Necurs Botnet Evolves to Carry New Payloads and Hide Better
- Necurs botnet is back again and on the rise, empowered by new payloads and a hiding technique.
- The botnet can communicate with its C&C server once in a while, and get the rest of the needed data through P2P.
- Researchers say they have a way to contain it, but it’s still far from being dealt with.
Necurs is a botnet that has been actively distributing Locky and other malware payloads since 2012. While the particularly botnet had its ups and downs in recent times, researchers have spotted a new and evolved version that is now harder to detect, analyze, and stop. The new Necurs botnet got better in hiding by employing interrupted “on/off” communications with its command and control server, while the payload repertoire has been expanded to include DDoS tools, crypto mining snippets, banking trojans, and powerful ransomware. The new version has already spread to over 570k systems around the globe, so it is one of the most severe botnet problems right now.
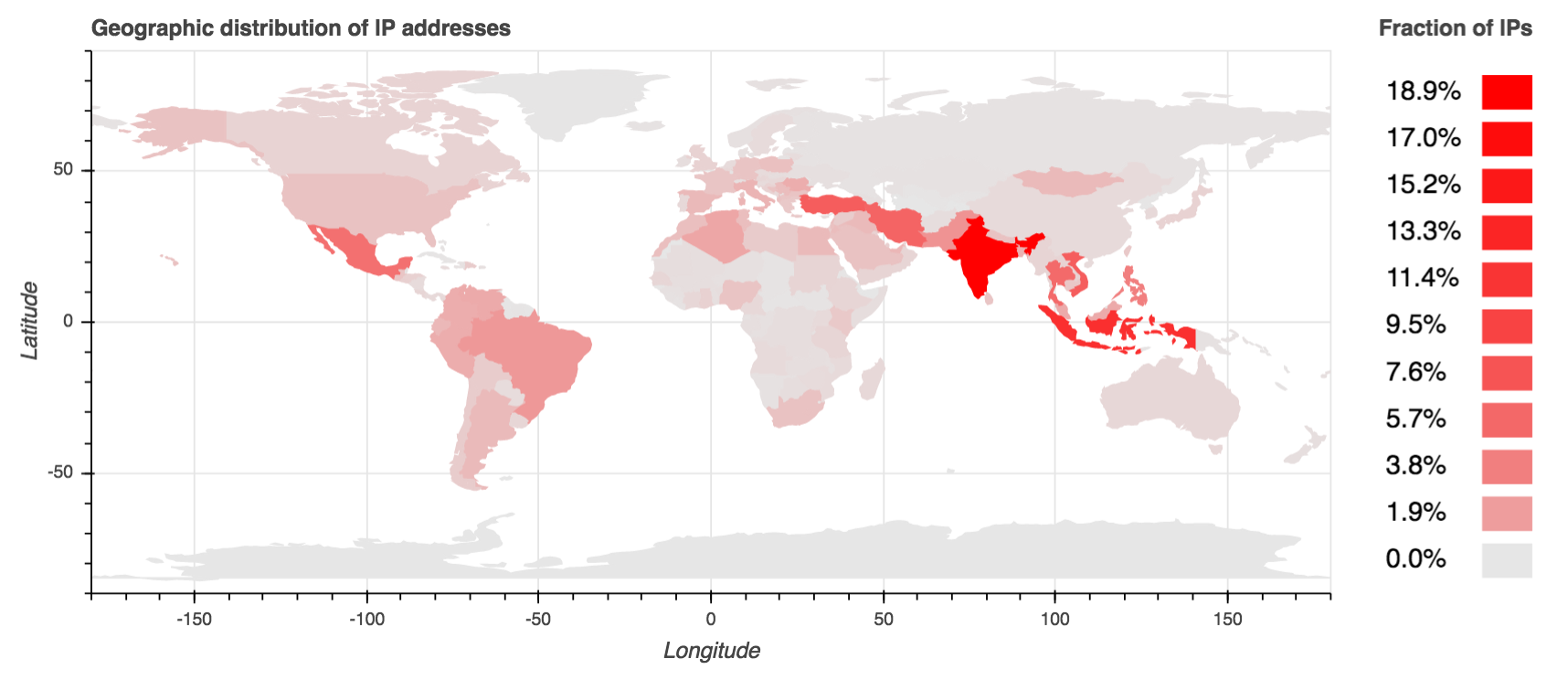
According to McAfee Labs, who have been monitoring Necurs for a long time, the largest numbers of infections are to be found in India, Indonesia, Vietnam, Turkey, and Iran, with the infections in these countries accounting for the 50% of the total. About 16% of the Necurs bots are considered “orphaned” as they have lost their connection to the C&C server, something that has happened in 2016 on a larger scale for the particular botnet. The remaining active bots are up and running, but follow large periods of inactivity in order to avoid detection. Researchers fear that even the 16% that is seemingly dormant may wake up at some point in the future.
source: netformation.com
Currently, Necurs employs a hybrid communication approach, combining direct C2 with P2P communications. The C2 server is pushing up-to-date peer lists to the botnet, so it remains versatile and keeps its network traffic data obfuscated. If the C2 server communication is lost, the bots look for new instructions through the P2P and designated DGA. According to the researchers who are monitoring and try to contain the activity of Necurs, its use of DGA is where its power and also weakness comes from. As DGA groups are known beforehand, they can be sinkholed, allowing the researchers to analyze the botnet network traffic and server infrastructure. Still, as the situation stands right now, Necurs is a botnet that keeps on evolving, and one that we should continue to monitor.
Do you see botnets like Necurs as a real threat for the internet infrastructure, or do you consider them a mere annoyance for the few? Share your thoughts in the comments section beneath, and don’t hesitate to do the same on our socials, on Facebook and Twitter.