Lunar Spider Leveraged Latrodectus, Brute Ratel C4, Cobalt Strike, and Custom Backdoor in 2-Month Network Intrusion
- Initial access: A single click on a malicious JavaScript file disguised as a tax form ultimately deployed Brute Ratel malware.
- Multi-payload attack: Latrodectus, Cobalt Strike beacons, and a custom .NET backdoor were used to maintain access and escalate privileges.
- Extended dwell time: The attackers remained within the network for nearly two months before being evicted.
A sophisticated Lunar Spider social engineering operation utilized tax lures to install Brute Ratel malware and Latrodectus malware, conducting reconnaissance, moving laterally, and exfiltrating data. This incident highlights the effectiveness of social engineering as an initial access vector for advanced persistent threat groups.
Attack Vector and Initial Compromise
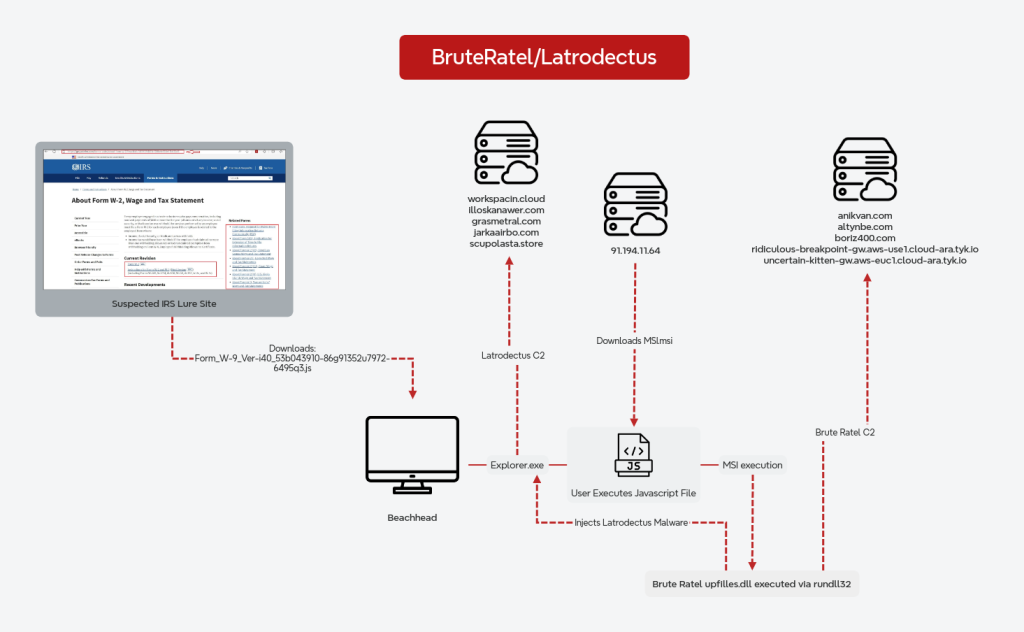
The intrusion began with opening a fake tax form attachment that executed a heavily obfuscated JavaScript file, which was previously associated with the Lunar Spider group by EclecticIQ.
This initial action triggered the download of an MSI package that installed Brute Ratel malware, a recent The DFIR Report analysis details.
The loader then injected the Latrodectus malware, designed to download payloads and execute arbitrary commands, into the explorer.exe process. A Latrodectus Stealer module was also used in the attack, harvesting credentials from 29 Chromium-based browsers, including Google Chrome, Microsoft Edge, and Epic Privacy Browser.
It extracted email credentials from Microsoft Outlook configurations across Office versions 11.0-17.0, server configurations, port numbers, usernames, encrypted passwords, legacy email configurations from older Windows Mail, Outlook Express, and MAPI profiles that may contain additional cached credentials..
Timeline and Techniques Employed
The cyberattack timeline shows rapid escalation following the initial breach. Within hours, the threat actor conducted host and domain enumeration. By day three, they discovered plaintext domain administrator credentials in a Windows Answer file, granting them immediate high-privilege access.
On day four, the actor deployed and executed a binary named lsassa.exe via BackConnect, which was a .NET backdoor containing an encrypted payload embedded in an assembly resource file. This action established command and control (C2) and initiated a nearly two-month-long compromise of the target network.
Several Cobalt Strike beacons were also deployed, with the first observed on day four. One implant initiated a UAC bypass, achieving privilege escalation without user interaction, via a well-documented registry hijacking method first observed in 2017 that exploits the UAC token duplication vulnerability. This allowed the Cobalt Strike implant to execute arbitrary code.
The actors moved laterally using PsExec to compromise a domain controller and other critical servers. Data exfiltration using Rclone occurred on day 20, demonstrating the patient and methodical nature of the attack.
Cybersecurity Implications of the Intrusion
The actor’s ability to remain undetected for almost two months while deploying multiple malware payloads demonstrates a high level of operational security and adaptability.
The successful credential harvesting from an unsecured configuration file also serves as a critical reminder of the importance of secure system provisioning and eliminating plaintext credentials.
The report concludes that despite extensive access, no ransomware was deployed, suggesting the primary objective may have been data theft and persistent access.
This month, Zscaler cybersecurity researchers linked the YiBackdoor malware family to IcedID and Latrodectus. The latter was created by the developers of IcedID and is actively being developed, with updates to its encryption key pattern and new commands.
In August 2024, a Google Safety Centre phishing operation deployed Latrodectus and ACR Stealer disguised as Google Authenticator. During Operation Endgame, which occurred in May 2024, law enforcement dismantled multiple botnets.