Lazarus Group Targets UAV Sector in Cyberespionage Operation DreamJob Focusing on Drones
- Targeted espionage: The North Korea-aligned Lazarus Group is targeting European defense companies, specifically those involved in the UAV sector.
- Proven tactics: The attacks are part of the long-running "Operation DreamJob," which uses fake job offers and social engineering to gain initial access.
- Primary malware: The main payload deployed is the ScoringMathTea RAT, giving attackers full control over compromised systems to exfiltrate proprietary information.
A recent cyberespionage campaign attributed to the Lazarus Group is actively targeting European defense companies, with a specific focus on the Unmanned Aerial Vehicle (UAV) sector, as part of a new wave of "Operation DreamJob," a series of sophisticated attacks linked to North Korean state-sponsored actors.
The campaign's objective is likely the theft of intellectual property and manufacturing know-how, aligning with North Korea's reported efforts to advance its domestic drone program through reverse engineering and intelligence gathering.
Attack Methodology and Malware Deployed
The Lazarus Group UAV attack leverages social engineering as its primary initial access vector, ESET security researchers have identified.
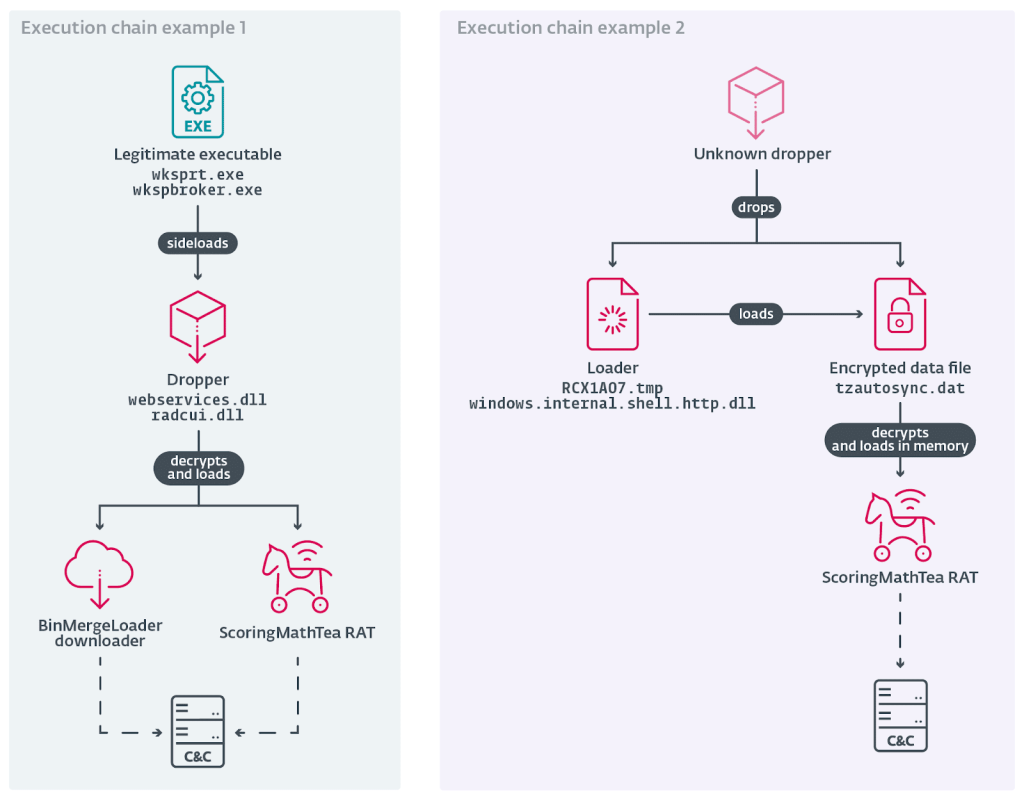
Targets receive fake, yet lucrative, job offers that include a decoy document and a trojanized application, such as a PDF reader, needed to view it. Once executed, the malware initiates a multi-stage infection chain.
This process often involves DLL side-loading and the use of trojanized open-source projects to evade detection.
The ultimate payload deployed in the observed attacks is ScoringMathTea, a complex Remote Access Trojan (RAT) that grants the attackers comprehensive control over the compromised machine for data exfiltration and further post-exploitation activities.
A trojanized MuPDF reader, QuanPinLoader, a loader disguised as a Microsoft DirectInput library, and a variant of ScoringMathTea were submitted to VirusTotal from Italy in April and June 2025, and BinMergeLoader from Spain in August 2025.
In some cases, the attackers also deployed a complex downloader similar to the MISTPEN malware that Mandiant reported, which leverages the Microsoft Graph API and Microsoft API tokens.
Geopolitical Context and Cybersecurity Implications
This campaign underscores the persistent threat of North Korea cyberattacks against strategic industries. The targeting of companies involved in UAV technology is significant, given North Korea's documented interest in mimicking Western drone designs like the MQ-9 Reaper and RQ-4 Global Hawk.
By stealing sensitive data, the Lazarus Group can directly support its nation's military and industrial objectives.
The consistent use of the Operation DreamJob framework, despite widespread reporting, indicates its continued effectiveness and highlights the ongoing need for heightened security awareness and robust defenses within the aerospace and defense sectors.
Last month, a Lazarus subgroup deployed three advanced RATs in cryptocurrency and financial sector attacks, and a Lazarus Group ‘Operation SyncHole’ targeted at least six South Korean entities in April.