Malicious Actors Actively Distributing Novel “CoronaVirus” Ransomware
- The new Coronavirus outbreak constitutes an inspiration for ransomware actors, who have named a new strain after it.
- The ransomware comes after the dropping of the KPot stealer, locking all system files and asking for a small payment.
- The actors are rebooting the infected system and setting a key to display the ransom note upon the system start.
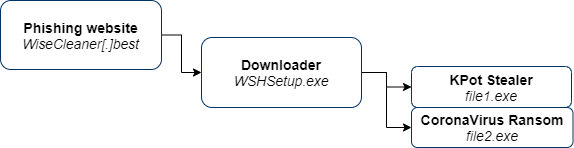
As reported by CyberArk researchers, there’s a new type of ransomware that spreads through a phishing website that resembles a popular Windows maintenance apps portal. The malicious URL is "WiseCleaner[.]best," and the file that begins the infection procedure is "WSHSetup.exe." It is actually a downloader that fetches the ransomware as well as the KPot stealer (Khalesi). KPot is a popular tool being sold for $100 on darknet forums. It is under active development and has an extensive info-grabbing ability. KPot is the first to be executed, followed by the CoronaVirus malware, which locks down the system files.
Source: CyberArk Blog
KPot steals whatever information it can from the target computer, such as account information, web browser cookies, locally stored passwords, instant messenger histories, emails, cryptocurrency wallets, VPN, RDP, and FTP login credentials. Having pocketed all that data, the actors aren’t very interested in pushing the victims for a noteworthy ransom, and they are asking for only 0.0008 BTC, which is the equivalent of about $43. Besides encrypting files and deleting shadow copy backups, they also rename the drive to "CoronaVirus (C:)." The ransom note is dropped in every folder and the malware also changes the BootExcute key to display the ransom note upon system reboot.
Source: CyberArk Blog
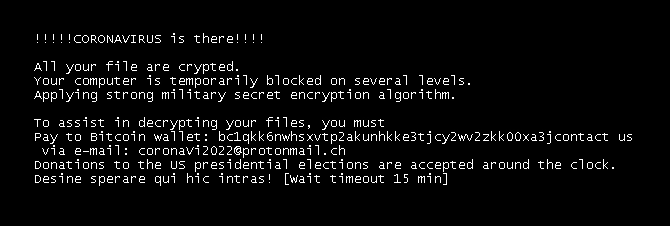
The rebooting of the target system is secured by the ransomware itself, as it's built-in its functionality, and it happens as soon as every file is encrypted. The final step before rebooting is to delete the malware itself, to mitigate the risk of retrieval and analysis. The note makes the typical claims about military-grade encryption that is impossible to decrypt on your own, urging the victim to send a payment to a Bitcoin wallet or to contact the hackers via email on a ProtonMail address. We’ve checked one of the Bitcoin wallets that are used in this campaign, and, thankfully, there have been no payments made to it. However, it is almost certain that malicious actors aren’t using only one wallet and one email address.
While the "CoronaVirus" ransomware may steal the spotlight due to the trendy name and the trouble that it can cause, it is the KPot that causes all this trouble. To stay safe from it, don’t download files from obscure websites, don’t download and execute email attachments, don’t follow URLs shared through unsolicited messages, and make sure that you’re using an up to date anti-virus solution from a reputable vendor.