Microsoft Is Ringing the Bell of May 2021 ‘Patch Tuesday’
- Microsoft has released yet another ‘Patch Tuesday,’ and this one brings 55 bug squashes.
- There are three critical bugs in the set of fixes, and one of them is a wormable flaw with serious potential.
- Adobe has released a fix for Reader that is being actively exploited in the wild right now.
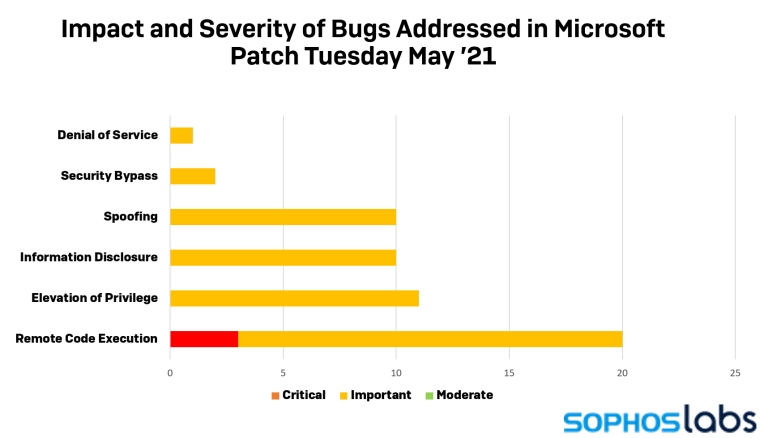
The time for another ‘Patch Tuesday’ has come, and it’s a lean package this time. Microsoft is pushing 55 security fixes for a range of the company’s products, including Windows, Office, Exchange, Visual Studio, and Skype. Of the 55 vulnerabilities identified and addressed by Microsoft’s security team, 20 are remote code execution bugs, of which three are critical. All the rest are classified as important and include 11 "elevation of privilege" flaws, 10 information disclosure bugs, and 10 spoofing issues.
The most serious vulnerability addressed this month is CVE-2021-31166 (CVSS score of 9.8), which exists in the HTTP protocol stack. The flaw could allow an unauthenticated attacker to gain remote code execution access to a server by sending a specially crafted packet to the target. Microsoft says this vulnerability is wormable, which means the threat actor’s presence could spread quickly among vulnerable systems on a network, so addressing it by applying the patch should be prioritized.
The second most critical flaw is CVE-2021-26419, lying in Internet Explorer’s scripting engine. The attacker can exploit this bug by tricking the target user into visiting a specially crafted website or by embedding an ActiveX control in an application or Office document that utilizes IE’s rendering engine and then tricking the user into opening the file.
The third critical bug is CVE-2021-31194, existing in OLE Automation, allowing a malicious actor to execute code on a target system without having to engage in any form of user interaction.
Of those classified as “important,” CVE-2020-24587 stands out for its potential to cause great damage, but even though it’s been known and tracked for a while - and while the attack complexity is of a low lever, the exploit remains unproven in the wild.
All in all, this is a smaller ‘Patch Tuesday,’ yet it’s still important to apply as soon as possible. Make sure to backup your data before you apply the update, as there’s always a chance to end up with a corrupted and unrecoverable filesystem in the process.
On a side but relevant note, Adobe has also released security updates for its products at the same time as Microsoft, and one of the fixed flaws, CVE-2021-28550, has been reported to be actively exploited in the wild. If you’re using Adobe Reader, it is critical that you apply the fixing patch immediately.