Mongol DDoS Attacks Against ISPs Are Gaining Traction
- Sneaky small-sized swarm-like network overload is the new trend in the world of DDoS attacks.
- This development has caught ISPs unprepared, as traditional monitoring tools don’t register this type of traffic as attacks.
- The need to develop more sophisticated attack pattern identification and mitigation is currently imperative.
Named as such due to their resemblance with the Mongol military tactics, a new type of DDoS (Distributed Denial of Service) attacks is causing unprecedented trouble to ISPs (Internet Service Providers) who find that their traditional methods of protection are thrown out of the window. Due to this effectiveness, the Mongol attacks are getting more popular, causing large-scale tormenting on both the communication service providers and their clients.
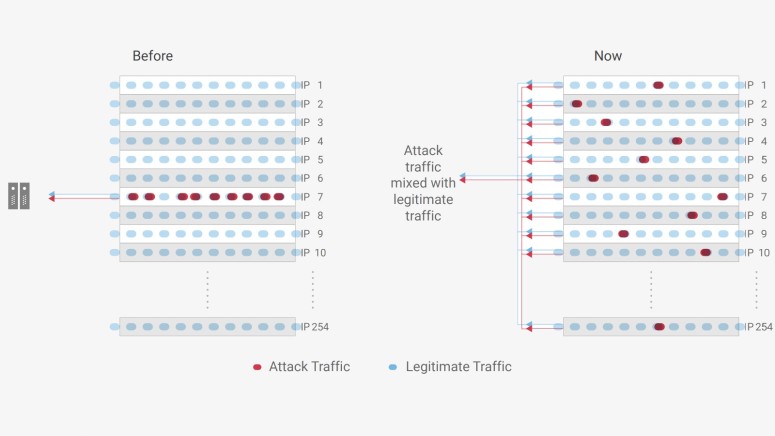
The main idea behind the Mongol attacks is to spread the distribution of the junk data that is injected into the traffic to overload the infrastructure into hundreds of different IPs instead of one or just a few. This creates a host of problems for the network traffic management systems, as there is not a single point of data surge that can be plugged or rerouted. The end result is an equally catastrophic impact on the services, as there can be no mitigation against the general congestion effects of the attack. The attacks are exploiting the ASN-level CSPs, overwhelming them with hundreds of minuscule junk packages.
Obviously, for this method to work for the attackers, there needs to be coordination and specific, narrow targeting. According to NexusGuard analysts, the monitored attacks feature the required level of orchestration, as they were focused on single targets based on their geo-location. In one instance, the junk traffic was spread across 38 IPs, with each one delivering a load of 2.48 Gbps, well below the threshold that would sound the alarm of network monitoring tools. This makes the attack very stealthy, and so the popularity of this approach has grown exponentially during the past months.
For now, ISPs are relying on whatever versatility their protection systems can offer, with black-holing of the traffic being the preferable defensive method, however, and as the attackers use larger numbers of IPs to conduct their attacks, black-holing has become non-feasible anymore as this would mean taking multiple IPs offline. Similarly, selecting blackholing, scrubbing, traffic filtering, and load balancing are not applicable or adequately effective here. NexusGuard sees always-on cloud deployment as the best choice against Mongol DDoS attacks, as they claim the ability to identify any attack size or patterns before the network gets overwhelmed.
The predictions for the upcoming months are not confident on that part, as hundreds of Class C networks and ASNs are expected to get hit by the sneaky Mongol DDoS actors, with DNS amplification causing high network latency or even deadlocks. The next step in protection is bound to be the development and implementation of clever attack pattern identification, as stopping the actors from conducting Mongol attacks is hard considering the fact that they leave no trace.
What is your opinion on the above? Share your thoughts in the comments below, and don’t hesitate to do the same on our socials, on Facebook and Twitter.