Microsoft Teams Flaws Allowed Message Editing and Caller ID Spoofing
- Flaws uncovered: Researchers identified several vulnerabilities in Microsoft Teams, including ones that allow invisible message editing and spoofed notifications.
- Executive impersonation risk: Attackers to forge a caller's identity, impersonate executives, and manipulate conversations to commit fraud or spread misinformation.
- Microsoft fixes: Microsoft addressed the issues through a series of updates rolled out in 2024 and 2025.
Multiple Microsoft Teams vulnerabilities that could allow threat actors to manipulate conversations, impersonate users, and exploit trust within the widely used collaboration platform were exposed. The findings demonstrate how attackers can leverage the inherent trust mechanisms of such platforms to execute sophisticated social engineering attacks.
With over 320 million monthly active users, the security of Microsoft Teams is paramount for enterprises globally.
Exploiting Trust: Specific Vulnerabilities Detailed
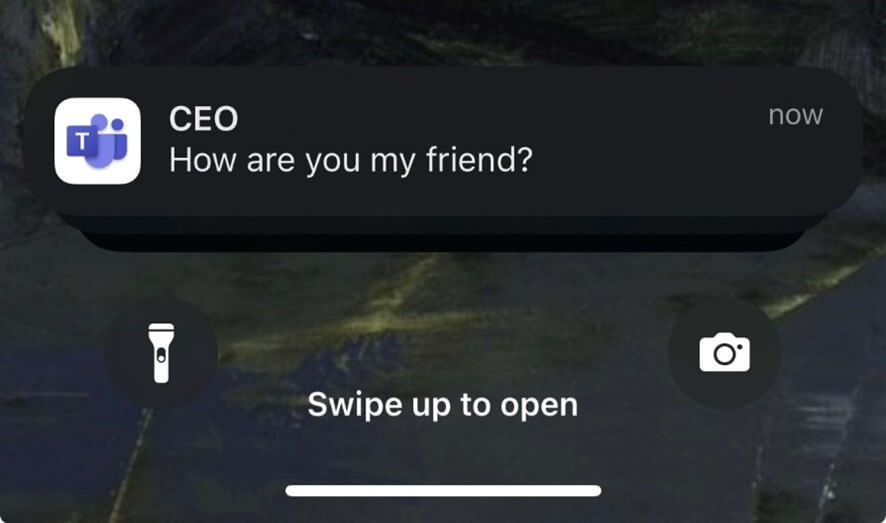
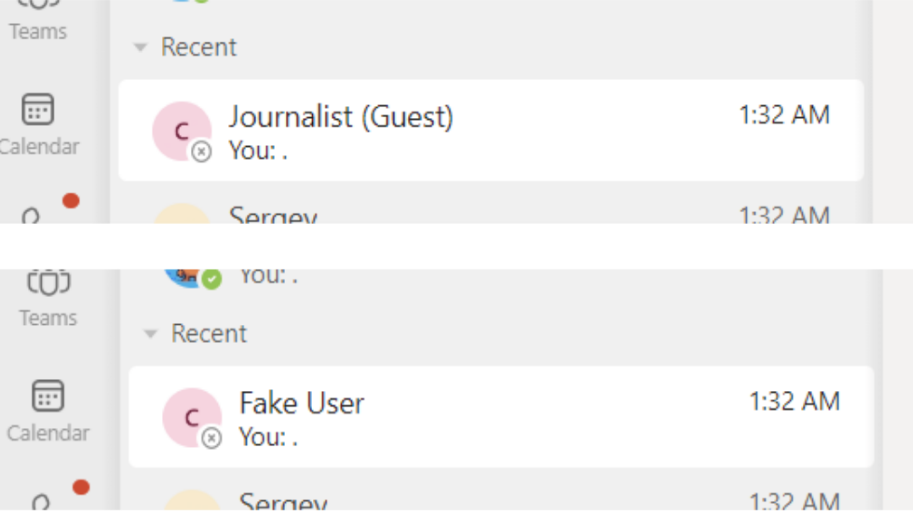
The Check Point Research findings highlight several methods for exploiting the platform. Attackers could edit previously sent messages without triggering the standard "Edited" label, silently altering conversation records.
Another significant vulnerability allowed for the manipulation of notification fields, making an alert appear to come from a trusted colleague or executive.
Researchers also found it was possible to forge a caller's identity in both video and audio calls by modifying call initiation requests. These digital trust issues create opportunities for executive impersonation, financial fraud, and the delivery of malware.
Microsoft Patches and the Broader Security Landscape
After Check Point Research responsibly disclosed the flaws on March 23, 2024, Microsoft assigned the identifier CVE-2024-38197 and deployed fixes, with the final patch completed by the end of October 2025.
While these specific issues have been resolved, the research underscores a systemic risk in the security of collaboration platforms. The incident serves as a reminder that native platform security must be augmented with layered defenses.
As these tools become central to business operations, they also become prime targets for threat actors who specialize in subverting trust signals rather than just technical exploits.
“A notification, a display name, a quoted message—all of these are subtle cues employees rely on to know who they’re talking to and what was said,” CPR stated. “If attackers can bend those cues, they can bend decision-making itself.”
In other recent news, Windows GDI flaws exposed systems to critical threats, including RCE and data leaks.