Naikon APT Targeting Seven APAC Governments via a New Backdoor
- The Naikon APT has reappeared online, and they have refreshed their attack arsenal.
- The group is using a new backdoor named “Aria-body,” and which features similarities with their 2015 malware.
- Mainly governments in the Asia Pacific region, ministries, and public entities were among the targets of the hackers.
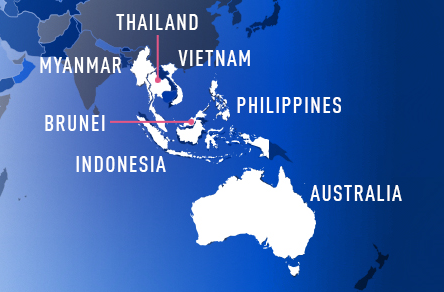
Activity attributed to the Naikon APT hacking group has been spotted for the first time after 2015 - when the group was exposed by “Threat Connect” researchers. This time, it was the radars of Check Point researchers that caught the activity, reporting about the use of a new backdoor named “Aria-body.” Naikon is deploying this new tool against governments of countries in the Asia-Pacific (APAC) region, including Australia, Indonesia, the Philippines, Vietnam, Thailand, Myanmar, and Brunei. The hackers are targeting government-owned public companies, key ministries, and critical organizations in these countries.
Source: Check Point
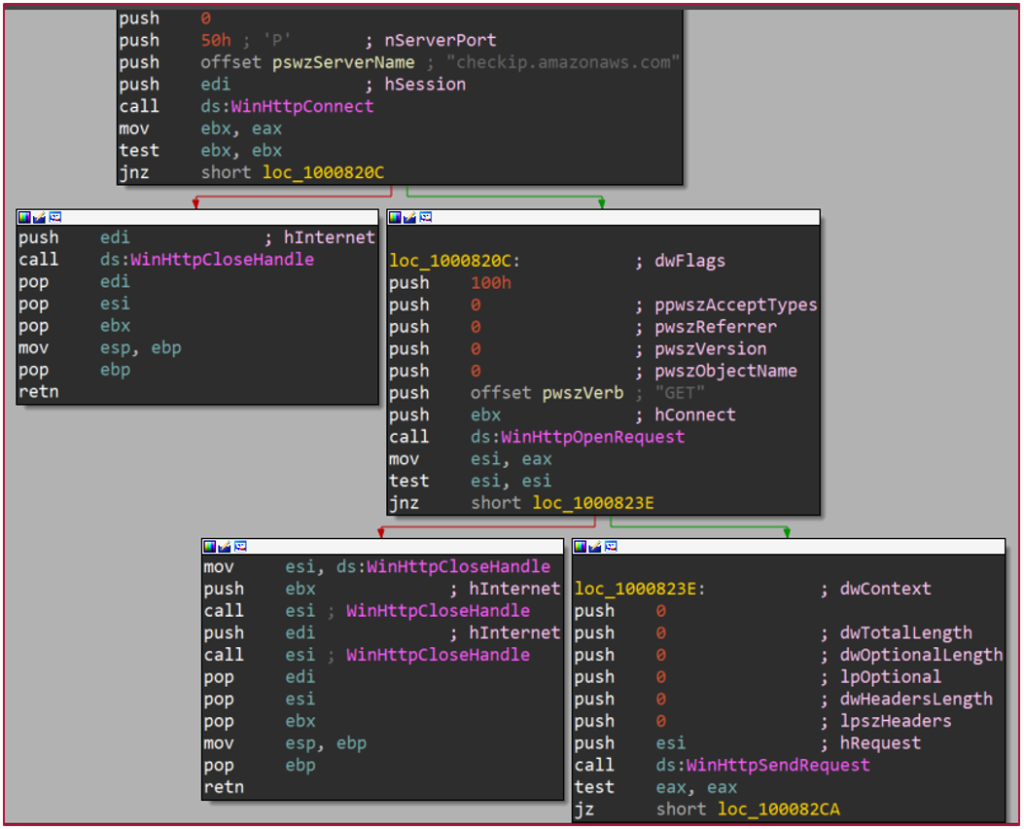
The Naikon actors deploy multiple methods through which they achieve the planting of the Aria-body backdoor onto their targets - from malicious emails containing infected RTF documents to archive files that side-load malicious DLLs and exploit Outlook and Avast proxies. The researchers even noticed the direct distribution of executables that act as loaders. The weaponizer that is used in the RTF files is “Royal Road,” a very capable exploit builder that is used by many threat actors out there. So far, it has been confirmed that Royal Road can exploit CVE-2017-11882, CVE-2018-0798, and CVE-2018-0802.
Source: Check Point
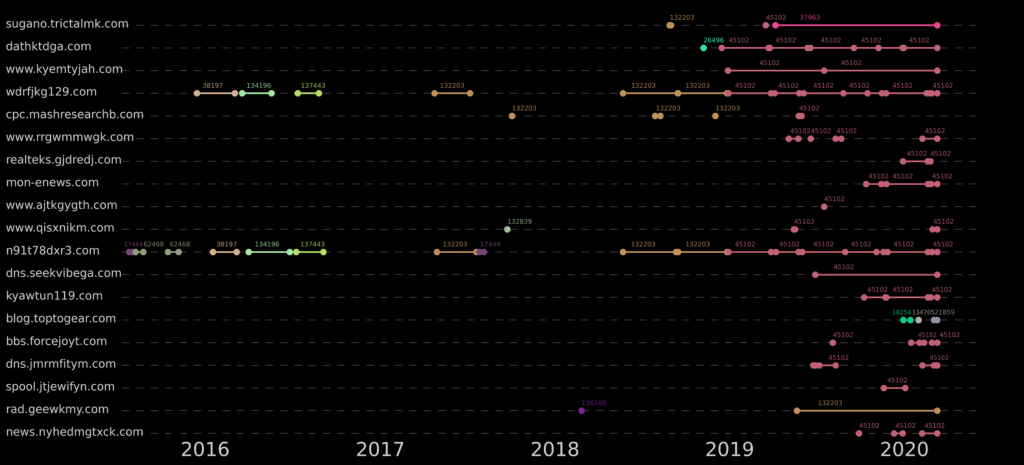
As for the infrastructure, Naikon is currently using C2 servers hosted by Alibaba. Some domains have been used for an extensive time already, others have changed the IP address but kept the same ASN, and several IP addresses were reused on more than a single domain. In one case, the actors were spotted using a compromised IP belonging to the Philippines Department of Science and Technology as a backup C&C server.
Source: Check Point
As for the backdoor itself, Aria-body is a 32-bit remote access tool that is capable of the following functions:
- Create/Delete Files/Directories
- Take a screenshot
- Search file
- Launch files using ShellExecute
- Enumerate process loaded modules
- Gather files’ metadata
- Gather TCP and UDP table status listing
- Close a TCP session
- Collect OS information
- Verify location using checkip.amazonaws.com
- (Optional) Inter-process pipe-based communication
The researchers have noticed several similarities in the debug strings of the Aria-body and the backdoor that was used by Naikon in 2015, called XsFunction. Moreover, some of the functions between the two malware tools are identical, so the attribution was declared with relevant confidence. It means that the particular group was working on the development of new tools behind the front scene, and has now returned to visible action.