“Morphixx” Scams Are Rising in Japan, Stealing Credit Card Data
- Morphixx isn’t gone, it just changed location, targeting Japan-based internet users now.
- The malvertising actors are going for fraudulent ad impressions as well as phishing attacks.
- Researchers believe this is the work of sophisticated actors and not lazy “script kiddies.”
A new “Morphixx” campaign has been launched in Japan, with the first signs of malicious activity being recorded by the GeoEdge security research team on August 15, 2020. This is the same malvertising campaign that occurred in Europe in June based on malicious auto-redirections that generate fraudulent ad impressions.
Unfortunately, this is not the end of the risks for internet users. Phishing pages crafted to look like legitimate online portals of recognizable firms are still trying to steal credit card details.
Related: Cybersquatting Actors Love to Mimic PayPal, Apple, and Netflix
GeoEdges says the campaign features two distinctive stages, with the first being typical among all malvertising campaigns. That would be deploying a CDN (content distribution network) to help mask the traffic and make the malicious activities much harder to detect and block. In the case of Morphixx, heavy obfuscation and encryption are also involved.
GeoEdges details how the attacker implements the fingerprinting process by loading a “creativeJS,” which streamlines the site infection process. The second stage is to load the obfuscated script, which is created to set up the URL for the actual redirection. The following is an example payload shared by the researchers.
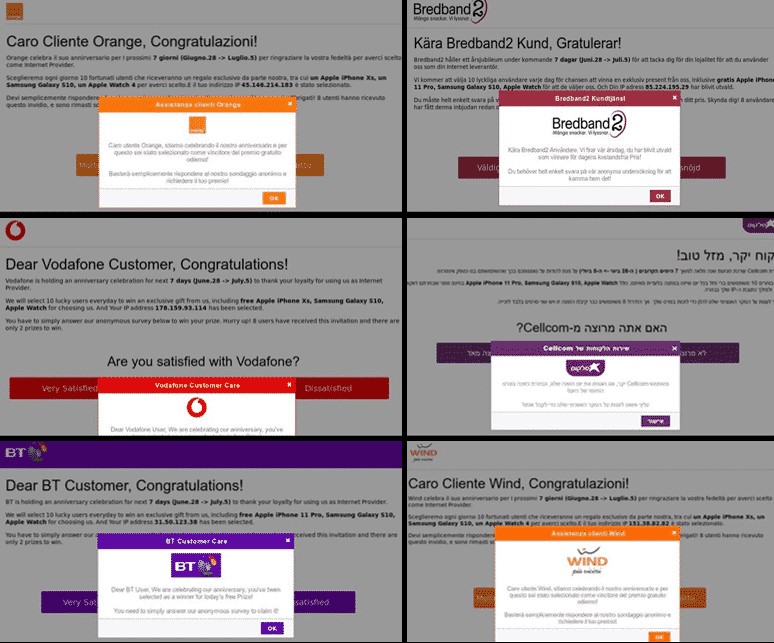
Morphixx actors are careful with the landing pages’ setting, trying to make them as targeted as possible. They detect the ISP of the visitor and serve them to the correct page, which involves winning a prize. In some cases, the potential victim is met with a gift lottery - which they always win, of course.
To redeem the prize, the victims are prompted to enter their credit card information as well as various private credentials. While this should be a telltale sign of fraud, many people are blinded by their willingness to believe they really won something, so they give away their data.
GeoEdge believes that the percentage of targets who are falling victims is between 1% and 2%. In Japan, Morphixx actors went rampant with the number of ads compared to the previous European campaign, and they kept them online for less than 24h.
Also, they preferred to run the malvertising campaign during weekends, when security teams rely on fewer people. As for the creation of legitimacy, the Japanese campaign is supported by comments coming from users who appear to be real, with profile pictures and everything.
The researchers believe that this can’t be the work of “script kiddies” since the level of sophistication and customized creation work is only equivalent to serious hackers who know how to make things work. In fact, by looking at the numbers, they believe that the previous campaign in Europe was more of a test.