Lazarus Subgroup Deploys Three Advanced RATs in Cryptocurrency and Financial Sector Attacks
- Lazarus RATs: A Lazarus subgroup was seen targeting the financial sector with PondRAT, ThemeForestRAT, and RemotePE.
- Trading firm impersonation: Attackers impersonate trading company employees via social engineering tactics targeting crypto users.
- Powerful RAT: RemotePE features over 20 command functions and is compatible with Windows, Linux, and macOS.
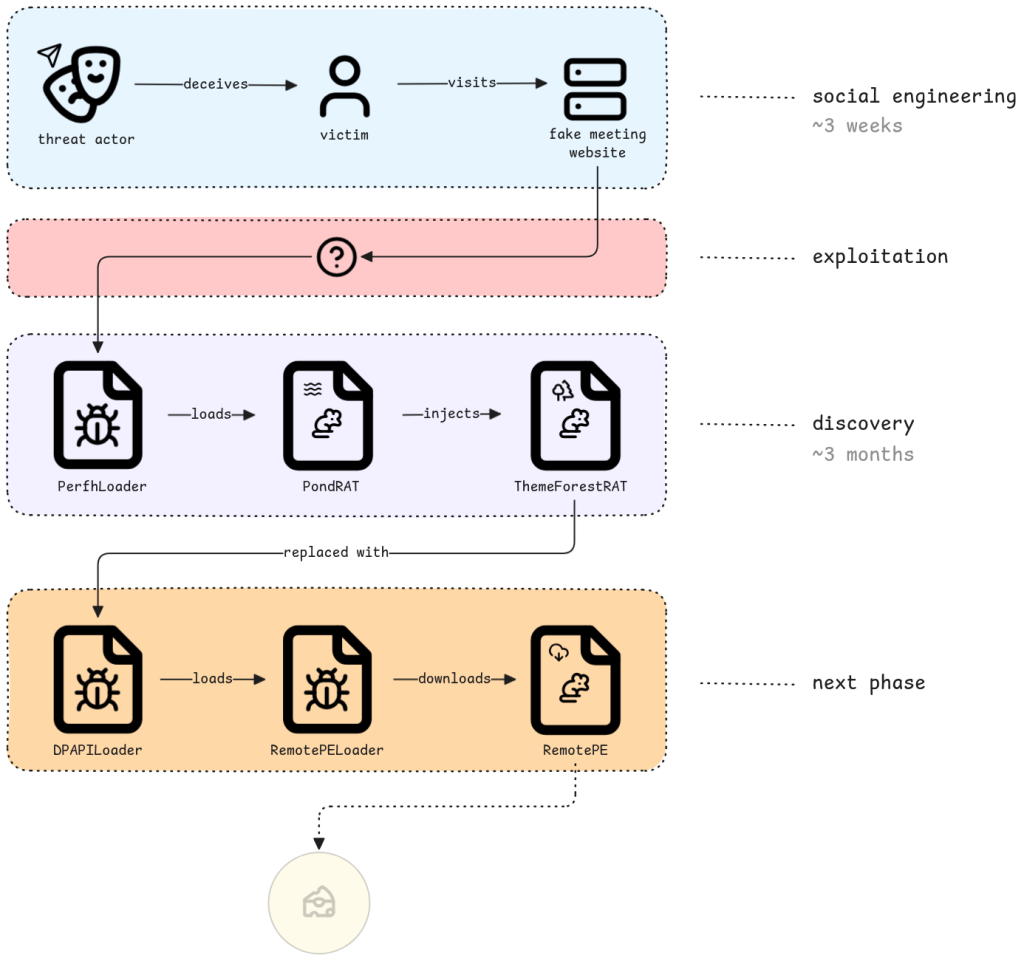
A sophisticated campaign by the Lazarus subgroup RATs targets organizations in the financial and cryptocurrency sectors. The coordinated use of three remote access trojans (RATs) – PondRAT, ThemeForestRAT, and RemotePE – was identified, demonstrating the North Korean-linked group's evolving cyber capabilities.
