How Malicious Actors Use DNS Tunneling to Exfiltrate Data
- Malicious actors infiltrate and exfiltrate data through DNS tunneling and C2 channels.
- The packets are sent from the malware on the infected system and then stitched together on the server side.
- Exfiltration is harder to perform than infiltration, but it’s possible if specific rules are respected.
Researchers of the Unit42 cybersecurity firm have compiled an interesting report on how malicious actors utilize command and control (C2) communication channels over the DNS, achieving a new way to exfiltrate data. Until now, shady C2 servers were infecting the DNS traffic with payloads that found their way onto the victim’s system, performing their malicious activity on a foundational level that we all trust and use the DNS protocol. However, and due to the lack of adequate data filtering and scrutiny on this level, attackers can take the next step of data exfiltration, and they do.
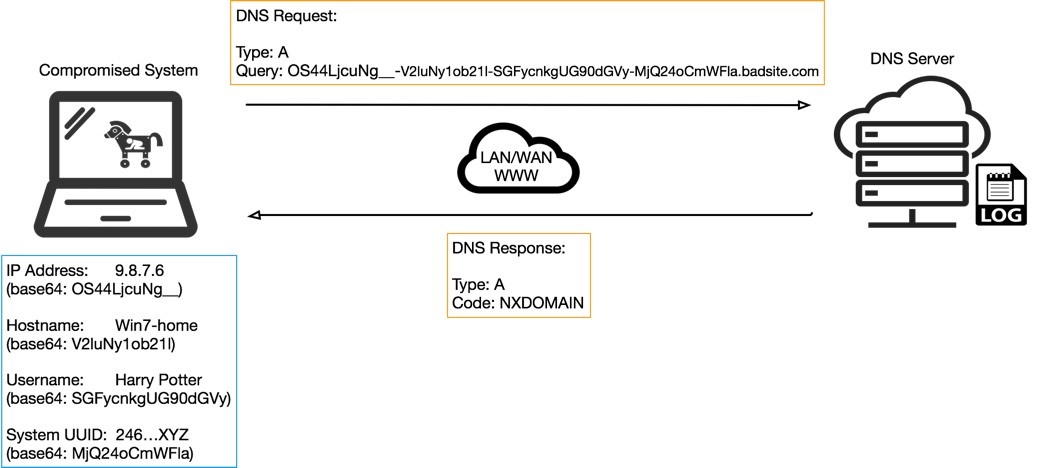
It’s all done through the leveraging of the DNS querying technology, something that can be considered as a type of data trace. Data such as your IP or your operating system which suddenly pops up as a warning message when you’re browsing a webpage is exfiltrated in this very way. Especially if the DNS server has debugged logging enabled, then this data trail is further extended.
According to the Unit42 report, the actors set up a C2 channel that serves as a beacon, indicating the status of operation for the remote payload. The malware that is planted inside the victim’s machine is sending query strings over DNS, and besides the “heartbeat” signals, the communication also includes metadata about the victim. This metadata allows the malicious actors to distinguish the individual infections and tell the difference between the various victims. A solid type of data to achieve this is UUIDs (Universal Unique Identifiers), as IPs, hostnames, and usernames are often duplicated.
source: unit42.paloaltonetworks.com
As long as the encoding of the query data is correct and it respects the UDP size limits (512 bytes packet), there’s really nothing that can’t be exfiltrated out of the victim’s machine. As 512 bytes are quite limiting, the malicious actors have found ways to stitch multiple packets together on the server side, although this often ends up having corrupted communications on a higher percentage than they would like. Also, they can’t go too far with the checking and transmission requests, as this would raise alarms for the network administrators.
So, if malicious actors have found ways to bypass DNS safety and security layers, and now perform not only data infiltration but also exfiltration, then what can we do about it? First of all, you can block IPs that are known to be malicious. Secondly, you can set up filtering for DNS query strings that look unnatural, and don’t respect the size limitations. Finally, there are certain DNS security products out there that can spot weird or abnormal domain access requests, and actively block them.
Share your thoughts on the above in the comments section below, and check out our socials on Facebook and Twitter, where more tech news are posted every day.