Malicious WordPress Plugin Targets Windows Users with Fake Java Update Pop-Up
- A newly identified malicious campaign is targeting WordPress users on Windows with malware.
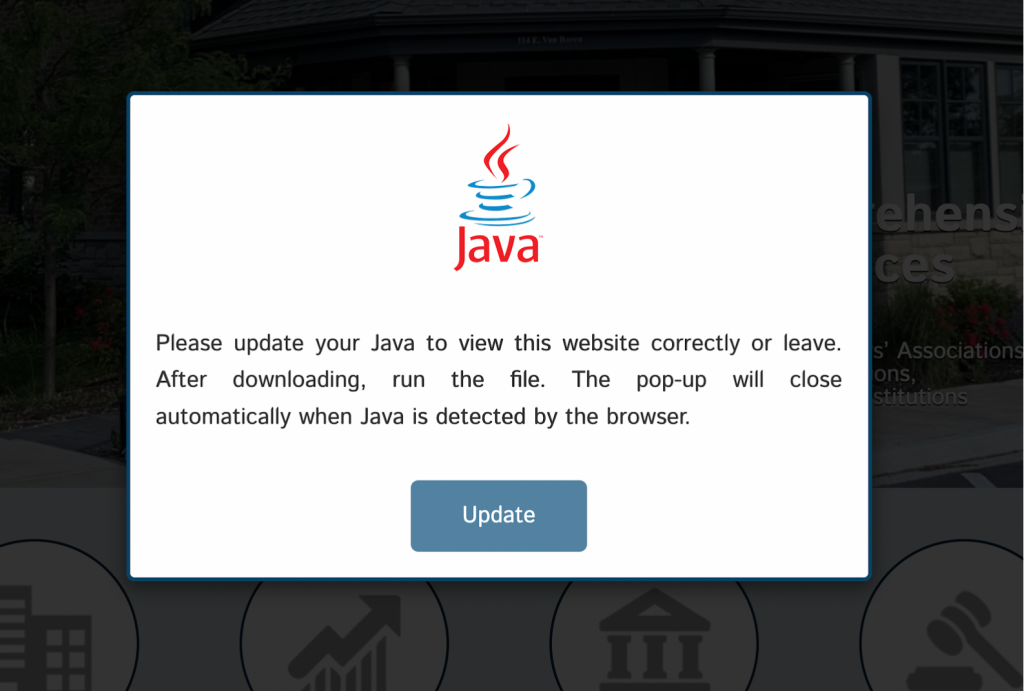
- The pop-up simulates a genuine Java update, complete with localized text, a progress bar, and a download link.
- The malware monitors user actions and exfiltrates browser data, among others.
WordPress users are targeted through a seemingly legitimate stealthy plugin, deploying deceptive “Java Update” pop-ups that aim to compromise website visitors. Its primary goal is to inject a counterfeit Java update prompt into the site's frontend code.
The attack uses a plugin masquerading as “Yoast SEO” and residing within the /wp-content/plugins/contact-form/ directory, according to Sucuri researchers.
The plugin leverages several evasion tactics, such as fake branding and cloaking, selective targeting, and social engineering.
It mimics respected plugins and manipulates metadata to avoid suspicion. Additionally, it hides itself from the WordPress admin dashboard, complicating detection and removal.
The injected JavaScript checks device parameters, targeting primarily Windows users and avoiding mobile devices or systems running macOS or Safari.
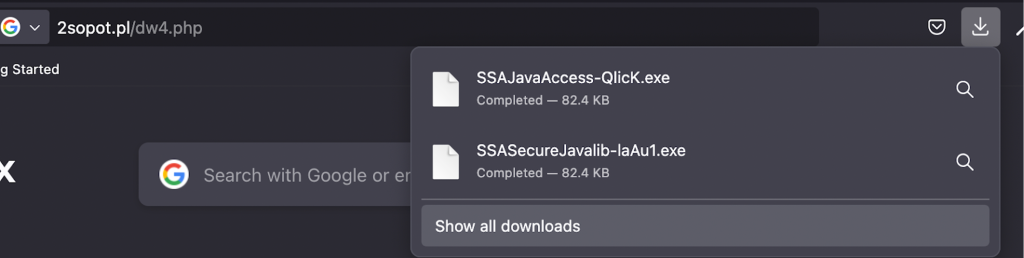
The pop-up simulates a genuine Java update, complete with localized text, a progress bar, and a download link. Victims who interact may unwittingly download and execute a malicious .exe file from a third-party domain.
Core infection vectors include persistent injection, session and cookie management, and process monitoring and exfiltration.
The massive JavaScript block embedded in the HTML head section dynamically manages the deceptive pop-up and handles post-interaction events. The plugin manages cookies and session variables to control pop-up frequency and track user actions.
After initiating a download, the malware uses system commands like tasklist to monitor for execution of the malicious payload, sending real-time notifications to attackers via Telegram. It also exfiltrates browser data and tracks if a user’s system runs known malicious processes.
End-users risk system compromise, data exfiltration, and post-infection malicious activity, while website owners face reputational harm and potential search engine blacklisting.