New Monero Mining Malware Targets Companies in China and Taiwan
- A malware campaign that employs information stealing and remote admin tools is targeting organizations in China.
- The attackers want to plant a Monero cryptocurrency miner on the infected machines.
- The success of the attack is based on whether the system admins have plugged a 2017 vulnerability on SMB.
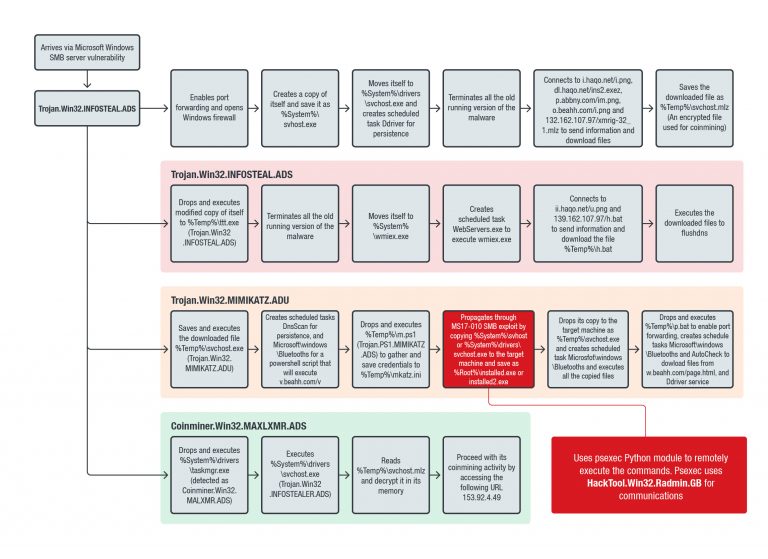
According to a report by Trend Micro researchers, there’s a surge in a hack tool installation attempts that exploits a Windows SMB Server vulnerability that has been patched since 2017. The researchers have determined that the targets are organizations in China, Hong Kong, Taiwan, and Italy. Enterprise-level resources are ideal for the final payload of this campaign, which is a Monero cryptocurrency miner. The attackers use the Mimikatz utility to view the credential information in the infected machine (passwords, Kerberos tickets, etc.), combined with the Radmin remote access tool. This combination empowers them to infect the device with the mining payload remotely, as seen in the following diagram.
source: blog.trendmicro.com
The malware can be downloaded through infected websites, or fetched by other malware tools. It scans the host system and even deleted older versions of itself so that the performance of the infection is maximized. The Monero miner itself is encrypted, as are all of the information collecting tools (Python modules) that are downloaded by the malware onto the victim machine. Some modules are downloaded by the malware itself, while others are directly sent to the machine via the Radmin tool.
Trend Micro clarifies that the patch that plugs the remote code execution vulnerability that this campaign is exploiting was released in March 2017, so if you’re using SMBv1 (Microsoft Server Message Block) and you have not applied the patch yet, you should do so immediately. The telemetry data shows that China and Taiwan received the highest number of installation attempts, although they were not the only countries that were targeted. The prediction of the researchers for the future is that the module structure of the malware is aimed at large-scale infections that will steal credentials and plant even more powerful malware tools via remote administration tools.
Another detail which indicates that these attacks are not random at all is the fact that China was celebrating their Lunar new year when the campaign activity culminated. This decreased the chances of the IT teams of the infected companies noticing that their system CPU and GPU resources are weirdly and inexplicably committed. This is just another example that clearly shows how malicious hackers are leaving nothing at the chance. For the full list of the indicators of compromise, as well as more in-depth technical details about this new campaign, check out Trend Micro’s report.
Have you ever had a cryptocurrency mining malware infection experience? Share the details with us in the comments section below, and don’t forget to check out our socials on Facebook and Twitter, for more tech news like this one.