Kimsuky APT Hackers Exposed in Alleged Breach Revealing Phishing Tools and Operational Data
- Exposed hackers: Two cybercriminals leaked a data dump belonging to the North Korean state-sponsored hacker group Kimsuky.
- What was published: The leaked data reportedly reveals the threat actor’s infrastructure and tactics.
- The reasons: This move was allegedly motivated by ethical reasons, as the two hackers’ values do not align with Kimsuky’s “greed.”
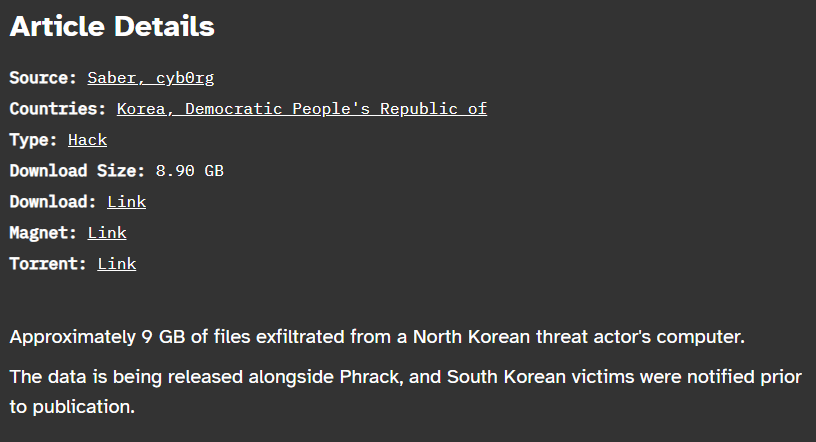
Kimsuky data breach reports reveal sensitive details about the North Korean Advanced Persistent Threat (APT) group. Two hackers, "Saber" and "cyb0rg," disclosed an 8.9 GB dump of the threat actor’s backend data, spotlighting their infrastructure and tactics.
Known for espionage operations targeting South Korea and global entities, Kimsuky has now become the target, as the two hackers accused the gang of being “driven by financial greed” and “hacking for all the wrong reasons.”
Details of the Leak
The data, accessible via the Distributed Denial of Secrets platform, reportedly reveals the group’s phishing tools, source codes, and operational logs. Key elements include phishing kits targeting South Korean government domains, such as spo.go.kr, and the source code of Korea's Ministry of Foreign Affairs email platform.
Additionally, the dump exposes Cobalt Strike loaders, reverse shells, SSH activity logs, and private certificates, as well as unknown binary archives and executables. Linked findings also document connections to GitHub accounts, VPN purchases through Google Pay, and the group’s use of hacking forums.
Such revelations confirm the North Korean state-sponsored APT group’s sophisticated methods, indicating a seamless integration of data theft, malware distribution, and remote exploitation.
Implications of the Exposure
The data breach effectively "burns" parts of Kimsuky’s APT infrastructure, potentially hampering ongoing campaigns and exposing operational methods. However, while this move may suggest temporary setbacks for the group, longer-term disruption in their capabilities is uncertain.
This potential APT infrastructure leak also provides significant intelligence for cybersecurity analysts, empowering defensive strategies and future countermeasures.
This month, TechNadu reported on a continued Kimsuky campaign targeting South Korea with official-looking phishing lures.