Jabber Zeus Developer ‘MrICQ’ in US Custody After Extradition from Italy
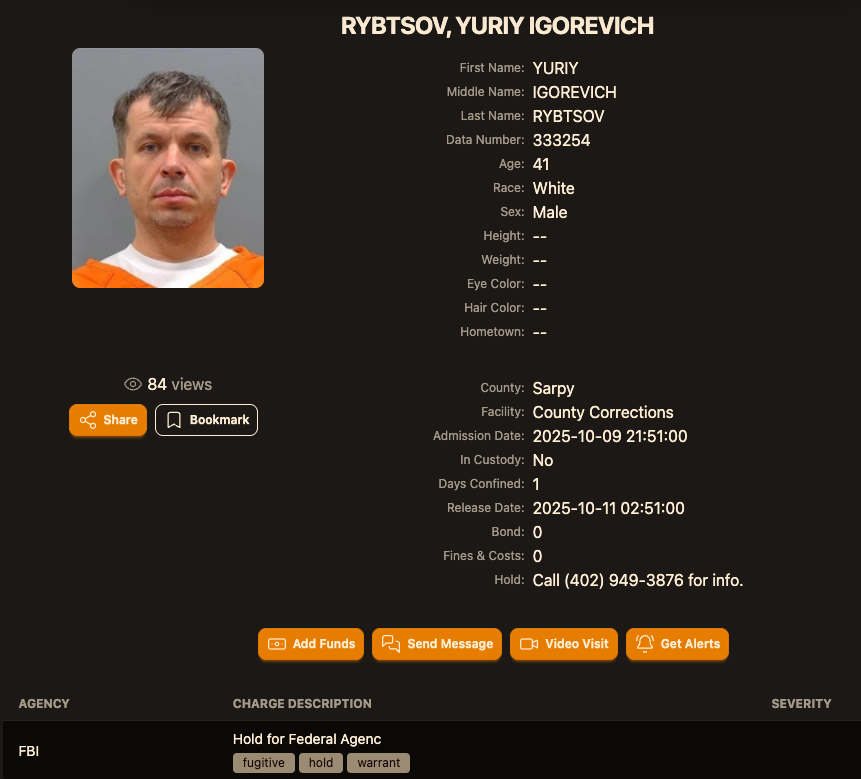
- Key Arrest: Ukrainian national Yuriy Igorevich Rybtsov, known by the alias “MrICQ,” has been extradited from Italy and is now in U.S. custody.
- Group Affiliation: Rybtsov is an alleged developer for the “Jabber Zeus” cybercrime group, a prolific gang known for stealing tens of millions from U.S. businesses.
- Malware Used: The group utilized a customized version of the infamous Zeus banking trojan to steal banking credentials and one-time passcodes.
A Ukrainian man indicted over a decade ago for his role in a sophisticated cybercrime operation has been arrested and extradited to the United States. Yuriy Igorevich Rybtsov, also known as “MrICQ,” was a key developer for the Jabber Zeus crew.
Rybtsov was arrested in Italy and, after a failed appeal against his extradition in April 2025, he arrived in Nebraska on October 9 to face charges.
The Jabber Zeus Operation and 'MrICQ's' Role
The Jabber Zeus group was notorious for its pioneering use of man-in-the-browser attacks. Their custom trojan would intercept banking credentials and send an instant message via Jabber each time a victim entered a one-time passcode (OTP).
According to a 2012 indictment, Rybtsov, 41, handled these incoming notifications and played a crucial part in laundering the proceeds through electronic currency exchanges. The Jabber Zeus coder, now arrested, faces justice as part of this long-running cybercrime crackdown.
The group’s leader, Vyacheslav “Tank” Penchukov, was arrested in 2022 and sentenced to 18 years in prison. The Zeus cybercriminal group has also been linked to two FBI-wanted Russians, Evgeniy Bogachev and Maksim Yakubets (alleged leader of Evil Corp), for whom the U.S. government offers rewards of $3 million and $5 million, respectively.
The FBI identified Zeus members by analyzing their Jabber chat messages from a seized U.S.-based server in 2010.
The group used a highly modified version of the Zeus banking trojan to steal tens of millions of dollars from small and mid-sized businesses, which also included a custom Backconnect component.
“The Jabber Zeus crew were literally connecting to the victim’s bank account from the victim’s IP address, or from the remote control function and by fully emulating the device,” Lawrence Baldwin, founder of threat intelligence company myNetWatchman, recently told KrebsOnSecurity.
“That trojan was like a hot knife through butter of what everyone thought was state-of-the-art secure online banking at the time.”
Implications of a High-Profile Cybercrime Takedown
The Jabber Zeus operation was a forerunner in sophisticated financial fraud, utilizing custom tools like "Leprechaun" to isolate high-value commercial accounts protected by two-factor authentication.
The successful extradition of MrICQ to U.S. custody demonstrates the persistent, long-term efforts by agencies like the FBI to bring key figures in the global cybercrime ecosystem to account, regardless of how much time has passed.
A few days ago, the Meduza Infostealer developers were arrested in a Russian authorities crackdown.