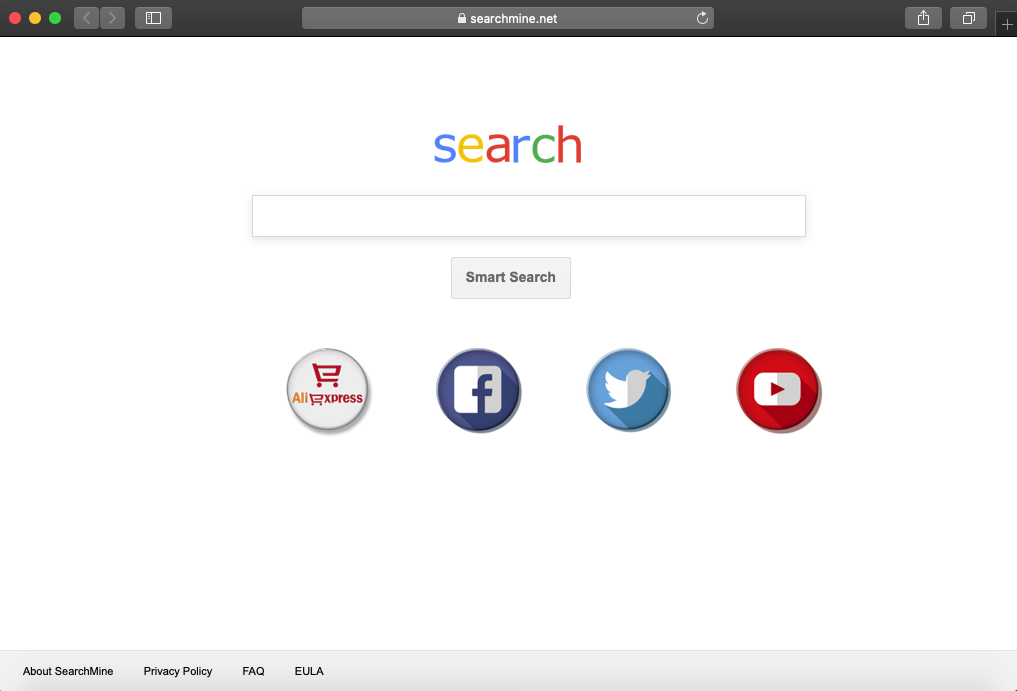
Right now, the actors are using the name “webtools.app” for the installer of the bundleware, while the Safari extension that is dropped is “extension.safariextz.” You can find the full list of the unwanted files in the above screenshot. One clear sign that things went wrong would be to see your Safari home page changing to “searchmine[.]net.” Other, less apparent signs of fraud are the chains of redirections that lead to Bing search results, the appearance of a “MyCouponSmart” extension, and numerous ad injection events that occur on all websites.
Source: Sophos