Kimsuky APT Continues Targeting South Korea with Official-Looking Phishing Lures
- Continued campaign: Kimsuky allegedly continues to focus on phishing emails that deploy malware via official-looking lures.
- Official lures: The threat actor uses legitimate public safety notifications and local tax notice templates for credibility and urgent engagement.
- Targets: The repurposed documents show a calculated focus on South Korean individuals and institutions.
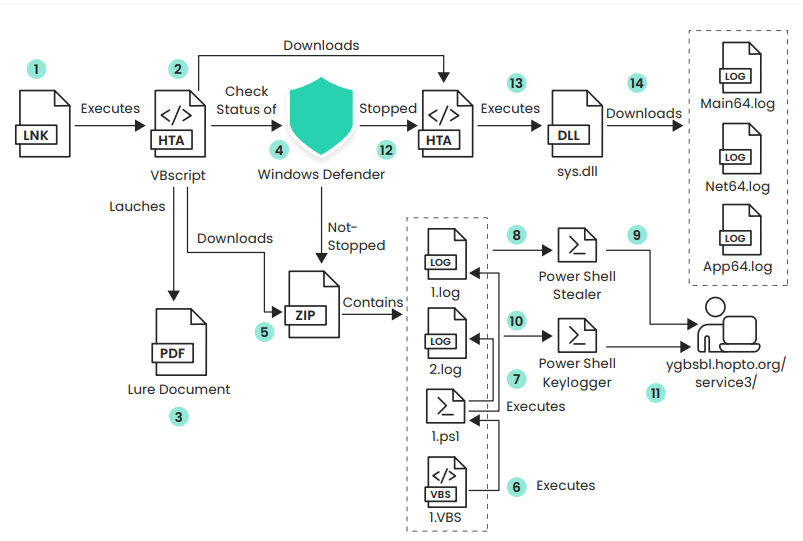
The Kimsuky APT group continues to deploy a campaign targeting South Korea with spear-phishing emails containing malicious shortcut files, as recently analyzed tactics, techniques, and procedures (TTPs) strongly resemble those attributed to this North Korean state-sponsored cyber-espionage operation.
The campaign exhibits a blend of social engineering, modular malware tactics, and data exfiltration strategies reportedly aimed at collecting geopolitical and technological intelligence, amid ongoing tensions between North Korea and South Korea.
Sophisticated Tactics and Tools
Known for targeting South Korean government agencies, defense contractors, and research institutions, the Kimsuky advanced persistent threat (APT), also tracked as APT43, Thallium, and Velvet Chollima, employs spear-phishing emails containing malicious LNK files in a continued campaign observed in a recent Aryaka security report.
These files execute obfuscated scripts that deploy multi-stage malware frameworks, as they launch HTA files hosted on a remote Content Delivery Network (CDN), which execute with full system privileges.
Decoy PDF documents, often based on publicly available South Korean government materials, lure victims into opening these files, which often masquerade as official government notices on a nearby sex offender, sometimes as an official tax or penalty notice PDF that warns about an alleged fine.
The malware utilizes PowerShell scripts for dynamic execution, evading traditional detection by employing anti-virtualization checks (for VMware, Microsoft, or VirtualBox) and obfuscation techniques.
It systematically harvests sensitive information, including credentials stored in web browsers, user activity logs via keylogging, and high-value documents, which are exfiltrated to the attackers’ command-and-control (C2) in discrete segments over regular network traffic, blending seamlessly with legitimate activities.
The dynamic interaction with the C2 server involves retrieving C2 files, delivering payloads, executing remote commands, and downloading subsequent payloads.
Strategic Targeting
Focusing primarily on South Korean institutions, Kimsuky also extends its reach to civilians, parents, school staff, local officials, and administrative workers.
The group's tailored approach, which combines psychological lures and region-specific profiling, underscores its intent to secure sensitive data for North Korea as tensions between the two nations persist. Today, South Korea began removing loudspeakers at the North Korean border.
Kimsuky’s Recent Activity
Similar campaigns that leveraged the same lure documents were previously reported by Seqrite in April 2025, and security researcher Emmy Byrne further supported the attribution to the Kimsuky threat group via related samples identified in March 2025.
In February 2025, TechNadu reported on a Kimsuky phishing scheme that impersonated South Korean officials.