Microsoft Disrupts RaccoonO365 Phishing-as-a-Service, Seizes 338 Domains
- RaccoonO365 PhaaS: Microsoft disrupted the infrastructure of a rapidly growing PhaaS platform, seizing hundreds of domains.
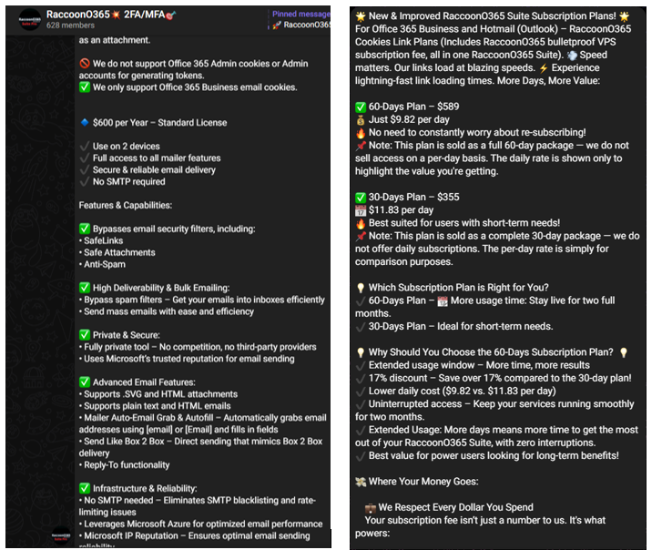
- Credential theft tools: The PhaaS sold subscription-based RaccoonO365 phishing kits offering fake Microsoft emails and login pages.
- Targeting Microsoft users: At least 5,000 Microsoft 365 credentials in over 90 countries were affected.
Microsoft's Digital Crimes Unit (DCU) has executed a significant blow against the cybercrime ecosystem by disrupting RaccoonO365, a rapidly growing phishing-as-a-service (PhaaS) operation. Through a court order, the DCU successfully seized 338 websites integral to the service's infrastructure, effectively cutting off a major source of credential theft tools.
RaccoonO365 Phishing Kits and Operations
Tracked by Microsoft as Storm-2246, RaccoonO365 provided subscription-based RaccoonO365 phishing kits that enabled even low-skilled cybercriminals to launch sophisticated attacks.
These kits mimicked official Microsoft branding to create convincing fraudulent emails and login pages designed to steal Microsoft 365 usernames and passwords.
Since July 2024, the service has been implicated in the theft of at least 5,000 Microsoft credentials across 94 countries.
The operation's leader was identified as Joshua Ogundipe, a Nigerian individual who allegedly authored the code and marketed the service on platforms like Telegram, amassing over 850 members and at least $100,000 in cryptocurrency payments.
Impact and Cybersecurity Implications
The phishing service takedown is a critical move to mitigate widespread cybersecurity threats. RaccoonO365's services have been used in broad campaigns, including a tax-themed attack that targeted over 2,300 organizations.
Alarmingly, at least 20 U.S. healthcare organizations were targeted, posing a direct risk to public safety by creating a pathway for ransomware attacks that can disrupt patient care.
The disruption highlights a growing trend of accessible, scalable cybercrime tools that lower the barrier to entry for malicious actors.
This month, Okta reported discovering a PhaaS operation targeting Microsoft and Google accounts.