How Iranian Actors Targeted Aerospace Defense Contractor Through a Fake Social Media Persona
- Iranian actors have been exchanging messages with targets on social media for months before they moved to drop malware.
- The hackers also sent several innocuous files via email to establish a relationship of trust with the victim.
- Facebook has banned the fake accounts from its platform, but the hackers could easily return through new ones.
The Iranian state-supported group tracked as ‘TA456’, or otherwise known as ‘Tortoishell,’ was recently caught by Facebook trying to trick American military personnel and contractors in the defense and aerospace industries and had their fake accounts banned. Proofpoint now has more details about how exactly the actors operated, what accounts they used, and what malware they dropped onto their targets’ machines.
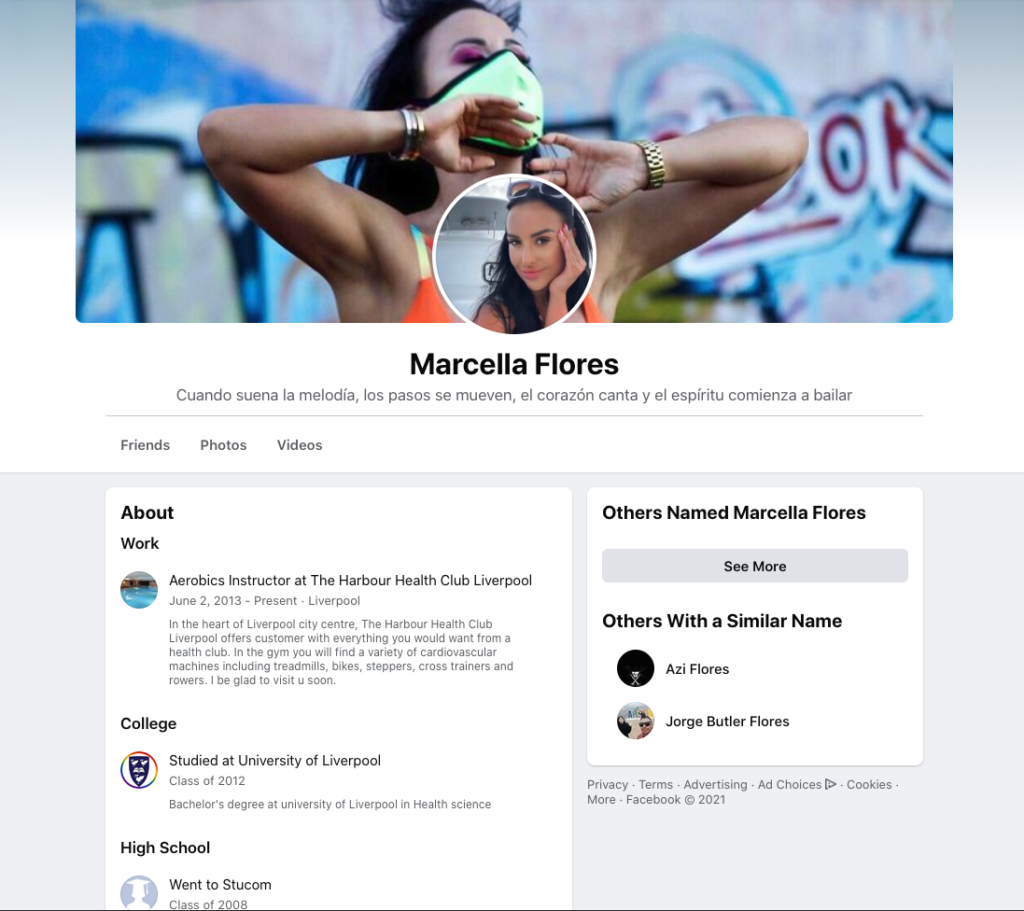
As the researchers explain, TA456’s operation took several years to unfold, as the hackers moved with patience to win the trust of their targets. One of the fake aliases used on Facebook was using the name “Marcella (Marcy) Flores,” pretending to be an aerobics instructor in Liverpool. “Marcella” was friends with a large number of defense contractor employees who were located quite far from Liverpool, UK, so for those looking into the signs of fraud, there were clearly some inexplicable red flags.
