LockerGoga on the Spotlight, Dubbing as Wiper and Ransomware
- LockerGoga is not only encrypting the victim’s files anymore, but it’s also locking the user out.
- The Talos team has noticed a cumbersome encryption process, which includes the Recycle Bin as well.
- The ransom note won’t ask for money directly but instead consults the victim to send an email to the attacker.
The Cisco Talos Intelligence team puts the LockerGoga ransomware on their spotlight, following the recent successful attack on Norsk Hydro that proved how unsophisticated ransomware tools can still be highly destructive. Fresh versions of the LockerGoga have been noticed by the team in the wild, featuring a new “locking-out” mechanism for the victims, preventing them any access to the infected system, the encrypted files, and even the ransom notes. The main focus of this new LockerGoga spin is to wreak havoc, rather than allow the victim to pay the ransom and get their files back.
The Talos team noticed that LockerGoga uses a valid certificate issued by Sectigo, so as to avoid anti-malware detection in most cases. The certificate has now been revoked, but the ransomware still makes use of it, taking its chances against non-updated anti-virus tools. The process of infection goes as follows: the LockerGoga executable is copied to the %TEMP% directory and executed, the Windows Event Logs directory is wiped, a ransom note is created, and the encryption process is initiated. The original files are deleted, and encrypted clones take their place in the system’s disks. LockerGoga doesn’t forget about the Recycle Bin, a location that many uses as a short-term backup.
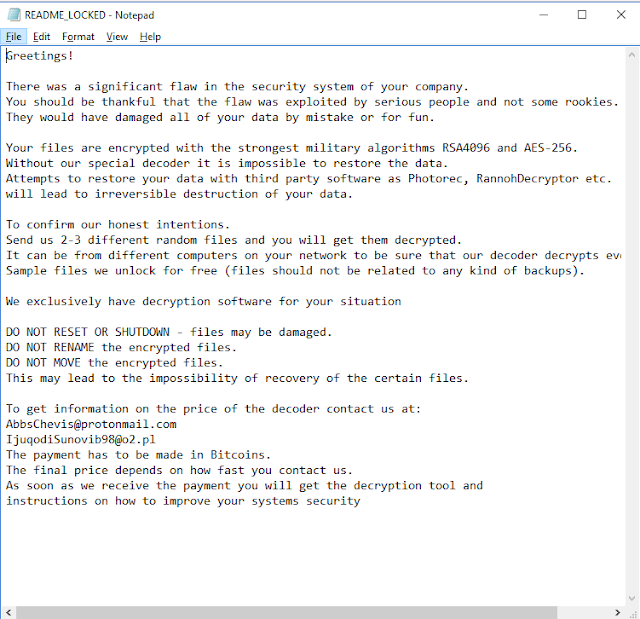
Something that is indicative of the lack of sophistication is the fact that LockerGoga is attempting to encrypt each file separately, a process that is highly inefficient. The resulting ransom note claims that the attackers are “serious people”, and that the encryption of the system files was done by using military-grade algorithms of the like of RSA4096 and AES-256. This is to discourage the victim from trying various solutions, as every attempt to restore the encrypted files, move them, rename them, or even shut down the system could lead to the data becoming non-recoverable. No price is given for the decryptor, but only a contact email address which the Talos team found to differentiate across multiple samples.
source: blog.talosintelligence.com
The researchers claim that there is no evidence to suggest that LockerGoga possesses the ability to propagate across hosts on an infiltrated network and that there appears to be no dedicated C2 server. Considering the widespread infection of Norsk Hydro, maybe the attackers were using a custom iteration of LockerGoga, managing to propagate it on multiple production units in different countries, after compromising the company’s main network. The locking-out part is compatible with the rest of the story, as the company hasn’t announced the payment of a ransom.
Care about sharing your views on the above? Feel free to do so in the comments section below, and don’t forget to like and subscribe on our socials, on Facebook and Twitter.