Multiple Android Performance Boosters Found to be Malware
- Researchers discovered a new batch of Android adware and malware fetchers.
- The apps have been downloaded by half a million users and were making money through ad-fraud.
- Google has removed all of them from the Play Store, but many still have them installed on their phones.
Trend Micro reports about their recent discovery which involves several malicious apps for the Android platform. The apps were mainly performance boosters, device optimizers, and generic utility tools, and they were all available on the Google Play Store. According to the stats, the malicious batch was collectively downloaded by 470000 users, while the telemetry data indicates that the first activity of the particular campaign dates back to 2017! Google has removed the apps now, but since some people could still be holding them on their device, it is important to uninstall them now.
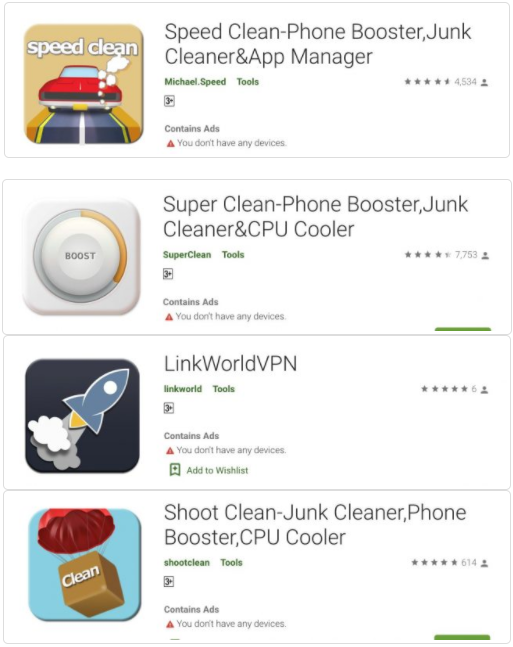
First of all, here is the list of malicious apps that need removal:
- Speed Clean-Phone Booster
- Shoot Clean
- Super Clean Lite- Booster
- Super Clean-Phone Booster
- Quick Games-H5 Game Center
- LinkWorldVPN
- H5 gamebox
- Rocket Cleaner
- Rocket Cleaner Lite
Source: Trend Micro Blog
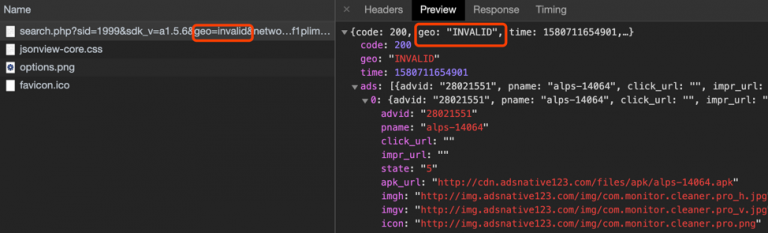
The researchers have analyzed these apps and figured that they are capable of downloading up to three thousand malware variants and payloads. Some engage in ad-fraud to make a quick buck for their publishers, while others are configured to do more damage by stealing information by using the Anubis banking trojan. In some cases, the compromised devices are then used to submit fake reviews about the app on the Play Store, giving them a higher score and feeding the monster of deception.
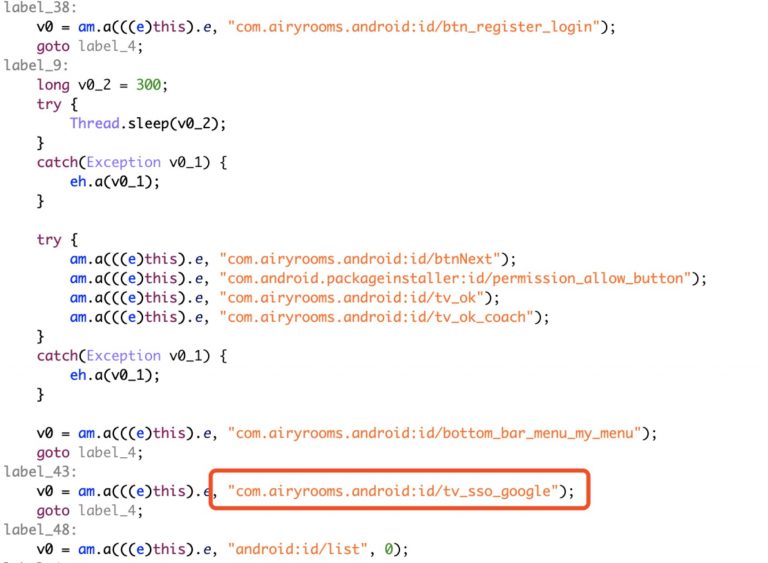
In most cases, the user is tricked into approving the apps’ request for accessibility permissions, which end up in the deactivation of Google Play Protect and the security that comes with it. The same permission is used for the login step on new malicious apps using the user’s Google and Facebook accounts, which is required for the simulated clicks on the ads that take place in the background.
Source: Trend Micro Blog
By noticing the geographic distribution of the victims, the researchers figured that the only exception to the delivery of malicious payloads seems to be China. This could be an indication that the actors behind this campaign are of Chinese descent. As for who is paying the bigger price, Japan takes the lead by far with almost fifty thousand infections, Taiwan is second with almost six thousand, while the United States is third with 2500.
Source: Trend Micro Blog
To stay protected against this kind of threat, use a mobile security suite and avoid installing device performance boosters altogether. Even when these tools aren’t fetching malware, they are not doing much to help your device get any faster. Contrarily, they will make your smartphone feel a little bit sluggish at best.