Millions of Cable Modems Vulnerable to “Cable Haunt” Attacks
- Researchers discover a new attack type that could potentially affect about 200 million cable modems.
- Called the “Cable Haunt”, the attack has severe consequences for its targets, and it’s particularly stealthy.
- There is no evidence of active exploitation right now, but no one can rule this out at the moment.
A team of researchers from the Lyrebird infosec firm and Simon Vandel Sillesen has discovered a new type of attack which they dub as “Cable Haunt”. This critical vulnerability concerns the cable modems of various manufacturers and enables a remote actor to take over a device through an unprotected endpoint. The main implication of this is the interception of the internet traffic of all the devices that are connected to the modem, including the private messages. Other forms of exploitation include the redirection of the traffic, the disabling of firmware updates, the changing of the default DNS server, changing of serial numbers, and also the participation of the modem in malicious botnets.
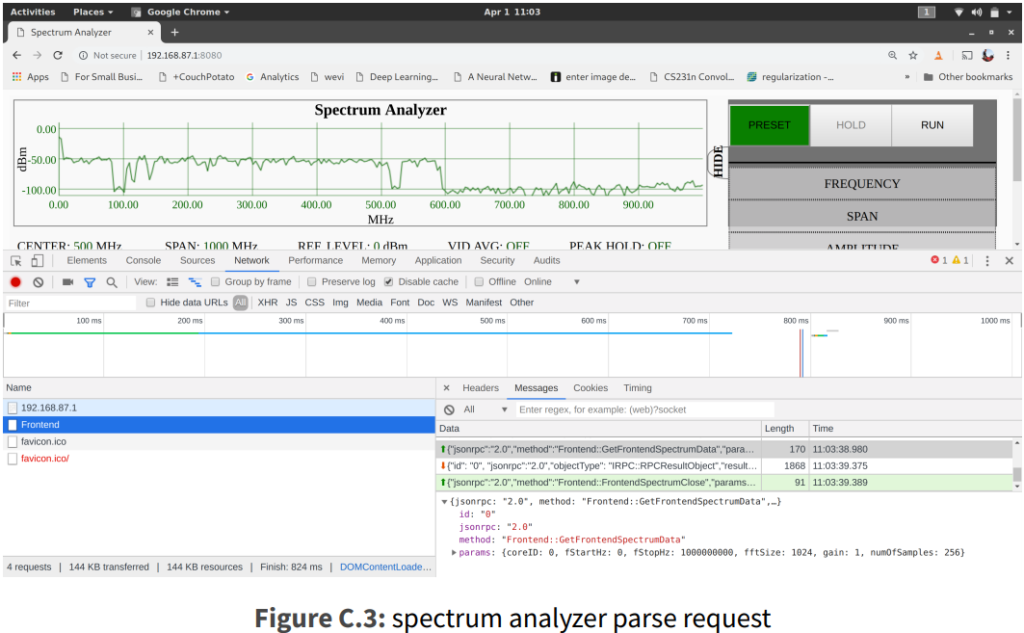
The attack is based on the exploitation of an endpoint that is open to serve a spectrum analyzer tool. As the WebSocket for this tool isn’t protected, an attacker can access the endpoint via an HTTP request. All that would be needed in the execution of a specially crafted JavaScript snippet running in the browser. The next step is to trigger a buffer overflow vulnerability in the JSON request parsing system of the WebSocket. By creating a special message, one could push the modem into arbitrary code execution mode, which would eventually lead to device takeover.
Source: Cable Haunt Report
The researchers have even developed a proof of concept code, so the first question that comes into everyone’s mind is "am I affected?". The following modems have been confirmed to be vulnerable to “Cable Haunt”, although more are bound to be added onto the list soon.
- Sagemcom F@st 3890
- Sagfemcom F@st 3686
- Technicolor TC7230
- Technicolor TC4400
- Netgear C6250EMR
- Netgear CG3700EMR
- Netgear CM1000
- COMPAL 7284E
- COMPAL 7486E
- Surfboard SB8200
The team has also developed a tool to check if your modem is vulnerable or not, which you may grab from GitHub.
If someone has already taken over your modem, chances are that you won’t have a clue. One thing that could potentially help stop the actors on your network's door would be a strict firewall configuration that regular users are unlikely to have set up. As for whether “Cable Haunt” is being exploited in the wild right now, the researchers have found no evidence of that, but it would be easy for skilled actors to hide their tracks anyway. The only thing that we as users can do is to check our modems, apply the latest firmware updates, and contact our ISP and modem vendor to inform them of the problem.