Iranian Threat Group Emennet Pasargad’s WezRat Malware Displays Improved Capabilities
- Emennet Pasargad continues to enhance the malware it deploys in Israeli campaigns aimed at exfiltrating information.
- The newest version of the gang’s custom modular infostealer has upload, keylogging, screenshot, and cookie exfiltration capabilities.
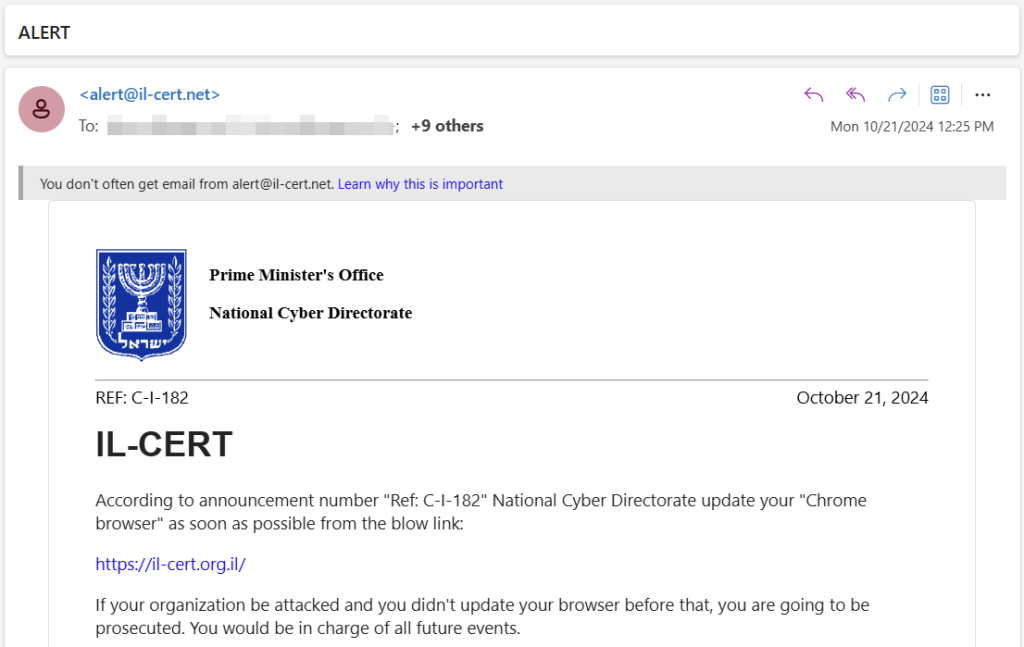
- The infostealer is disseminated via phishing emails masquerading as communications from the Israeli National Cybersecurity Directorate.
The Iranian threat group Emennet Pasargad has enhanced its notorious malware. The newest version of the custom modular infostealer dubbed WezRat by Check Point Research can execute commands, take screenshots, upload files, perform keylogging, and steal clipboard content and cookie files.
This evolution has prompted a joint Cyber Security Advisory from the FBI, the U.S. Department of the Treasury, and the Israeli National Cybersecurity Directorate (INCD), attributing this malware to the Iranian entity. Known for its audacious cyber operations across the U.S., France, Sweden, and Israel, this group continues to pose significant threats to global cybersecurity.
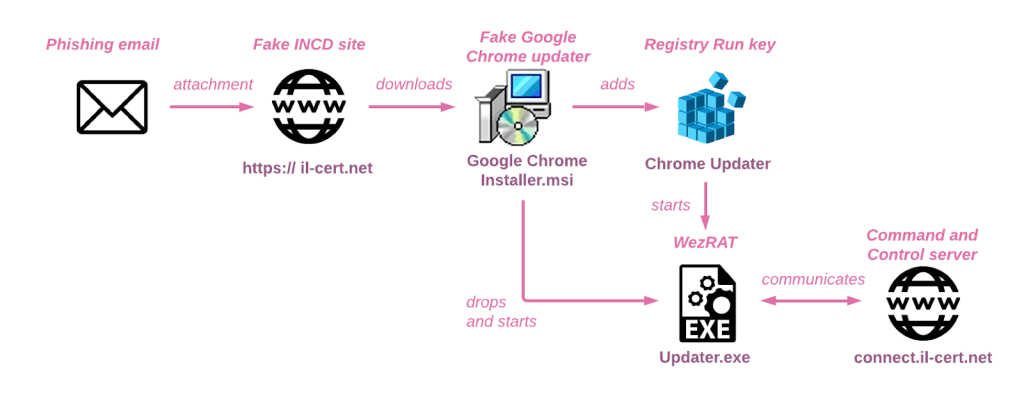
The most recent campaign targeted multiple Israeli organizations through emails masquerading as communications from the INCD. These phishing attempts included a false alert about the urgent necessity to update their Chrome browser.
Victims who clicked the link were redirected from the legitimate INCD site to a fake one, leading to the download of a file containing both the genuine Google Chrome installer and a hidden backdoor. This backdoor execution, stealthily named "Chrome Updater," ensured continued access for attackers.
The CPR report says WezRat's new version further obscures its malicious activities by downloading additional modules from the command and control (C&C) server as DLL files, which reduces suspicion surrounding its primary component.
Further analysis has uncovered partial source code for the backend, indicating that separate groups may handle the malware's development and operational deployment.
This distinct separation of development and operational functions within the organization highlights a sophisticated structure behind WezRat, where, typically, a single entity would manage both aspects.
Recently, Iranian government-backed cyber espionage group MuddyWater was seen deploying a new malware campaign aimed at Israeli organizations. The phishing operation used PDF-embedded URLs that download malware, with lures like invitations to webinars.