Multiple Flaws in Apache Guacamole Leave Sour Taste for Corporate Networks
- Check Point warns about an exploit chain leading “full network control” attack against corporate networks.
- The discovered flaws concern the FreeRDP 2.0.0 and the Apache Guacamole 1.1.0 that is using it.
- Apache was quick to respond and fix the identified and reported flaws, so users are advised to update immediately.
Check Point researchers have published a report on Apache Guacamole, presenting several critical vulnerabilities that plagued the popular software, leading to catastrophic remote attacks and privilege escalation. Apache was quick to push fixing patches after they received the tip from Check Point. Users are now advised to update to version 1.2.0 or later. Apache Guacamole is a particularly popular remote-work gateway that has had over 10 million docket downloads. With the Coronavirus situation, the interest of both companies and hackers towards these tools has become a lot hotter.
Source: Check Point
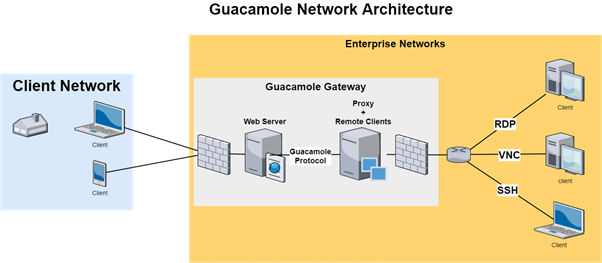
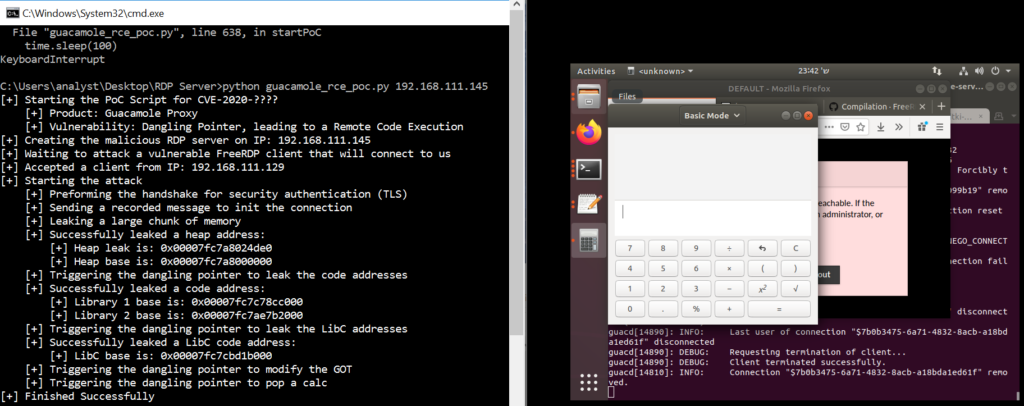
Check Point’s researchers found multiple vulnerabilities and a way to link them to a working exploitation chain. The result could be a full takeover of the Guacamole gateway and all of the connected sessions. The following short video briefly demonstrates the cyber attack.
As explained, Check Point had already done research on FreeRDP 2.0.0, which is a remote desktop protocol client used by Guacamole. Thus, they already knew about the flaws that plagued that component and had something to begin with. Here is a list of the flaws that affect Apache Guacamole 1.1.0:
- CPR-ID-2141 / CVE-2020-9497 – Information disclosure vulnerability
- CPR-ID-21412 / CVE-2020-9497 – Information disclosure vulnerability
- CPR-ID-21413 / CVE-2020-9497 – Information disclosure vulnerability
- CPR-ID-2144 / CVE-2020-9498 – Memory corruption vulnerability
- CPR-ID-2145 and CPR-ID-2146 – Out-of-Bounds reads in FreeRDP
By exploiting the above flaws, the researchers can achieve a privilege escalation scenario that begins by taking over a single “guacd” process. The next step is to connect to the primary process over TCP port 4822, essentially jumping from lower to higher privileges. Next, content and layout are harvested from memory. From there, an attacker would request to join all of the existing connections by supplying the UUIDs that were “stolen” previously. In this stage, the actor may even turn on the “read-only” privilege in the connections, even if they’re not the owners. Finally, for any session that begins after the guacd process has been taken over, the attacker would simply have to repeat the exploit chain all over again.
Source: Check Point
This report is highly critical because it does not present a way to compromise a single computer, but the gateway that handles all remote sessions on an organization’s network. If attackers were to launch an attack as previously described, they would be able to eavesdrop all communications that pass through the gateway, record all credentials used, and even start new sessions to access computers that are out of reach.