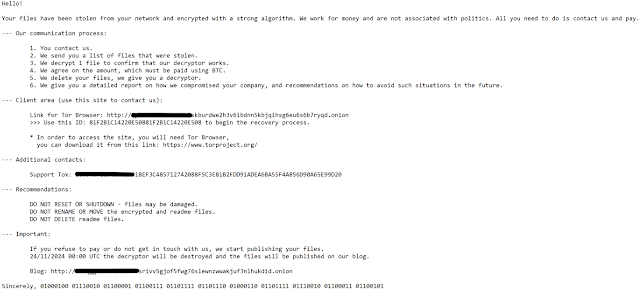
LockBit, Conti TTPs Leveraged by DragonForce in Latest Ransomware Attacks
- DragonForce ransomware started mixing payloads derived from Conti and leaked LockBit 3.0 source code.
- The new ransomware attacks use the "stack strings" obfuscation technique and log activity in an encrypted Public directory log file.
- Proven encryption methods are used, like the ChaCha8 algorithm for file encryption, as well as obfuscation and targeting strategies.
The DragonForce threat group integrates both LockBit and Conti ransomware into its arsenal. This concerning development has rapidly escalated the group's capabilities, signaling increased risks for organizations globally.
DragonForce, a hacktivist collective previously associated with politically motivated cyberattacks, has demonstrated a significant shift in its operational tactics. Adopting LockBit and Conti ransomware strains effectively combines two of the most potent ransomware threats tracked in recent history.
The DragonForce sample analyzed by Hybrid Analysis combines proven encryption methods like the ChaCha8 algorithm for file encryption, with the encryption key and nonce protected by the public RSA key.
Both LockBit and Conti are highly advanced ransomware-as-a-service (RaaS) platforms known for their targeted attacks and data encryption efficiency.
Industry experts note that this development blurs traditional distinctions between hacktivism and financially motivated cybercrime.
The blending of these ransomware variants enables DragonForce to conduct high-impact attacks that disrupt operations while also extracting ransom payments.
LockBit is recognized for its autonomous encryption process, which has made it a preferred tool for rapid deployment across networks. Additionally, its customizable ransom notes and self-spreading capabilities make it particularly challenging to counteract.
Conti, on the other hand, has built a notorious reputation for its double-extortion tactics, where sensitive data is both encrypted and threatened with public exposure. Its advanced encryption algorithms and exceedingly fast propagation mechanisms further amplify its destructive potential.
By weaponizing these two strains simultaneously, DragonForce ransomware appears to be targeting vulnerable sectors and profiting from ransom demands while aligning itself with its hacktivist origins.
Law enforcement shut down LockBit's infrastructure in February 2024 in Operation Cronos, seizing several servers with decryption keys. This led to the progressive acquisition of approximately 7,000 LockBit keys that the FBI offered for free to U.S. and international victims.