‘Meetup.com’ Fixed Flaws That Could Have Allowed Hackers to Redirect Payments
- Several critical flaws on the ‘Meetup.com’ platform have been discovered and reportedly fixed now.
- Exploiting the vulnerabilities would be very easy and completely stealthy from the victims.
- Meetup says nobody has exploited the reported and now fixed flaws in the wild, so user accounts are safe.
‘Meetup.com,’ a popular event creation platform that is widely used around the globe, has fixed several critical flaws that have been discovered by the Checkmarx team of researchers. The vulnerabilities include cross-site scripting (XSS) and cross-site request forgery (CSRF) holes that can potentially result in Meetup group takeovers, role escalation, access to the group’s functions, and assets, and the redirection of PayPal payments to the attacker’s account.
The Checkmarx team has created a proof of concept script that they shared with Meetup.com and demonstrated that the attack could be carried out silently.
Source: Checkmarx
Meetup.com gives the meeting/event creator the option to organize an event that’s “free to join” or set a fee. Those who want to participate in paid events use PayPal to cover the expense. This is precisely what an attacker would be interested in.
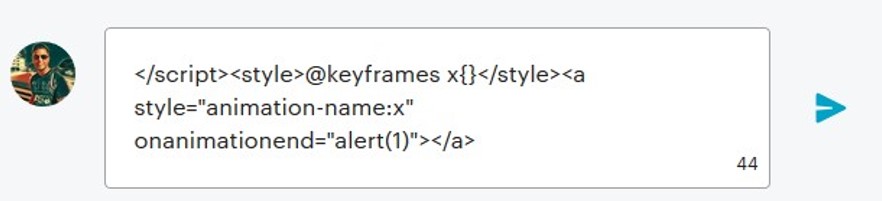
According to what the researchers found, a threat actor could potentially drop the following script into the discussion area of a Meetup event, and nobody would be able to see it. When someone with a JavaScript-enabled browser visits that page, a popup appears warning them about anything the attacker chooses to display there.
By chaining the XSS and the CSRF together as shown in the above video, attackers could escalate their privileges from a regular user to a Meetup event co-organizer. That would open the way to accessing group functions, including payments and the “Manage Money” tab.
All that it would take in order to steal people’s payments is to change the PayPal email where the money would normally end up with an address controlled by the attacker. Since Meetup doesn’t send notifications to the event creator when such changes occur, the organizer wouldn’t realize what happened until it would be too late.
Checkmarx informed Meetup.com of their findings on December 14, 2019, and the platform proceeded to apply the first fixes in March 2020. Checkmarx tested again but found that the fixes were partial, so they returned with additional suggestions. Eventually, Meetup.com fixed everything on July 15, 2020, so the problems demonstrated above shouldn’t be an issue anymore.
As for whether or not anyone has exploited the discovered vulnerabilities in the wild all this time, Meetup officially states that they have found no evidence of this, so Meetup users shouldn’t feel at risk.