Malicious Telegram App Secretly Loads Malware Sites
- Telegram app “MobonoGram” is loading malware websites in the background.
- The app was available on the Play Store for quite a while, getting downloaded 100000 times.
- The malicious services loaded automatically, even after rebooting, or after their manual killing.
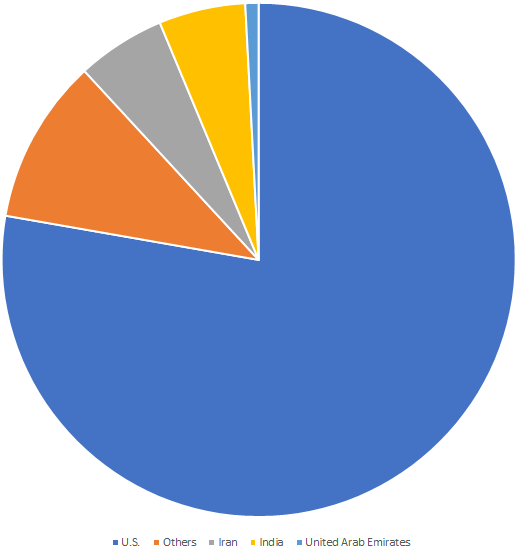
According to a Symantec report, there’s a Telegram application named “MobonoGram 2019” that was available on Google Play Store until recently, accumulating about 100 thousand installations before being removed. The app promoted itself as an unofficial version of the Telegram app, a popular communications tool for users who value their privacy and want to keep their communication with others away from prying eyes. The two main reasons for people to choose MobonoGram instead of the official Telegram app is apparently the more abundant set of features that it offers, and the fact that is was available in regions where the official Telegram app is banned.
image source: symantec.com/blogs
As it seems though, these two were not the only differences between the two apps. Symantec researchers discovered that MobonoGram also runs several services under the expected messaging functionality, without asking for the user’s consent, and without doing it openly. These processes basically open browser sessions that load numerous malicious websites in the background. Symantec says the number of these websites was “endless”, as the app keeps on opening them until the RAM of the device is filled up. Based on the investigation of the researchers, it looks like the app was malicious from the beginning, so this is another failure for the Play Store reviewers.
image source: symantec.com/blogs
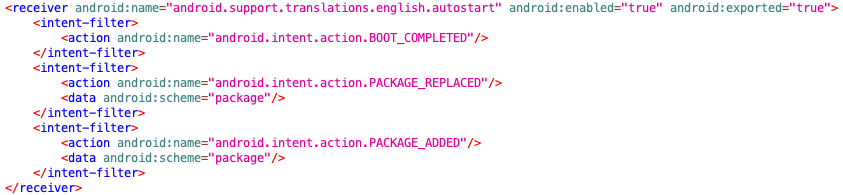
The app didn’t even wait for the user to launch it upon a device restart, as it features an “Autostart” class in its manifest file, launching it after a boot-up, an installation, or an app update. From there on, the additional services that are initiated are taking place in the background, so the user is unlikely to notice anything. Even if the user locates the malicious services and kills them manually, the app will re-launch it thanks to the “AddService” class that has a setting for two hours.
When the services are running unobstructively, they access a set of designated servers that respond with a URL, a user agent, and three JavaScript codes. The URL is selected to be relevant to the IP address of the victim, while the researchers noticed that there are some cases where the URL is making a request to itself, entering an infinite loop state. The three JavaScript codes are there for the addition of click fraud action in the future when the attackers decide to implement this. Right now, they are executed by the server without anything particular happening.
Have you used a Telegram alternative that operated like the above? What was the name of the app? Share your comments with us in the dedicated section down below, and help us raise awareness by sharing this post through our socials, on Facebook and Twitter.