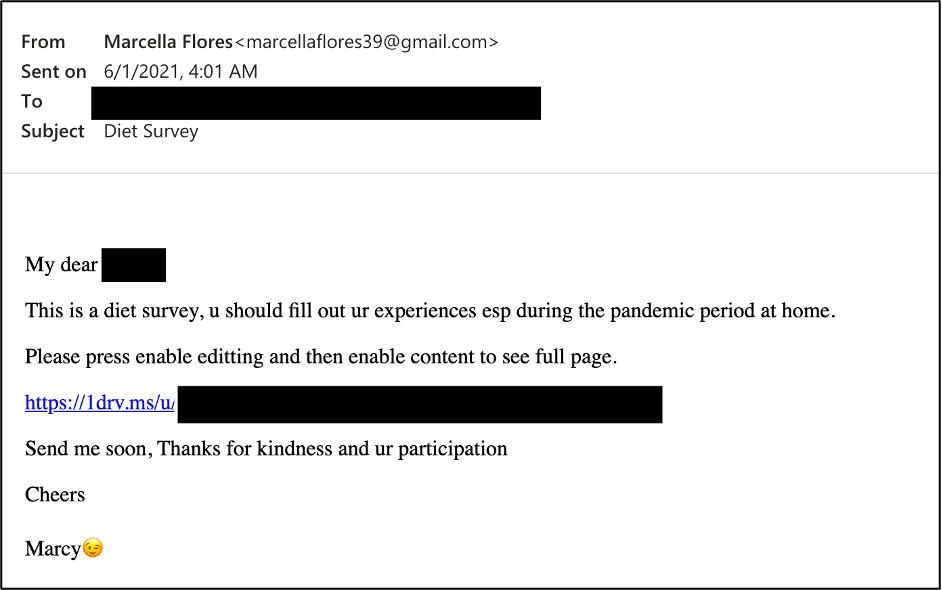
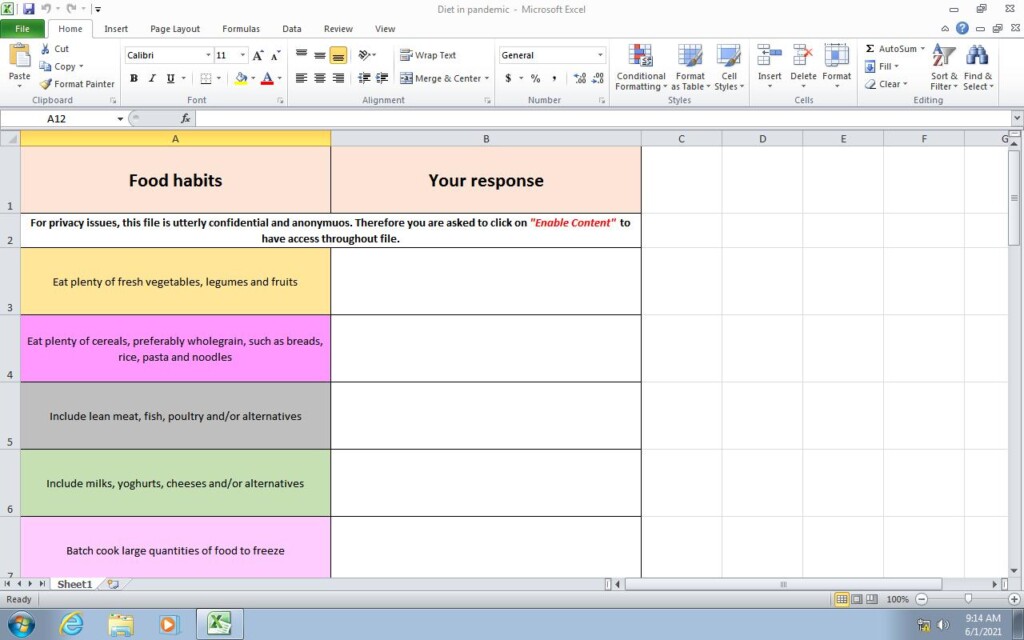
“Marchella” used a Gmail account to send the targets generally benign messages like diet plans, photographs, fitness programs, videos, etc. This went on for months without attempting to drop anything nasty to the target so that the rapport between the actors and the victim would grow strong. At some point, “Marcy” sent a OneDrive URL that was masked as a diet survey but was, in reality, a macro-ridden Excel.
The file requested the user to enable content in order of its functions to activate, and if the victim did so, ‘LEMPO’ would be dropped. 'LEMPO' is a simple yet very effective plaintext stealer that adds a registry key on Windows and initiates upon user login to the OS. The malware can collect the following information from the infected system:
- Date and time
- Computer and usernames
- System information via WMIC os, sysaccount, environment, and computer system commands
- Antivirus products located in the “SecurityCenter2” path
- Drives
- Tasklist
- Software and version
- Net users and user details
- Usernames and passwords found through “findstr” for “user”, “pass” and “vpn”
Once the above are gathered in a “Logs.txt” and packaged into a “Logs.zip” file, it is exfiltrated over SMTPS on port 465 using hardcoded credentials with MS CDO. 30 seconds later, both files are deleted from the system. The malware also connects via HTTP POST to showip[.]net. Prior to this, LEMPO performs a simple connectivity check to ford[.]com.
‘Tortoishell’ may have been caught in action this time, but it came after months of operation and only suffered account bans. This means that they can easily return to their regular trickery through new accounts, which is something to keep in mind if you’re working for a defense contractor.