Microsoft 365 Direct Send Exploit Exposes Significant Email Security Risks
- Feature exploitation: Threat actors exploit the trusted M365 email pathway, designed for unauthenticated devices like printers, to bypass security checks and launch attacks.
- Bypassed authentication: Direct Send allows messages to circumvent standard sender verification protocols like SPF, DKIM, and DMARC.
- Mitigation required: Microsoft has introduced controls like RejectDirectSend and plans a "default-off" posture for new tenants.
A feature in Microsoft 365 Exchange Online, known as Direct Send, is being actively exploited by malicious actors to conduct phishing campaigns and business email compromise (BEC) attacks. Direct Send is designed to allow legacy devices and applications, such as multifunction printers and scanners that cannot properly authenticate, to send emails within a tenant.
However, its ability to bypass standard security and authentication checks makes it a prime target for abuse.
Understanding the Inherent Email Security Risks
Security researchers have observed a significant increase in Microsoft 365 Direct Send abuse, where attackers emulate device traffic to send unauthenticated messages that appear to originate from trusted internal accounts.
The primary risk associated with Direct Send is that it creates a trusted channel that bypasses critical sender verification protocols, the Talos Intelligence security report said.
Standard email security relies on a combination of Sender Policy Framework (SPF), DomainKeys-Identified Mail (DKIM), and Domain-based Message Authentication, Reporting and Conformance (DMARC) to validate a sender's identity.
Because Direct Send is intended for unauthenticated traffic, messages sent through this channel are not subjected to these checks.
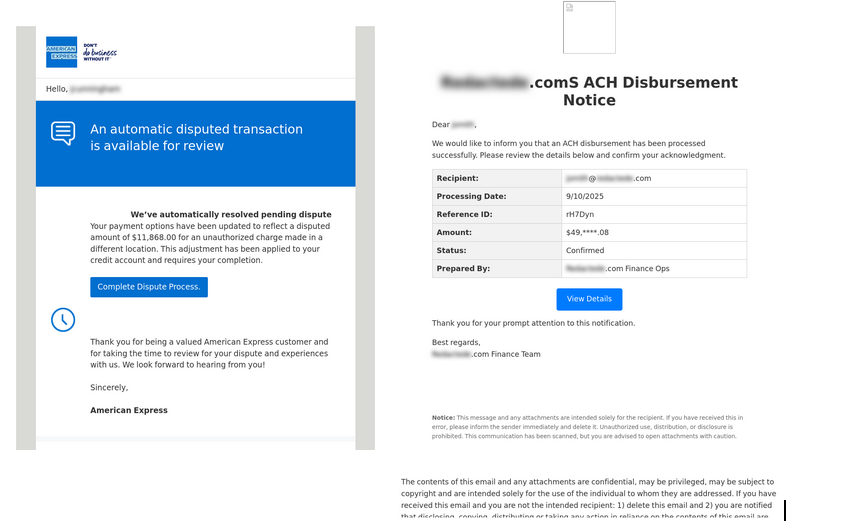
This allows attackers to craft phishing attacks that impersonate internal users, executives, or IT help desks with a high degree of success, as the malicious emails are implicitly trusted by the receiving infrastructure.
Lures often include fake payment notices, task approvals, or QR codes leading to credential harvesting pages.
Cybersecurity Best Practices for Mitigation
In response to the growing threat, Microsoft has introduced new controls, including a RejectDirectSend setting, and plans to disable the feature by default for new tenants in the future.
Organizations are advised to take immediate action to mitigate these email security risks. Key recommendations include:
- Disabling or restricting Direct Send where feasible
- Migrating devices to authenticated SMTP
- Implementing partner/inbound connectors for approved senders
- Strengthening authentication and alignment
- Strengthening the policy, access, and monitoring.
Implementing robust monitoring to alert on unexpected internal domain messages that lack proper authentication is also a critical step in strengthening defenses against this attack vector.
In other recent news, security researchers spotlighted evolving phishing campaigns that deliver HoldingHands malware across China, Taiwan, Japan, and Malaysia.