MarioNET Framework Demonstrates Potential for Stealthy Exploitation
- Researchers show that it’s possible to run anything on a victim’s Web browser without getting detected.
- Using an example framework called “MarioNET”, you can hijack system resources while running in the background.
- Users are advised to review and actively manage their browser's 'service workers'.
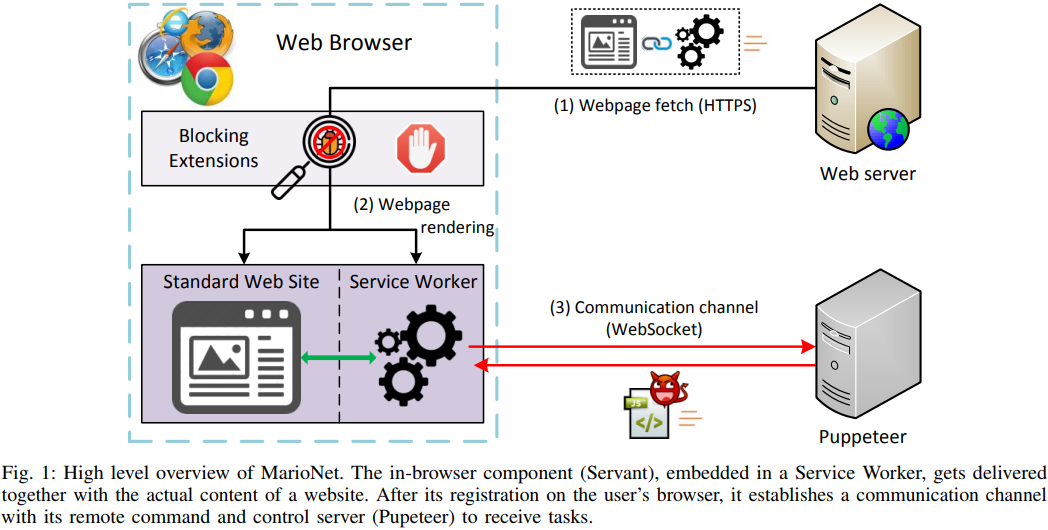
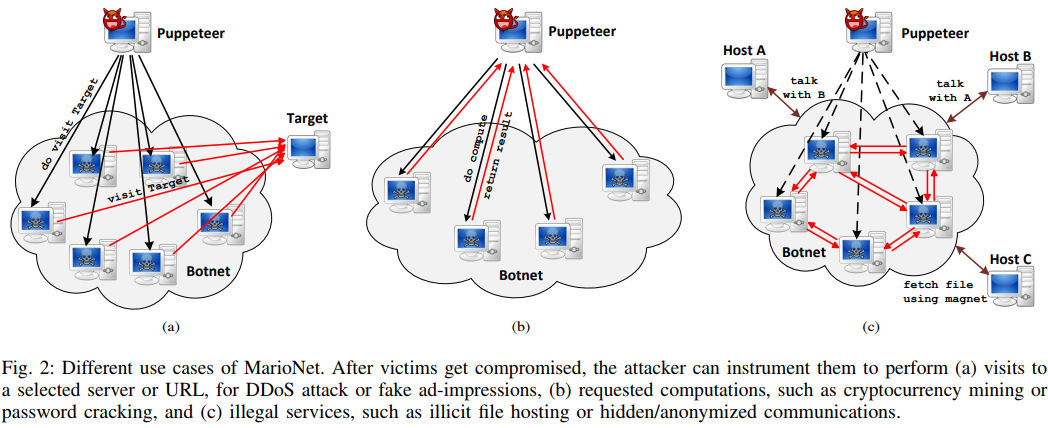
According to a team of Greek security researchers, running malicious code on a browser without getting detected, and keeping the code running even after the tab that initiated the process is closed, is perfectly doable. Using an example framework called “MarioNET”, they have showcased that it’s feasible to hijack a website’s visitors’ resources by using already available HTML5 APIs. This would allow the running of cryptocurrency mining scripts, using the visitor’s machine as a DDoS attack contributor, for password cracking computation and anything else a spiteful hacker can think of.
As all modern browsers support the APIs used in this example framework, and since no further installation or any user interaction is required, the attack is considered entirely stealthy. The framework utilizes “service workers”, which are used by websites to interact with the browser without having to visit the domain. For example, getting a notification about a newly published blog post on your favorite tech news website is done by a service worker and you don’t have to have an open tab on the particular website to get it. This is a background process that requires no interaction with the user after its registration. This registration is usually done through a prompt, but registering a service worker automatically is also possible, leaving the user in the dark.
Source: ndss-symposium.org
By taking advantage of the fact that service workers are completely isolated and independent from the websites that registered them, MarioNET can continue to run as a separate thread, so the browsing speed is not affected at all, and the user is unlikely to notice the resource-stealing activity. After all, people who regularly check and manage the service workers that are registered and/or running on their browser are the overwhelming minority. This practically means that MarioNET is seamlessly running in the background, as long as the browser is running on the victim system.
Source: ndss-symposium.org
If you want to check what service workers are running on your browser, you can input “chrome://serviceworker-internals/” in Chrome’s URL bar, or “about:debugging#workers” if you’re using Firefox. Moreover, there are several browser extensions out there that will at least push a warning notification when a web page tries to register a new service worker without a prompt. Beware that most service workers are used for legitimate purposes, so disabling everything indiscriminately will undermine your browsing experience in the affected websites.
Are you regularly reviewing the service worker entries on your browser? Share your experience in the comments section below, as well as our socials, on Facebook and Twitter.