LogoKit Phishing Kit Targets Government, Banking, and Logistics Sectors
- A new wave of phishing pages impersonating legitimate entities leverages LogoKit.
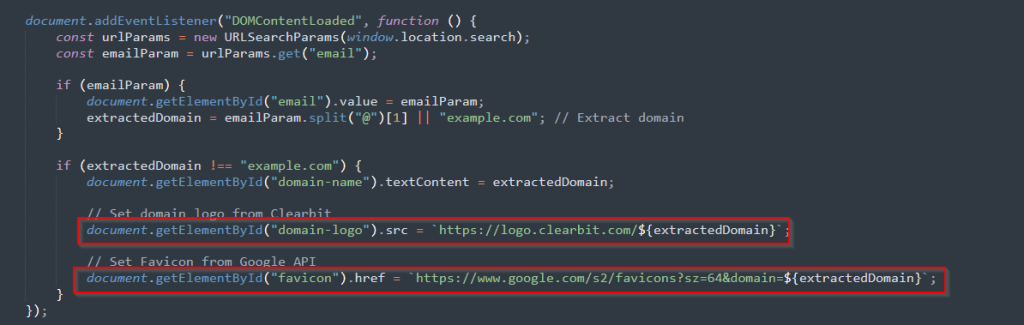
- Attackers fetch targeted companies’ branding elements in real-time via Clearbit Logo API and Google S2 Favicon.
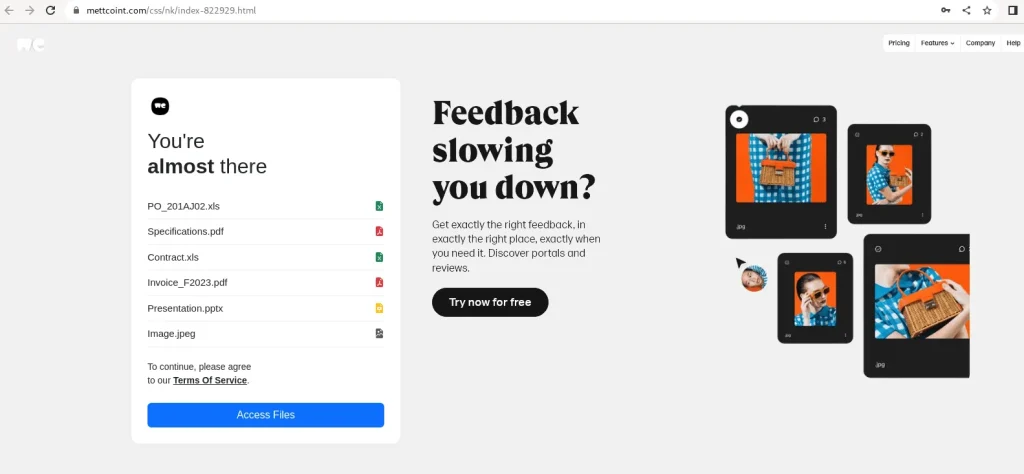
- Hungary’s HunCERT, WeTransfer, Kina Bank in Papua New Guinea, and the U.S. Catholic Church are among the targets.
The LogoKit phishing kit has emerged as a significant tool in a new wave of phishing attacks, targeting organizations across the government, banking, and logistics sectors globally with enhanced deception and effectiveness, posing serious risks to users and organizations alike.
Among the features of the LogoKit Phishing Kit are simplicity and automation, allowing cybercriminals to quickly customize phishing pages and steal credentials.
According to a detailed report by Cyble, the kit integrates services like Clearbit Logo API and Google S2 Favicon to fetch targeted companies’ branding elements in real-time.
By embedding users’ email addresses directly into phishing links, LogoKit further personalizes its attack, fostering a false sense of legitimacy that increases the likelihood of credential theft.
Phishing pages generated using LogoKit are hosted on publicly trusted platforms such as Amazon S3, leveraging their credibility to evade detection.
Additionally, some of these sites implement Cloudflare Turnstile verification, adding another layer of perceived authenticity to deceive users. Victims are typically drawn to these fraudulent pages through convincingly crafted emails that mimic trusted entities, such as government security agencies or financial institutions.
Cyble researchers also revealed the Impact of LogoKit-based attacks. For example, phishing links impersonated Hungary’s HunCERT security team, with pre-filled login fields designed to appear genuine.
Beyond the government space, Kina Bank in Papua New Guinea, the Catholic Church in the United States, and logistics companies in Saudi Arabia have also been confirmed targets. WeTransfer was also among the impersonated brands.
These campaigns aim to harvest sensitive credentials, which are then sent to attacker-controlled servers. Reports indicate that harvested data is stored in open directory paths accessible for further exploitation.
The continued use of undetected domains and the expansion of LogoKit’s reach reveal its scale and efficacy in accessing critical organizational systems.
Cybersecurity best practices for organizations include robust cybersecurity measures to defend against phishing kits like LogoKit. Regular employee training on identifying phishing scams, coupled with ongoing monitoring for suspicious activity, is equally critical.