A New Android Banking Trojan Named “EventBot” Has Emerged
- A grave threat has appeared on the Android landscape, featuring advanced keylogging abilities.
- Called the “EventBot,” the trojan already supports a wide spectrum of e-banking and payment apps.
- The actors behind it are unknown, and so far, they are limited to working on its development rather than renting it to others.
There’s a new banking trojan that is roaming the Android space, called “EventBot.” The discovery and report come from the Cybereason Nocturnus team, and they define the date of the new malware’s first appearance to be around March 2020. EventBot is a powerful banking trojan and info-stealer that can access SMS messages to bypass two-factor authentication, steal financial data from over two hundred institutions, and also steal crypto-coins from wallets. EventBot is still under heavy and rapid development, which signifies the potential for this malware to become the next big threat in the Android ecosystem.
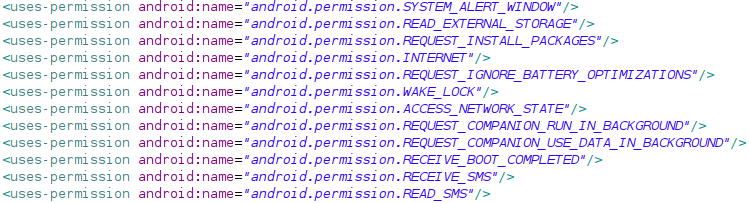
All EventBot permission requests, Source: Cybereason
“EventBot” spreads through APKs that are found in unofficial Android app stores, torrents, and other obscure sources, so it’s not on the Google Play Store yet. The malware is using fake icons to masquerade real applications such as MS Word, Adobe Flash, and so on. Once installed, it requests the user to grant access to the “accessibility services,” which is precisely where Pandora’s Box opens. This enables EventBot to operate as a keylogger, retrieve notifications, access content on active windows, and more. More recent versions are also asking for permission to run in the background and then delete the launcher’s icon.
Here are all of EventBot’s functions right now:
- Create windows on top of apps;
- Read data from external storage;
- Request the installation of packages;
- Open network sockets;
- Whitelist an app from battery consumption monitoring;
- Prevent the processor from sleeping;
- Access network state information;
- Request permission to run and use data in the background;
- Launch itself after system boot;
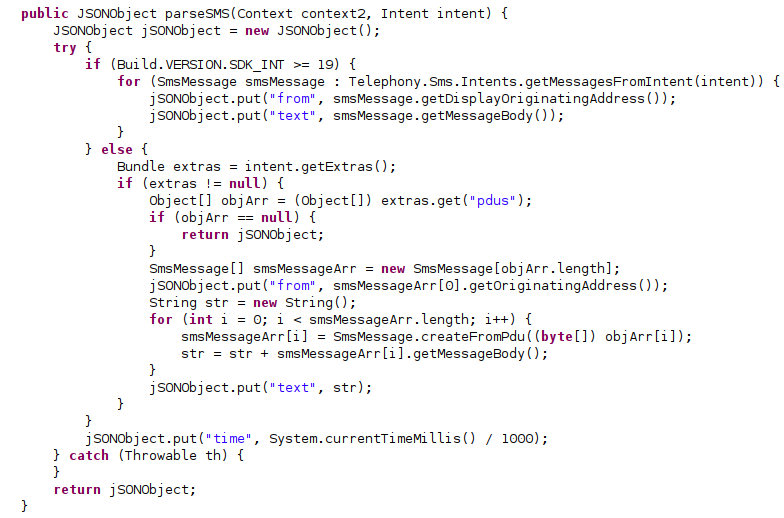
- Receive and read text messages;
- Get the full list of all installed applications;
- Get device information;
- Encrypt all exfiltrated data using Base64 and RC4.
SMS parsing, Source: Cybereason
Although EventBot is not massively deployed yet, it already covers apps such as Paypal Business, Revolut, Barclays, UniCredit, CapitalOne UK, HSBC UK, Santander UK, TransferWise, Coinbase, Paysafecard. As for what e-banking apps this malware targets, it’s a set of institutions from Italy, the UK, Spain, Switzerland, France, and Germany.
All apps targeted by EventBot, Source: Cybereason
Cybereason can speculate on the identity of the threat actors behind EventBot, but nothing can be declared with certainty right now. By analyzing the infrastructure, the researchers found a connection with Italian actors who launched several attacks in Italy last year using an Android info-stealer. With new versions of EventBot being released every couple of days, we expect this malware to become a severe problem when its authors decide to market it.