Multi-Stage Attack Framework
The PondRAT malware serves as the initial access payload in these operations, functioning as a simplified RAT with basic file manipulation and process execution capabilities, NCC Group’s Fox-IT researchers have documented.
This Lazarus subgroup overlaps with activity linked to AppleJeus1, Citrine Sleet2, UNC47363, and Gleaming Pisces4, according to the report.
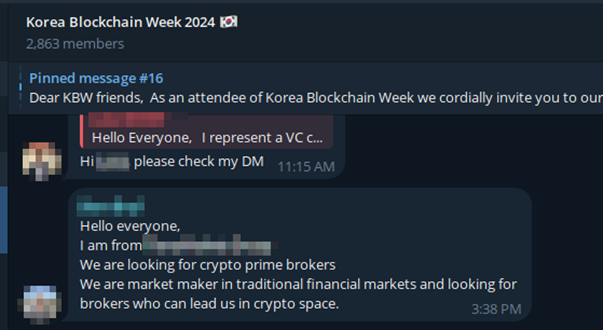
The campaign begins with social engineering tactics, where attackers impersonate existing employees of a trading company on Telegram, using fake meeting websites to establish contact with victims in the cryptocurrency sector.
Researchers suspect that Chrome zero-day exploits may facilitate initial compromise, followed by months-long reconnaissance activities using various credential-harvesting and proxy tools.
Security researchers identified PondRAT samples dating back to 2021, with the malware utilizing XOR encryption and Base64 encoding for command-and-control communications over HTTP/HTTPS protocols.
Operating in conjunction with PondRAT, ThemeForestRAT analysis reveals a more sophisticated tool that has remained operational for at least six years without public documentation.
This Windows, Linux, and macOS-compatible RAT features over 20 command functions, including file management, process monitoring, and shellcode injection capabilities. The malware employs RC4 encryption for configuration files and uses hibernation periods between command and control (C2) sessions to avoid detection.
Advanced Persistence Mechanisms
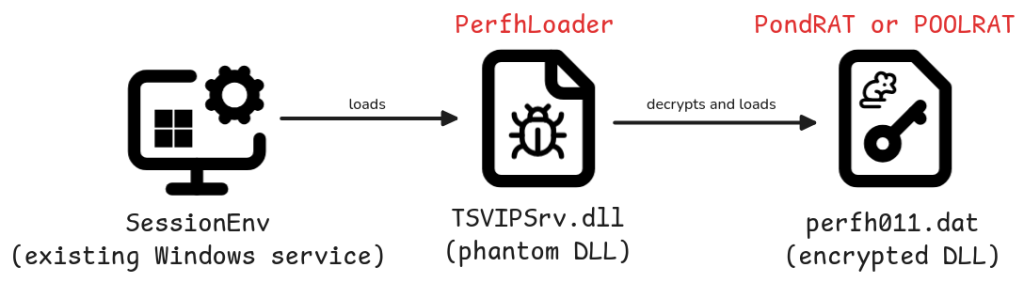
Lazarus group attackers leverage phantom DLL loading techniques through Windows services, specifically targeting the SessionEnv service for persistence.
Custom loaders, such as PerfHLoader, decrypt and execute payloads stored as seemingly legitimate Windows Performance Monitor files, demonstrating sophisticated evasion tactics.
Next-Generation Threat: RemotePE
The RemotePE cybersecurity threat represents the campaign's final stage, deployed after the actors have removed the PondRAT and ThemeForestRAT artifacts. This advanced RAT utilizes Windows Data Protection API (DPAPI) for environmental keying, making analysis difficult without access to the compromised machine.
The malware's C++ architecture and elegant design suggest it was designed for deployment against high-value targets that require enhanced operational security.
This multi-RAT approach demonstrates Lazarus Group's commitment to long-term access and highlights the persistent threat facing financial institutions and cryptocurrency organizations worldwide.
In other recent news, Lazarus Group’s “Operation SyncHole” targeted at least six South Korean entities.