MostereRAT Phishing Campaign Leverages AnyDesk/TightVNC Targeting Windows Systems
- MostereRAT campaign: A newly seen phishing campaign relying on social engineering distributes a powerful RAT.
- Additional capabilities: It can also install legitimate remote access tools like AnyDesk, TightVNC, and RDP Wrapper.
- What it does: Threat actors can gain complete control over the infected system, facilitating data exfiltration, further lateral movement, and more.
A sophisticated phishing campaign deploying a Remote Access Trojan (RAT) known as MostereRAT was uncovered. The campaign utilizes multiple advanced evasion techniques to compromise systems, grant attackers complete control, and bypass security measures, posing a significant threat to Microsoft Windows platforms.
The RAT has evolved from a banking Trojan, first reported in 2020, into a full-featured RAT.
Attack Methodology and Evasion Tactics
Fortinet FortiGuard Labs research has identified that the MostereRAT phishing campaign begins with social engineering via phishing emails targeting Japanese users with fake business inquiries. Recipients are deceived into accessing an infected site that automatically downloads a malicious file.
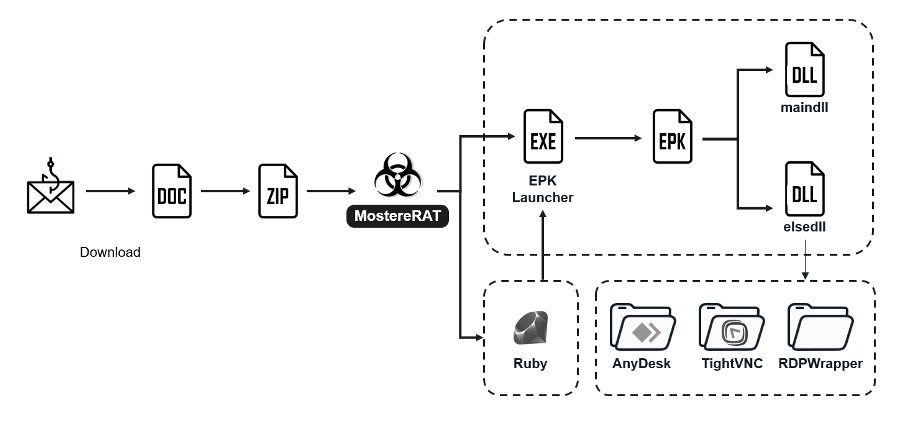
The downloaded Word document guides the victim to open an embedded archive and run the only file it contains to deploy the necessary tools for the subsequent stage. This executable is based on the menu sample from the wxWidgets GitHub repository.
Once a system is compromised, the malware executes a multi-stage payload developed using Easy Programming Language (EPL) to obscure its operations.
A key tactic involves creating a hidden service and running processes with TrustedInstaller privileges to maintain persistence and elevate permissions. The malware actively works to disable security tools by blocking traffic from antivirus solutions.
To secure its connection with Command and Control (C2) servers, the campaign employs mutual TLS (mTLS) encryption, a more secure method than standard TLS that authenticates both the client and server.
Impact and System Control
Jason Soroko from Sectigo said the malware scans for and blocks security products with Windows Filtering Platform “in a style similar to EDRSilencer,” while also “crippling Windows security and updates and obscuring service creation.”
Commands cover keylogging, screen capture, file and process control, early bird injection, and flexible delivery of EXE DLL shellcode and EPK packages.
After establishing a foothold, MostereRAT can deploy additional payloads and install legitimate remote access tools like AnyDesk, tightVNC, and RDP Wrapper.
By leveraging these trusted applications, the threat actors can gain complete, interactive control over the infected system, facilitating data exfiltration, further lateral movement, and other malicious activities. The severity of this threat is rated as high due to the level of control attackers can achieve.
Fortinet’s Perspective on System Control
TechNadu connected with Yurren Wan, Threat Researcher with Fortinet’s FortiGuard Labs, who underlined the strategic shift in MostereRAT’s evolution, saying, “The malware’s design reflects long-term, strategic, and flexible objectives, with capabilities to extend functionality, deploy additional payloads, and apply evasion techniques. These features point to an intent to maintain persistent control over compromised systems, maximize the utility of victim resources, and retain ongoing access to valuable data.”
On the question of attribution, Wan shared, “For this attack campaign and its related infrastructure, no clear evidence was observed linking it to a known threat actor. From a technical perspective, the use of novel and advanced techniques shows limited similarity to known malware families, and therefore attribution cannot be made at this time.”
Answering our request for security tools and mechanisms, Wan recommended a layered approach detailing, "For vendors, developers, and defenders, focus should be placed on implementing layered and proactive defenses to mitigate the threat of Remote Access Trojans (RATs). Attention should be given to all suspicious activity across each stage, including system and network behavior, particularly FWPM (Windows Filtering Platform Management) operations. Accordingly, we recommend using mature and comprehensive security solutions to ensure full protection.”
Security Recommendations
Organizations should consider removing user’s local administrator privileges. “If you remove the local administrator privilege you vastly reduce the attack surface and limit the impact of a malware infection,” sayid James Maude, Field CTO at BeyondTrust.
Maude added that blocking unapproved remote access tools is important since these are often used by threat actors to gain access and maintain persistence. “As these tools are legitimate and signed by trusted vendors, they are unlikely to be detected as malicious by EDR solutions, however in the wrong hands they provide a back door into your organization,” he said.
Soroko offered the following recommendations for security teams:
- harden email defenses and user reporting
- enforce allowlisting
- restrict egress
- add detections for TrustedInstaller token abuse and untrusted parent processes
- enable tamper protection
- deny or tightly manage installation and execution of AnyDesk TightVNC Xray and RDP Wrapper
- block execution of EPK package handlers where not needed
- use Sysmon and EDR to catch early bird or in memory execution and rundll32 launches that load unknown modules
- monitor TLS fingerprints to surface anomalous client certificate use associated with mTLS.
“If compromise is suspected isolate the host, remove rogue WFP filters, rotate credentials, review RDP and remote tool artifacts, search for the hardcoded V account, and restore update components from trusted media,” he added.
Lauren Rucker, Senior Cyber Threat Intelligence Analyst at Deepwatch, underlined that browser security is a critical area for defense in phishing email cases, recommending organizations to “enforce browser security policies restricting automatic downloads and prompts users for confirmation prior to downloading files from unknown sources.”