KT Telco Femtocell Flaws Exposed Customers to Fraud, South Korean Police Arrested Five Individuals
- Security Failures: Korea Telecom femtocells were deployed with security oversights, recent discoveries say.
- Customer Impact: Flaws allowed attackers to clone the devices, intercept customer communications, and perpetrate micropayment fraud totaling $169,000.
- Government Intervention: South Korea’s police have issued 13 arrest warrants in connection with a gang exploiting the flaws.
South Korean carrier Korea Telecom (KT) is facing scrutiny after the Ministry of Science and ICT found severe security deficiencies in its femtocell devices. These small, in-home base stations, intended to improve mobile coverage, were deployed with security oversights. An investigation into these flaws led to the arrest of five individuals.
The Ministry of Science and ICT investigation results were also found in an analysis from Korean infosec academic and IEEE Fellow Yongdae Kim, who discovered that femtocells were deployed without a root password, plaintext security keys, and a single shared authentication certificate.
KT Femtocell Vulnerabilities
The devices lacked root passwords, stored critical authentication keys in plaintext, and enabled remote SSH access by default. Most significantly, all deployed femtocells used the same digital certificate for network authentication, which had a ten-year validity period.
These femtocell vulnerabilities enabled threat actors to easily access devices, extract certificates, and create cloned femtocells that KT's network would recognize as legitimate. A police report stated that KT announced it had discovered 20 illegal femtocell IDs through an investigation conducted from August 1, 2024, to September 10, 2025.
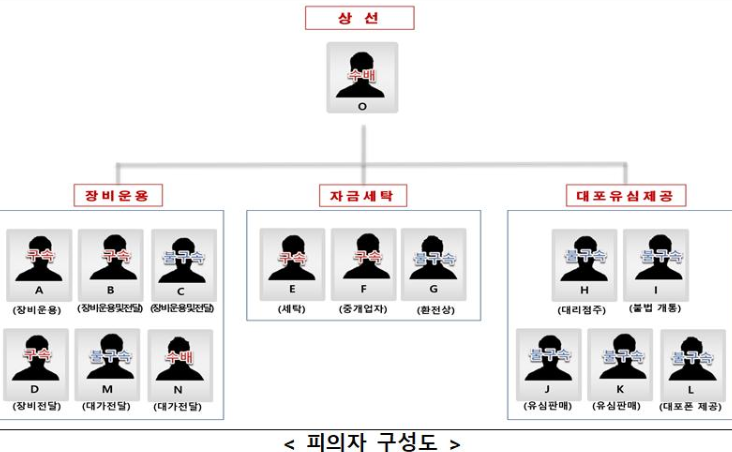
The South Korea KT security incident prompted a significant response from authorities. Two individuals are wanted in connection with a KT mobile phone fraudulent payment multiple-victim case, and 13 suspects have arrest warrants (of which five have been arrested):
- 5 suspects involved in the operation (such as equipment supply),
- 3 suspects who laundered money by cashing and exchanging gift certificates,
- 5 suspects who opened or provided fake phones using stolen identities.
Authorities secured 31 pieces of equipment, including 2 femtocells, 5 routers, directional antennas, and accessories. The police report said that analysis of the illegal femtocell revealed electronic information related to the crime, such as:
- KT certificates,
- KT authentication server IP,
- cell ID used in the crime,
- administrator access IP,
- packet transmission software.
The individuals were allegedly part of a gang that was "war-driving" with cloned femtocells to expand their reach. One of the cloned devices was traced back to a certificate taken from a unit that was confirmed to have been lost during a Korean military barracks relocation around January 2020, according to the police.
Micropayment Fraud and Surveillance Risks
The consequences of the KT Telecom femtocell security failures have been substantial. Attackers leveraged the cloned devices to intercept customer communications, including text messages and call logs, which facilitated a large-scale micropayment fraud scheme.
By intercepting SMS messages, the attackers were able to exploit KT’s SMS-based payment service for digital content. Investigations have so far linked the fraudulent activity to at least 368 victims, resulting in financial losses of $169,000.
However, authorities said the total impact could be greater, as attackers may have been conducting surveillance for years before the fraud was detected.
South Korea Regulatory Response
In response to the findings, the South Korean government has mandated that KT must allow affected customers to terminate their contracts without penalty.
Today, the Korean police published a press release announcing the arrest of a hacker in connection with a KMSAuto clipper malware campaign. In July, South Korea's Ministry of Science and ICT announced a penalty of 30 million won (approximately $21,970) against SK Telecom, another large mobile carrier, for suffering a data breach.
This month, Polish police arrested three Ukrainian nationals who were found in possession of computer hacking equipment, including FLIPPER hacking devices, laptops, routers, and antennas, and charged them with offenses linked to national defense.