Massive ‘Breach Index’ Data Archive Leaked Online
- A now discontinued breach index platform had its massive database leaked online.
- The initial leak lasted for a couple of hours, but that was enough for dissipators to take it from there.
- There’s a mix of disclosed and unknown breaches in the archive, so following proper security practices is the only way to stay safe.
A data breach index site named ‘Cit0day’ has been diligently collecting hacked databases since January 2018, selling access to hackers for a monthly fee. The platform discontinued operations in September 2020, but its massive database archive remained valuable for crooks.
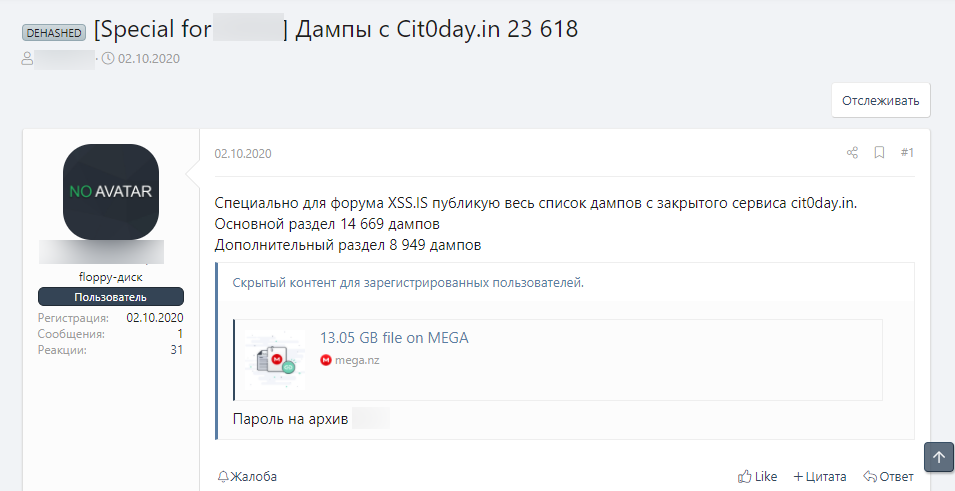
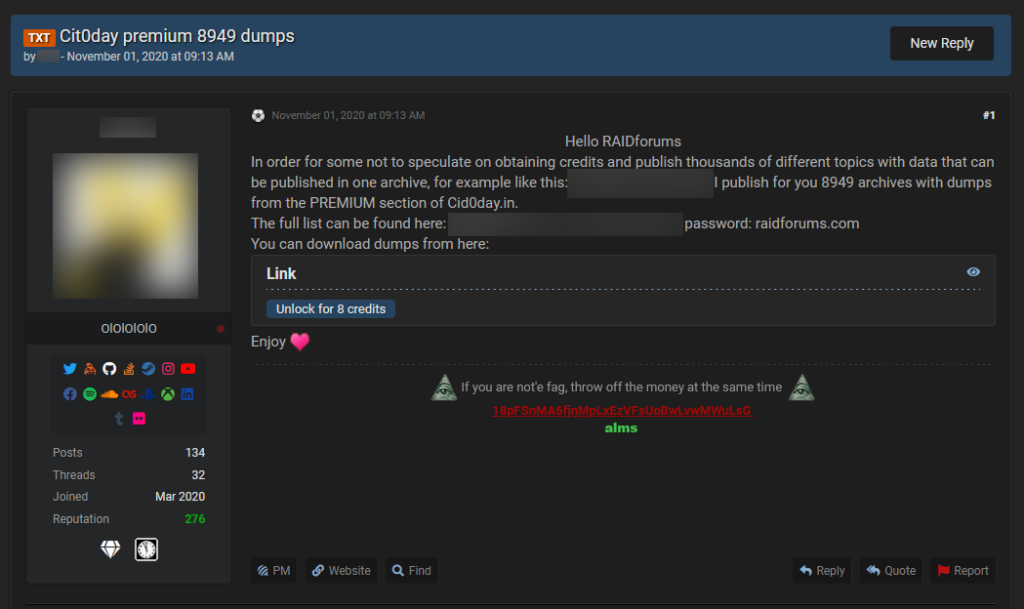
Someone, possibly the original operators of the index site, has leaked the archive in its entirety for a few hours on a dark web forum. The pack contained 50 GB and 13 billion users records from 23,618 hacked databases that were freely shared online.
Investigative journalist Catalin Cimpanu has made an effort to confirm the shared data’s validity and reports that Italian security firm D3Lab has seen the data first hand. Even if it’s no longer freely shared (for now), and considering that few people had the chance to download it, the leaking on other channels is already underway. Data brokers are using Telegram and Discord to further disseminate the pack, and some even report it to other hacker forums.
For now, spammers and credential stuffing actors are using the databases and the email addresses in them, so it’s being utilized in a bulk way. Later on, a more sophisticated and specific-targeting wave will rise, but sophisticated hackers need to perform quite some digging into the massive archive first. The question that arises from this is whether or not the data is fresh.
Related: One Million ‘Star Tribune’ Users’ Data Leaked on Dark Web Forums
Cit0day was collecting both old and new databases, and there’s a mix of known and unknown breaches in the archive. That said, some of these were in the spotlight at some point, and the compromised users probably already went through resetting their credentials.
The archive’s most dangerous parts are those concerning smaller sites that never bothered to disclose any security incidents or never realized them. These sites aren’t using strong hashing algorithms and salting for the user passwords, so the credentials are in plain-text form.
We have reached a point where there are so many leaks that even keeping track of them is impractical. This leak alone is maybe the biggest of its kind, so properly evaluating it would take a lot of time. That said, you should always treat your accounts as potentially compromised and reset your credentials frequently. In addition, you should use unique and strong passwords everywhere, activate MFA if available, use anonymous email accounts, and try to share the minimum possible information about you.