Major Cloud Password Managers Vulnerable to Recovery Attacks: Bitwarden, LastPass, and Dashlane
- Significant Flaws: An academic study has systematically identified 25 distinct attack vectors targeting password recovery mechanisms in major cloud-based password managers.
- Vulnerability Target: Vulnerabilities were identified in the account recovery protocols of these services, which are designed to restore user access when master password authentication fails.
- High-Stakes Compromise: Successful exploitation enables adversaries to achieve complete compromise of a user's credential vault, bypassing primary authentication controls.
Bitwarden, LastPass, and Dashlane – three leading cloud-based password managers that claim to use Zero-Knowledge Encryption – account recovery flaws were identified by security researchers. An additional analysis of 1Password led to the identification of 27 distinct attacks that a malicious server can mount against its users.
Technical Analysis of Password Recovery Attack Mechanisms
The ETH Zurich researchers’ methodology focused on documenting cloud password manager vulnerabilities, which originated from implementation weaknesses in identity verification protocols, cryptographic secret distribution, and access restoration procedures.
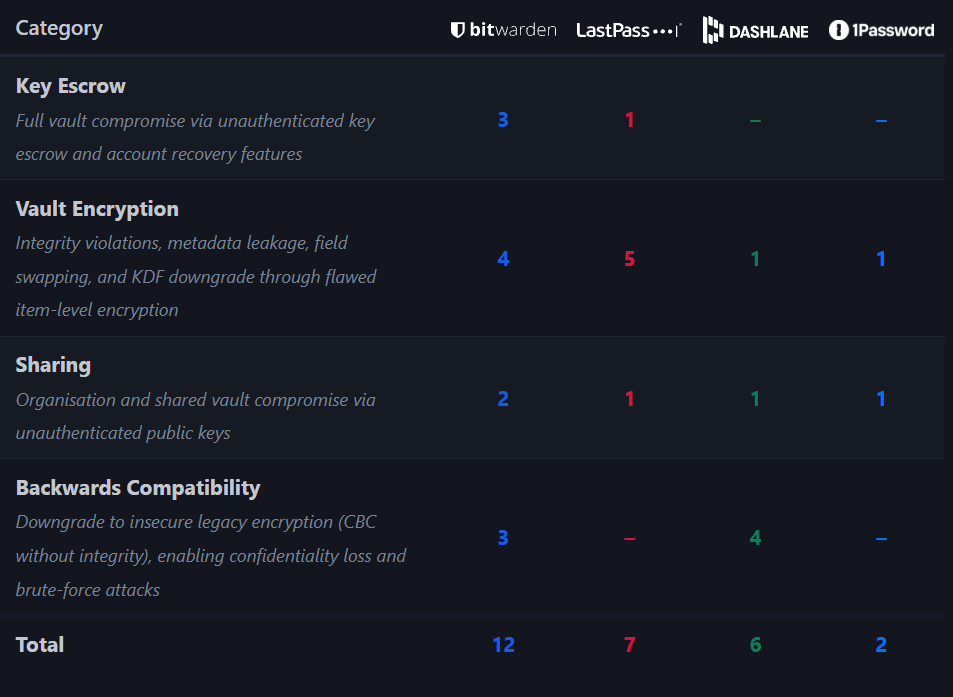
Bitwarden, which allows self-hosting and uses AES-CBC-HMAC for authenticated encryption of vault data, encrypts items separately. A malicious server could execute cut-and-paste attacks, leak metadata, or exploit the organization and key recovery features to steal vault data.
Researchers report that LastPass employs AES-CBC per-item encryption without integrity protection and is vulnerable to cut-and-paste attacks and metadata leakage. “We could not find an exploitable padding oracle, but the key recovery feature would allow a malicious server to trivially recover an entire vault.”
Dashlane’s vault content is encrypted using keys derived from the master password, using AES-256 in CBC mode with HMAC. Researchers leveraged legacy support for CBC mode without HMAC to develop an entire attack chain based on a padding oracle through a long-running, targeted attack.
1Password’s brute-forcing-proof two-secret approach consists of a master password and a 128-bit secret key. The AES-GCM encryption, with RSA-OAEP for key wrapping, lacks RSA-OAEP ciphertext authentication, thereby allowing the swapping of users' vaults with those controlled by a malicious server.
Risk Assessment and Industry Security Implications
The severity of the attacks ranges from integrity violations to the complete compromise of all vaults in an organisation. Successful vault compromise provides adversaries with comprehensive access to users' complete digital authentication infrastructure.
Adversaries who gain control of associated email accounts can exploit protocol weaknesses to initiate unauthorized password resets and compromise the entire vault, thereby fundamentally undermining the security model of these authentication systems.
In January, a LastPass phishing campaign used deceptive requests targeting password vaults. A report last month found that remote access compromise, phishing, social engineering, and rapid flaw exploitation are the primary ransomware attack vectors.