IoT Botnet Aisuru Hits KrebsOnSecurity Website With Near-Record DDoS
- Security researcher Brian Krebs revealed that his website was the target of a massive DDoS.
- IoT botnet Aisuru targeted KrebsOnSecurity, with the attack reaching 6.3 Tbps.
- Investigations link the botnet’s management to individuals operating under the alias Forky.
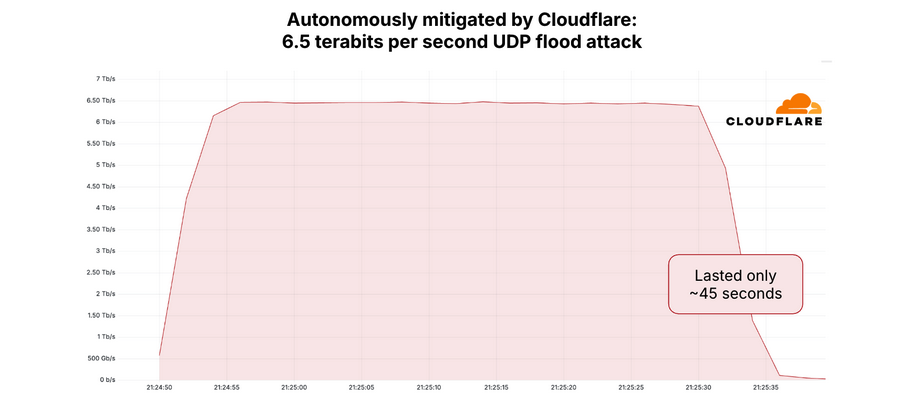
A near-record distributed denial-of-service (DDoS) attack struck KrebsOnSecurity last week, reaching over 6.3 terabits per second (Tbps) and underscoring a new escalation in cyber threat capabilities.
This brief but intense event showcases the growing prowess of modern botnets, capable of overwhelming even the most fortified network infrastructures.
The attack lasted under a minute and was orchestrated through a formidable new Internet of Things (IoT) botnet called Aisuru.
This global threat marshals hundreds of thousands of compromised devices—including routers and digital video recorders—exploited via default credentials and unpatched vulnerabilities.
Security experts at Google, responsible for mitigating the attack via Project Shield, confirmed it as the largest incident they have managed to date and the second highest globally, trailing only a 6.5 Tbps attack neutralized by Cloudflare in April.
Aisuru, also known as Airashi, first surfaced in 2024 and quickly demonstrated its power during an attack on a major gaming platform. After a period of dormancy, it reemerged equipped with zero-day exploits, including one targeting Cambium Networks cnPilot routers.
The botnet is being openly marketed on Telegram, where operators rent out its capabilities in subscription tiers—from $150 per day to $600 per week; attacks can reach up to two Tbps.
Investigations link the botnet’s management to individuals operating under the alias “Forky,” who also run Botshield, a purported DDoS mitigation and hosting business registered in the U.K.
Although Forky denies orchestrating the recent attack on KrebsOnSecurity, he admits involvement in developing and marketing Aisuru.