New MacOS Malware Abuses Disclosed Vulnerability that Apple Won’t Fix
- A MacOS malware based on a zero-day that Apple won't fix is out there already.
- The malware came about a month after the disclosure of the flaw and the associated proof of concept code.
- The massive distribution campaigns are not underway yet, but they may soon go full-on.
A new Mac malware that goes by the name "OSX/Linker" has appeared in the wild, abusing a vulnerability that was publicly disclosed last month by Italian security researcher Filippo Cavallarin. The researcher demonstrated how to exploit the zero-day through a video, creating a zip archive that contained symbolic links pointing to automount endpoints that the attacker controls. This takes the victim to a location that was never checked and approved by Gatekeeper, yet can contain and execute malicious code onto the target machine. The researcher sent the proof of concept code to Apple in February, but they never took it seriously.
On version 10.14.4, Apple claimed that they had fixed Gatekeeper bypassing problems, yet further tests revealed that the problem persisted and was still exploitable. With all the details out there, it was only a matter of time before a malicious actor took note of the PoC and created a malware that abuses the disclosed issue. According to Joshua Long, an experienced Apple security researcher who has been following this new malware, someone from the Intego team noticed the first samples of the OSX/Linker early at the beginning of this month, so we're already past the testing and payload refinement stage.
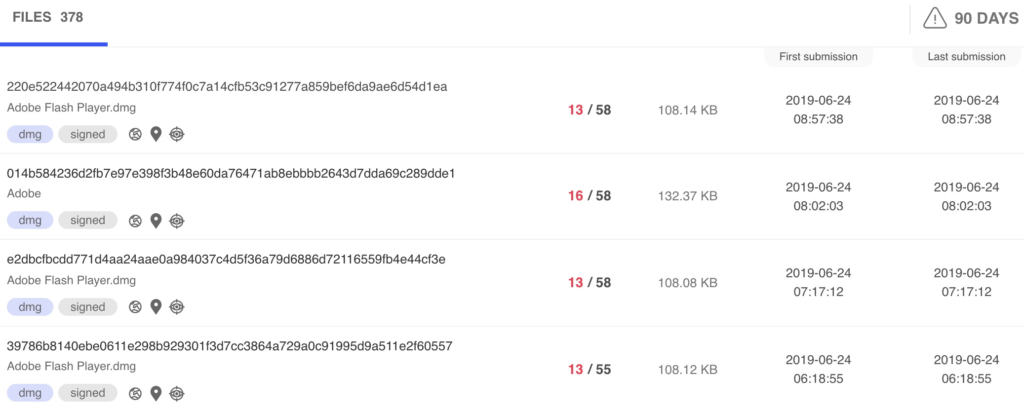
image source: intego.com
The malware is signed with certificates previously used by the Surfbuyer adware group, so this latest piece of menace most likely comes from experienced actors. The malware utilizes disk image files and a modified version of Cavallarin's PoC, containing the payload and supposedly Adobe Flash Player installers. While the disk images are no longer to be spotted in the wild, it is possible that the researcher has missed small-scale distribution campaigns that may be going on right now. The samples that were analyzed were signed by a compromised Apple Developer ID that Apple is yet to revoke.
So, if Apple won't plug this vulnerability even after a full month following its disclosure, then what can you do in order to stay safe? One way is to lock down your network to prevent NFS communications with external IP addresses. Another solution is to disable the automount functionality on your system, preventing these nasty images from getting mounted. To do this, edit "/etc/auto_master" as root, comment the line beginning with "/net", and reboot. For this to work, you will first need to disable the SIP (System Integrity Protection). All in all, Apple really needs to fix this, but first, they need to stop denying or ignoring the flaw exists in the first place.
What are you planning to do about the particular vulnerability? Share your thoughts in the comments section beneath, or on our socials, on Facebook and Twitter.