Latest LibreOffice Version Still Vulnerable to Malware-Dropping Documents
- LibreOffice thought they’d fixed a severe code execution vulnerability, but it looks like there’s still a way.
- An independent reporter bypassed the fix in the latest version of the office suite, so the developers will have to work on a fix quickly.
- People are urged to install LibreOffice by excluding the vulnerable component.
Recently, LibreOffice released 6.2.5, addressing two severe vulnerabilities (CVE-2019-9848 and CVE-2019-9849), allegedly plugging a code execution flaw that could result in a malware infection following the opening of a specially crafted document. While the developers of the popular open-source office suite thought that they had dodged that bullet, but a security researcher named Alex Inführ came on Twitter and announced that he had successfully bypassed the fix of CVE-2019-9848 in LibreOffice 6.2.5, the latest available and patched version.
Bypassed successfully the fix of CVE-2019-9848 in LibreOffice 6.2.5. It's time to write a new email 🙂
— alex (@insertScript) July 26, 2019
Obviously, while fixing something means that a known way to exploit a vulnerability is addressed, there can be other ways through which an attacker could reach the same results. Moreover, there’s always the chance of a fix introducing a new way to exploit the plugged flaw. Mr. Inführ has not provided any details on how he managed to bypass LibreOffice’s fix, as this would risk the security of more than 200 million people who are currently using the open-source productivity suite.
CVE-2018-9848 concerns the LibreOffice programmable turtle vector graphics script, which apparently can be manipulated into executing arbitrary python commands. An attacker can exploit the document event feature to trigger LibreLogo and execute malicious code that is embedded in a specially crafted document. From there, the python commands are executed silently and without the user getting any warnings or being asked for their permission. Accepting that the flaw hasn’t been fixed even in the latest version, it affects the current and all previous versions of the office suite.
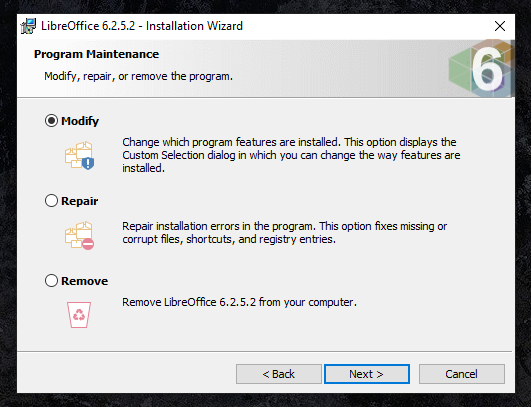
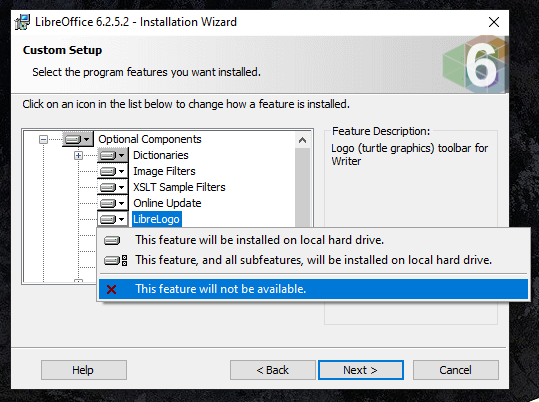
If that is the case, then what can people do about it? Until LibreOffice releases a new fix that addresses Inführ’s bypassing method, we may install the suite by excluding the “LibreLogo” component. You can select what components you want to install by selecting “custom” installation, expand the “optional components” list, and then click on the disk icon to deselect the “LibreLogo” component. If you already have LibreOffice installed on your computer, you may re-run the installer and choose the "modify" option as seen below.
There have been no known cases of exploitation based on the aforementioned vulnerability yet, and the upcoming proactive fixing goes to show that open source software like LibreOffice is still adequately supported by a vivid community of testers and reporters. With Microsoft Office counting over 1.2 billion users, it remains the number one target for malicious actors right now, but as the LibreOffice userbase grows, it will receive an equally increasing attention from hackers.
Are you using LibreOffice or do you still prefer another office suite? Let us know what your choice is in the comments below, and help us spread the word of warning by sharing this post through our socials, on Facebook and Twitter.