Nefilim/Nephilim Could Soon Fill the Gap Left by NEMTY’s Termination
- NEMTY closed down and passed its code to Nefilim, a new type of ransomware that’s already causing trouble.
- Nefilim is stealing data from large companies and then leaks them in pieces to apply pressure.
- So far, there has been no RaaS operation, but it’s too soon to tell if the actors are planning to launch it.
Only about three weeks ago, we reported on the closure of the NEMTY project - at least as far as its RaaS (ransomware as a service) operations are concerned. The authors of the successful strain decided to go private and hunt bigger fish, while they shared the source code of NEMTY with a selection of individuals who reportedly spewed “Nefilim.” A Sentinel Labs report tries to shed light on the new strain, how it works, what encryption protocols it uses, and how much of NEMTY does it have at its core.
Source: Sentinel Labs
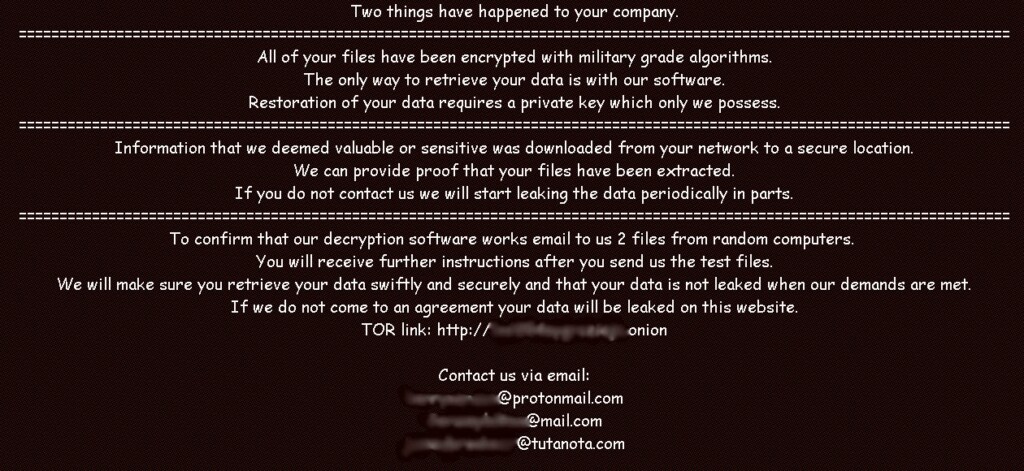
Nefilim first appeared in March 2020, and initially, it shared much of NEMTY’s code without significant changes. The primary method of delivery is through vulnerable RDP services, the encryption is done through AES-128 using an RSA-2048 key, and the extension of the encrypted files carries the name of the strain itself. The main difference from NEMTY is the lack of a RaaS operation, although this may be a matter of time. Another point of differentiation is the fact that Nefilim isn’t using a TOR-based payment portal but instead prompts its victims to reach out via email communication.
Source: Sentinel Labs
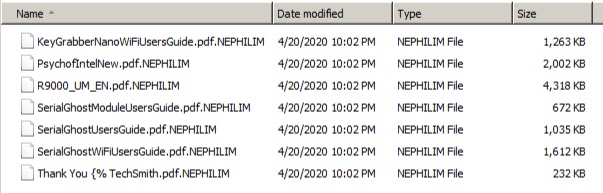
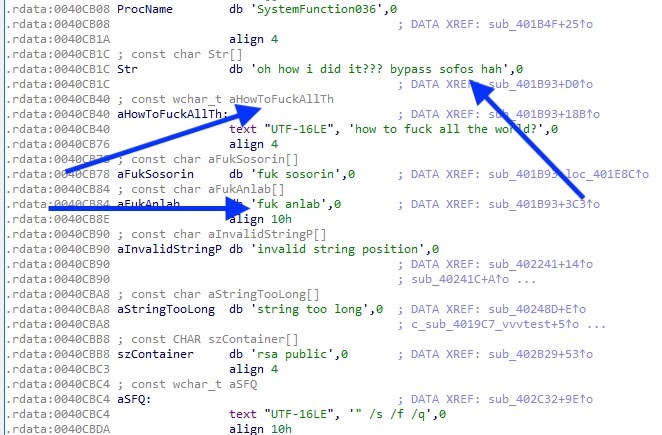
From Nefilim came Nephilim, which is almost the same ransomware strain - so technically, the researchers are treating them as a single entity. After looking deeper into the code, the analysts have found that the authors of Nephilim find enjoyment in the embedding of insulting messages aimed at well-intended researchers. Although Nefilim is so young, it has quickly grown in popularity by being one of the ransomware families that don’t only encrypt files of the infected system, but it also steals them. So far, the Nefilim group has published portions of data belonging to large oil and gas firms, as well as entities engaging in the “Engineering and Construction Services” and the “Apparel and Fashion” field.
Source: Sentinel Labs
That said, Nefilim is another data-breaching headache that can’t be dealt with backups or decrypters alone. These threats are better stopped at the entrance, so defending the network perimeter would be the best approach for prevention. Nefilim received the code of NEMTY, a powerful ransomware strain, and so it could start doing business right away. We don’t know if the group behind the new ransomware is interested in launching a RaaS platform or not, but from the first steps, it doesn’t seem like they are going for it.