MCPoison Vulnerability in Cursor IDE Allows MCP Trust Bypass, Exposing Persistent Execution Risks
- MCP Trust Bypass: Cursor IDE failed to revalidate subsequent modifications to the approved MCP configuration.
- Risks for developers: The Cursor IDE security flaw risks include RCE for prolonged attacker access and privilege escalation.
- Unnoticed compromise: Malicious configurations auto-trigger upon project sync or reopening.
The recently discovered, now-patched MCPoison vulnerability in the popular developer-focused AI Cursor IDE enables persistent code execution through compromised Model Context Protocol (MCP) configurations. Cursor combines local code editing with large language model (LLM) integrations.
Detailed by Check Point Research (CPR), the flaw underscores significant risks for developers utilizing this AI-powered IDE in collaborative environments. Cursor released an update on July 29.
Exploitation Pathway
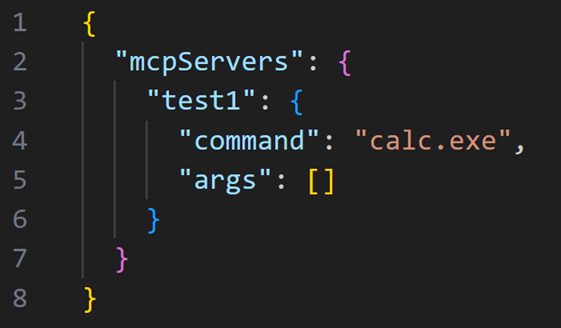
Cursor IDE offers developers extensive configuration control through workspace-specific MCP files, designed to ease task automation and API integration.
However, the report says the vulnerability reveals that once an MCP configuration is approved, the IDE fails to revalidate future modifications to its commands or arguments.
This oversight allows an attacker to inject malicious payloads after gaining initial trust. For example, an attacker could replace approved commands with reverse Shell scripts, enabling silent remote code execution (RCE) whenever the project is reopened.
These attacks are particularly effective in shared development settings involving Git repositories, where MCP files are routinely synced among team members.
Victims may unknowingly execute malicious commands embedded within an MCP file, granting attackers ongoing access to their systems without additional interaction.
Mitigation Measures
To address this issue, Cursor has released version 1.3, which mandates new approval prompts for any modifications to MCP settings. Developers are urged to update immediately, regularly review project configurations in .cursor directories, and restrict permissions on shared repositories to limit unauthorized edits.
In March, TechNadu reported on a novel GitHub Copilot and Cursor vulnerability that allowed weaponizing the AIs.
The persistent risk introduced by the MCPoison vulnerability underlines the importance of robust validation mechanisms in developer tools.